BOOK THIS SPACE FOR AD
ARTICLE AD
Hey Cyberpunks, Ethical Kaps here, I’m back again with another powerful article. I hope you all are doing great in your life. Today we are going to talk about JSON Web Token. So without wasting any time let’s get straight into it.
Note: I will keep the topic as simple as possible and try to explain it in layman’s language. So that you’ll be able to grasp the roots of the vulnerability, and find that bug in your targets to make them more secure and earn bounties.
I will use abbreviation for JSON Web Token as JWT.
Simply understand this like, A Token which is used to securely transmit the information between parties as a JSON Object. It is also used for Authorization.
I think this definition is Cool and that’s all you need to know at this point. Do not worry at all you’ll grasp every aspect of it.✌ I’ll provide you the link further in this article in case you want to dive deep into the definition.
JWT follows the following structure :-
Base64(Header).Base64(Data).Base64(Signature). JWT are storage mechanism for data. It provides security mechanism as :-
EncryptionSignatureSignature Methods used to ensure Integrity of JWT :-
RSAHMACElliptic curvesNoneWhy I have highlighted the NONE Algorithm? You’ll get to know in a while when I’ll share the real time example of this vulnerability. I hope till now you have the basic Idea about what exactly is this JWT. Though this is enough for you to hunt this Vulnerability but still If you want to explore more about JSON Web Token. Then you can visit here.
Enough Kaps, 😒 show me some real world example in detail.
I am going to show you an practical example of how I did it in stepwise manner. You’ll be able to hunt it too.
Step 1:- I logged into the application and took the request onto Burp suite. As you can see I am currently logged in as ethicalkaps.

I noticed that auth= value is interesting as it follows the JWT Structure which we already discussed above.
Step 2:- I then tried to Decode the value and send that to Decoder.

Step 3:- I noticed that the algorithm used here was HS256 for encryption. Also login parameter was reflecting the username. So I thought to manipulate both of them to another value. Like :- HS256 -> None & ethicalkaps -> admin. To notice if anything happens.🤔
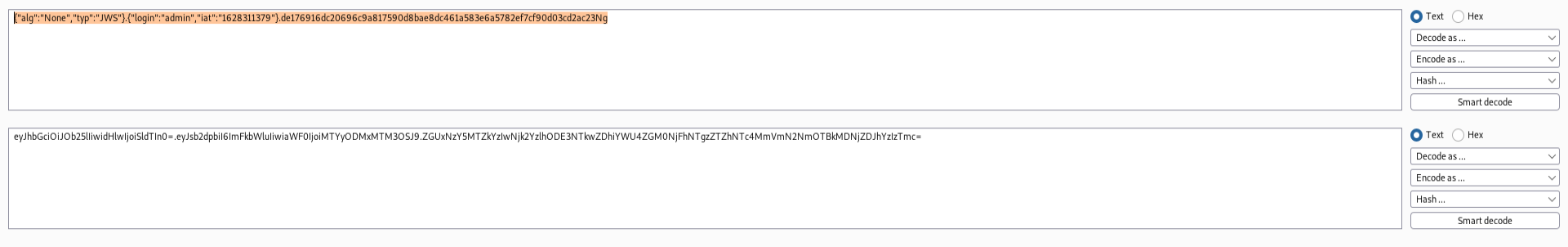
Step 4:- I then copied the whole (manipulated)Base 64 value and pasted in the cookie value. I noticed that the response was 200 OK. 😍

Step 5:- Though the response was 200 OK. But Unfortunately I was not able to log in to the account of admin. So I thought to remove the Signature of JWT.

Step 6:- Boooommmm!!!! I was successfully able to exploit and takeover the account of admin.😍✌
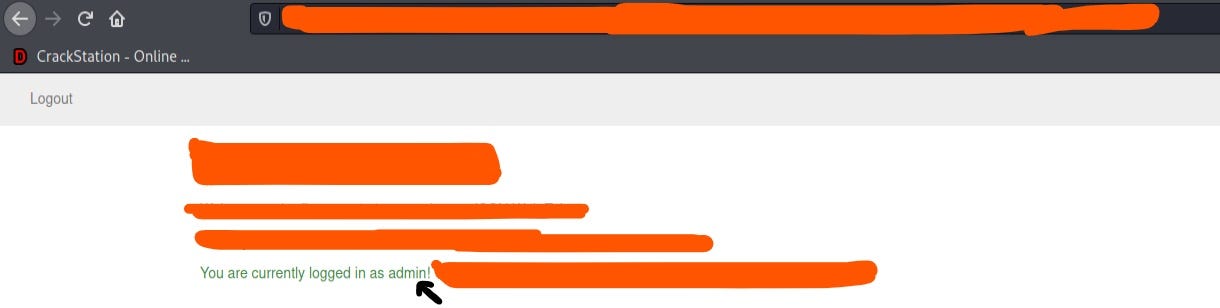
So this was it!!! That’s how I was able to manage to takeover the account of admin. OR you can say that’s how ethical kaps turned himself to admin by escalating the privileges.😅
Hackers!!!! keep your eye open and consider this option of hunting JWT while testing. If you want to decode any JWT token then don’t forget to use https://jwt.io/ as your one stop Solution. 😁
So, this is it for this Article I hope you enjoyed it. I will come back to you with another helpful writeup. Till then, take care and Keep Hunting for good. Keep Digging and learning new stuffs.😍
If you like the content then, you can support me over here :- @buymeacoffee.com/ethicalkaps
See you in the next Article. Until then Cherish your life. Peace!
You can Follow me on Twitter, on Spotify to listen my writeups(😁) and on Instagram.
If you enjoyed this story, please click the 👏 button as many time as you want and share to help others find it! Feel free to leave a comment below.
.png)
 3 years ago
174
3 years ago
174 













 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·