A total of 158 privacy and security issues have been identified in 58 Android stalkware apps from various vendors that could enable a malicious actor to take control of a victim's device, hijack a stalker's account, intercept data, achieve remote code execution, and even frame the victim by uploading fabricated evidence.
The new findings, which come from an analysis of 86 stalkerware apps for the Android platform undertaken by Slovak cybersecurity firm ESET, highlight the unintended consequences of a practice that's not only unethical but in the process could also expose private and intimate information of the victims and leave them at risk of cyberattacks and fraud.
"Since there could be a close relationship between stalker and victim, the stalker's private information could also be exposed," ESET researcher Lukas Stefanko said in a Monday write-up. "During our research, we identified that some stalkerware keeps information about the stalkers using the app and gathered their victims' data on a server, even after the stalkers requested the data's deletion."
To date, only six vendors have fixed the issues that were identified in their apps. 44 vendors chose not to acknowledge the disclosures, while seven others claimed they intend to address the flaws in an upcoming update. "One vendor decided not to fix the reported issues," Stefanko said.
Stalkerware, also called spouseware or spyware, refers to invasive software that enables individuals to remotely monitor the activities on another user's device without the individual's consent with the goal of facilitating intimate partner surveillance, harassment, abuse, stalking, and violence.
Based on telemetry data gathered by ESET, Android spyware detection surged by 48% in 2020 when compared to 2019, which witnessed a five-fold increase in stalkerware detections from 2018. Although Google put in place restrictions on advertising for spyware and surveillance technology, stalkerware providers have managed to slip past such defenses by masquerading as child, employee, or women safety apps.
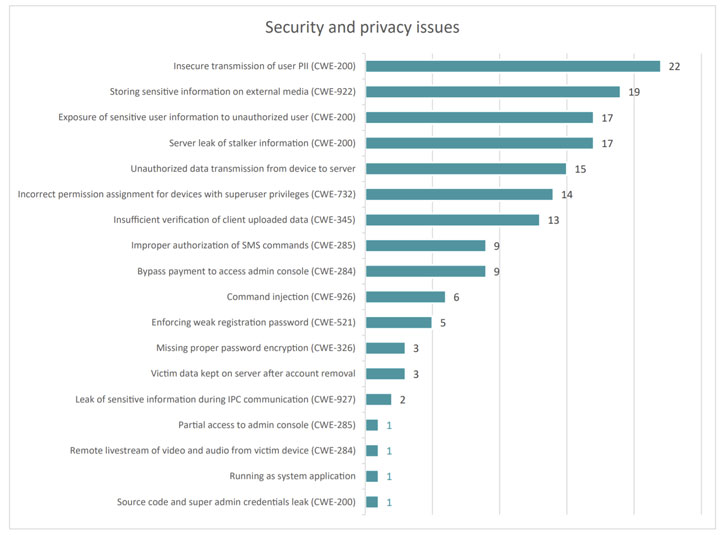
Among the most prevalent issues uncovered are as follows —
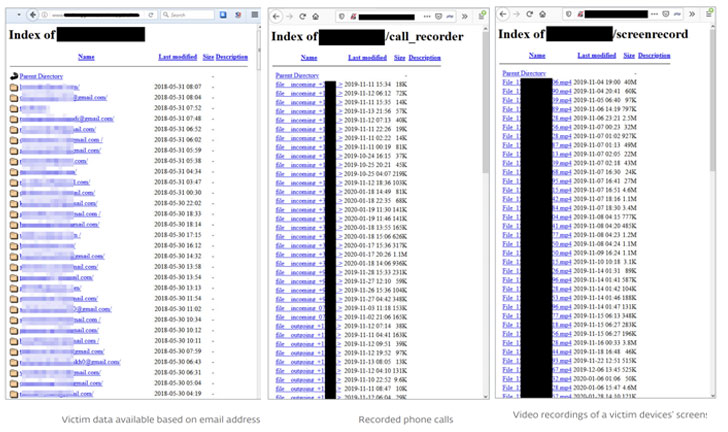
Apps from nine different vendors are based on an open-source Android spyware called Droid-Watcher, with one vendor using a Metasploit payload as a monitoring app. Some apps have hardcoded license keys in cleartext, allowing easy theft of software. Other apps analyzed by ESET disable notifications and Google Play Protect to weaken the device's security intentionally. 22 apps transmit users' personally identifiable information over an unencrypted connection to the stalkerware server, thereby permitting an adversary on the same network to stage a man-in-the-middle attack and change transmitted data. 19 apps store sensitive information, such as keystroke logs, photos, recorded phone calls, and audio, calendar events, browser history, contact lists, on external media. This could allow any third-party app with access to external storage to read these files without additional permission. 17 apps expose user information stored in the servers to unauthorized users without requiring any authentication, granting the attacker full access to call logs, photos, email addresses, IP logs, IMEI numbers, phone numbers, Facebook and WhatsApp messages, and GPS locations. 17 apps leak client information through their servers, thus allowing a victim to retrieve information about the stalker using the device's IMEI number and creating an "opportunity to brute-force device IDs and dump all the stalkerware clients." 15 apps transmit unauthorized data from a device to the servers immediately upon installation and even before the stalker registers and sets up an account. 13 apps have insufficient verification protections for uploaded data from a victim phone, with the apps solely relying on IMEI numbers for identifying the device during communications.The last issue is also concerning in that it be exploited by an attacker to intercept and falsify data. "With appropriate permission, those identifiers can be easily extracted by other apps installed on a device and could then be used to upload fabricated text messages, photos and phone calls, and other fictitious data to the server, to frame victims or make their lives more difficult," Stefanko said.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
222
3 years ago
222 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·