An ongoing cyber-espionage operation with suspected ties to China has been found targeting a Southeast Asian government to deploy spyware on Windows systems while staying under the radar for more than three years.
"In this campaign, the attackers utilized the set of Microsoft Office exploits and loaders with anti-analysis and anti-debugging techniques to install a previously unknown backdoor on victim's machines," researchers from Check Point Research said in a report published today.
The infection chain works by sending decoy documents, impersonating other entities within the government, to multiple members of the Ministry of Foreign Affairs, which, when opened, retrieves a next-stage payload from the attacker's server that contains an encrypted downloader. The downloader, in turn, gathers and exfiltrates system information to a remote server that subsequently responds back with a shellcode loader.
The use of weaponized copies of legitimate-looking official documents also suggests that "the attackers first had to attack another department within the targeted state, stealing and weaponizing documents for use against the Ministry of Foreign Affairs," said Lotem Finkelsteen, head of threat intelligence at Check Point.
The last link in the attack involves the loader establishing a connection with the remote server to download, decrypt, and execute an implant dubbed "VictoryDll_x86.dll" that's capable of performing file operations, capture screenshots, create and terminate processes, and even shut down the infected machine.
Check Point said the adversary placed significant effort into hiding their activity by changing its infrastructure multiple times since its development in 2017, with the backdoor receiving its own fair share of revisions to make it more resilient to analysis and decrease the detection rates at each stage.
The long-running campaign has been linked with "medium to high confidence" to a Chinese advanced persistent threat (APT) group it calls "SharpPanda" based on test versions of the backdoor dating back to 2018 that were uploaded to VirusTotal from China and the actor's use of Royal Road RTF weaponizer, a tool that been used in campaigns attributed to well-known Chinese threat groups since late 2018.
Several other clues point to this conclusion, including the fact that the command-and-control (C2) servers returned payloads only between 01:00 and 08:00 UTC, which the researchers suspect are the working hours in the attackers' country, and that no payloads were returned by the C2 servers between May 1 and 5 — even during working hours — which coincides with the Labor Day holidays in China.
The development is yet another indication that multiple cyberthreat groups believed to be working in support of China's long-term economic interests are continuing to hammer away at networks belonging to governments and organizations, while simultaneously spending a great deal of time refining the tools in their arsenal in order to hide their intrusions.
"All the evidence points to the fact that we are dealing with a highly-organized operation that placed significant effort into remaining under the radar," Finkelsteen said. "All in all, the attackers, who we believe to be a Chinese threat group, were very systematic in their approach."
"The attackers are not only interested in cold data, but also what is happening on a target's personal computer at any moment, resulting in live espionage. Although we were able to block the surveillance operation for the Southeast Asian government described, it's possible that the threat group is using its new cyber espionage weapon on other targets around the world," he added.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
176
3 years ago
176 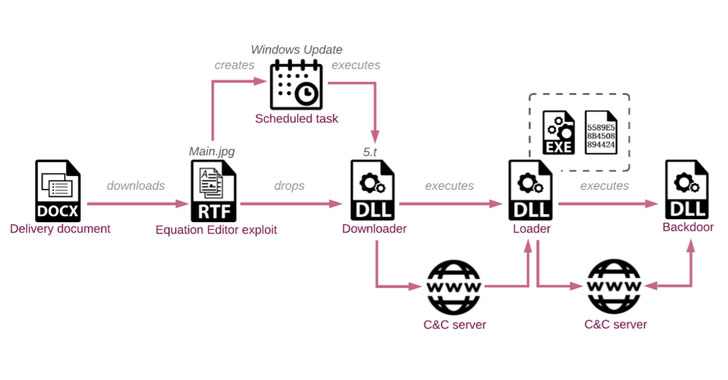
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·