BOOK THIS SPACE FOR AD
ARTICLE ADWhat Is Sub domain Takeover: When an attacker is able to gain control of a company’s subdomain hosted on a cloud service such as AWS, github etc. because of the DNS entries pointing to that service is not being removed. This allows attacker to set up a phishing page on that sub-domain or serve malicious content.

Disadvantage:
· Attacker can misuse company’s reputation by send phishing emails from the legitimate domain, perform XSS, phishing, stealing cookies and more.
What is S3(Simple Storage Service): S3 buckets are scalable , high speed , data availability web based cloud storage service designed to use read private, public content or upload content to the buckets. You can also host your webpage on it and can render the contents of this on any of your subdomain using the CNAME DNS entry
Subdomain takeover in amazon s3: Each bucket pointing to a specific domain or subdomain. So sometimes, when s3 buckets is no longer in use customer delete them from their Amazon account, but forgets to remove the DNS entry pointing to that subdomain it may escalate to a subdomain takeover because amazon allow non existing bucket names to be claimed again on any other account.
Exploitation:
· We have s3 bucket located here (http://test.s3-website-south-.amazonaws.com) and this URL is getting rendered to this domain https://blessedgupta.online. This bucket contain data of https://blessedgupta.online
· The blessedgupta.online is using a CNAME entry to render the data of the S3 bucket to his domain.
· Later she wants to move to another services so she delete the bucket from her amazon account. But forgets to remove the CNAME from DNS entries
· Now attacker creates a bucket with same name since CNAME entry has not been removed from the blessedgupta.online the data of the newly created will starts rendering on the blessedgupta.online.
This whole process known as Subdomain takeover and attacker can serve malicious contents to the users.
Basic Identification: By using any subdomain enumeration tool like Sublist3r or Knockpy we can get all the subdomain of a website. There might be some of the subdomains which they have used in early phase but not using as of now. These should be the main targets. In order to find out the CNAMe enter of any domain open the terminal and type this command.
Dig cname <Enter any URL>

This command will shows the CNAME of a domain/subdomain. You can also use any online DNS resolver tools to find that as well.
Now in order to check whether there is subdomain takeover or not you have to use the URL in the CNAME entry to access the website.
After visiting the url, there are 2 types of response which you will see in the browser
· Access Denied: It simply means subdomain is not available for takeover
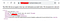
· NoSuchBucket: It simply means that the user had delete the bucket from his account and you can claim that on the amazon.
Note: For more details you can check my github repository “https://github.com/guptabless/unclaim-s3-finder/blob/master/bucket-takeover.py” .
How it Works: Sub-domain takeover is not only limited to CNAME records it also includes NS, MX and even A records.
A web browser has implicitly trust to the DNS functionality means when attacker gets control over DNS records, all web browser security measurements are easily by passed.
RISK and Mitigation
· Many organizations do not audit their configuration on a regular basis.
· No standardized process for adding, changing or removing entries from their DNS zone file.
· Whenever organization discounting or terminating a service will safely remove its DNS records.
.png)
 4 years ago
233
4 years ago
233 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·