BOOK THIS SPACE FOR AD
ARTICLE ADAn analysis of second-quarter malware trends shows that threats are becoming stealthier.
A full 91.5 percent of malware was delivered using HTTPS-encrypted connections in the second quarter, researchers said, making attacks more evasive.
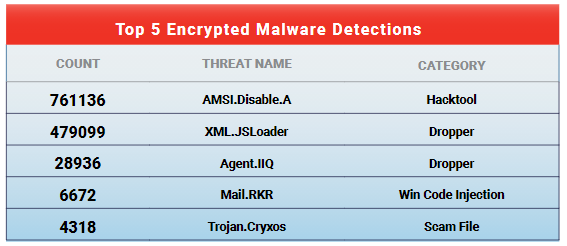
That’s according to WatchGuard Technologies’ latest report on findings within its telemetry, which also found that these detections come primarily from two malware families: AMSI.Disable.A ,which was first spotted in Q1; and the older malware known as XML.JSLoader. Together these make up more than 90 percent of detections over HTTPS and more than 12 percent of total detections, according to the report.
For its part, AMSI.Disable.A is a recently developed malware that uses PowerShell tools to bypass security protections.
“This malware family uses PowerShell tools to exploit various vulnerabilities in Windows,” according to the firm. “But what makes it especially interesting is its evasive technique. WatchGuard found that AMSI.Disable.A wields code capable of disabling the Antimalware Scan Interface (AMSI) in PowerShell, allowing it to bypass script security checks with its malware payload undetected.”
Source: WatchGuard.
The report also noted that the stats mean that any organization that is not examining encrypted HTTPS traffic at the perimeter is missing blocking nine out of 10 malware infection attempts.
“Unfortunately, not many administrators configure HTTPS inspection to peer into these connections,” according to the report, issued Monday. “The ramifications of this lack of visibility are even more serious this quarter.”

Source: WatchGuard.
WatchGuard’s report also identified other malware trends for the quarter, including growth in fileless threats, which is a category into which AMSI.Disable.A also falls. In just the first six months of 2021, malware detections originating from scripting engines like PowerShell had already reached 80 percent of last year’s total script-initiated attack volume. At its current rate, 2021 fileless malware detections are on track to double in volume year over year.
“Malicious PowerShell scripts have been known to hide in the memory of the computer and already use legitimate tools, binaries and libraries that come installed on most Windows systems,” explained the report. “That is why attackers have increased their use of this technique, called living off the land (LotL) attacks. Using these methods, a vaporworm might make its script invisible to many antivirus systems that don’t inspect the scripts or systems’ memory.”
Ransomware Soars
In terms of styles of malware, ransomware attacks are continuing apace, the firm noted, and are on pace to spike in volume a full 150 percent this year compared with 2020.
“While total ransomware detections on the endpoint were on a downward trajectory from 2018 through 2020, that trend broke in the first half of 2021, as the six-month total finished just shy of the full-year total for 2020,” according to the report.
The spike dovetails with findings from other security firms, including SonicWall, which in August found that global attack volume for ransomware had increased by 151 percent for the first six months of the year as compared with the year-ago half. From a hard-number perspective, the ransomware scourge hit a staggering 304.7 million attempted attacks within SonicWall Capture Labs’ telemetry. To put that in perspective, the firm logged 304.6 million ransomware attempts for the entirety of 2020.
Check out our free upcoming live and on-demand webinar events – unique, dynamic discussions with cybersecurity experts and the Threatpost community.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·