BOOK THIS SPACE FOR AD
ARTICLE AD
A Facebook malvertising campaign targets users searching for AI image editing tools and steals their credentials by tricking them into installing fake apps that mimic legitimate software.
The attackers exploit the popularity of AI-driven image-generation tools by creating malicious websites that closely resemble legitimate services and trick potential victims into infecting themselves with information stealer malware, as Trend Micro researchers who analyzed the campaign found.
The attacks start with phishing messages sent to Facebook page owners or administrators, which will send them to fake account protection pages designed to trick them into providing their login information.
After stealing their credentials, the threat actors hijack their accounts, take control of their pages, publish malicious social media posts, and promote them via paid advertising.
"We discovered a malvertising campaign involving a threat actor that steals social media pages (typically related to photography), changing their names to make them seem connected to popular AI photo editors," said Trend Micro threat researcher Jaromir Horejsi.
"The threat actor then creates malicious posts with links to fake websites made to resemble the actual website of the legitimate photo editor. To increase traffic, the perpetrator then boosts the malicious posts via paid ads."
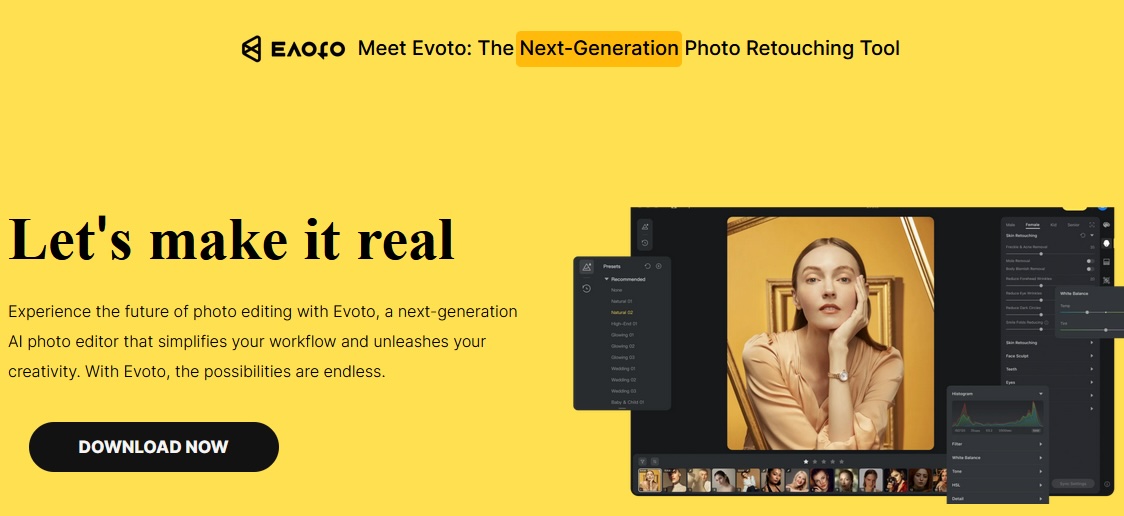 Fake AI photo editor website (Trend Micro)
Fake AI photo editor website (Trend Micro)Facebook users who click the URL promoted in the malicious ad are sent to a fake web page impersonating legitimate AI photo editing and generating software, where they are prompted to download and install a software package.
However, instead of AI image editing software, the victims install the legitimate ITarian remote desktop tool configured to launch a downloader that automatically deploys the Lumma Stealer malware.
The malware then quietly infiltrates their system, allowing the attackers to collect and exfiltrate sensitive information like credentials, cryptocurrency wallet files, browser data, and password manager databases.
This data is later sold to other cybercriminals or used by the attackers to compromise the victims' online accounts, steal their money, and promote further scams.
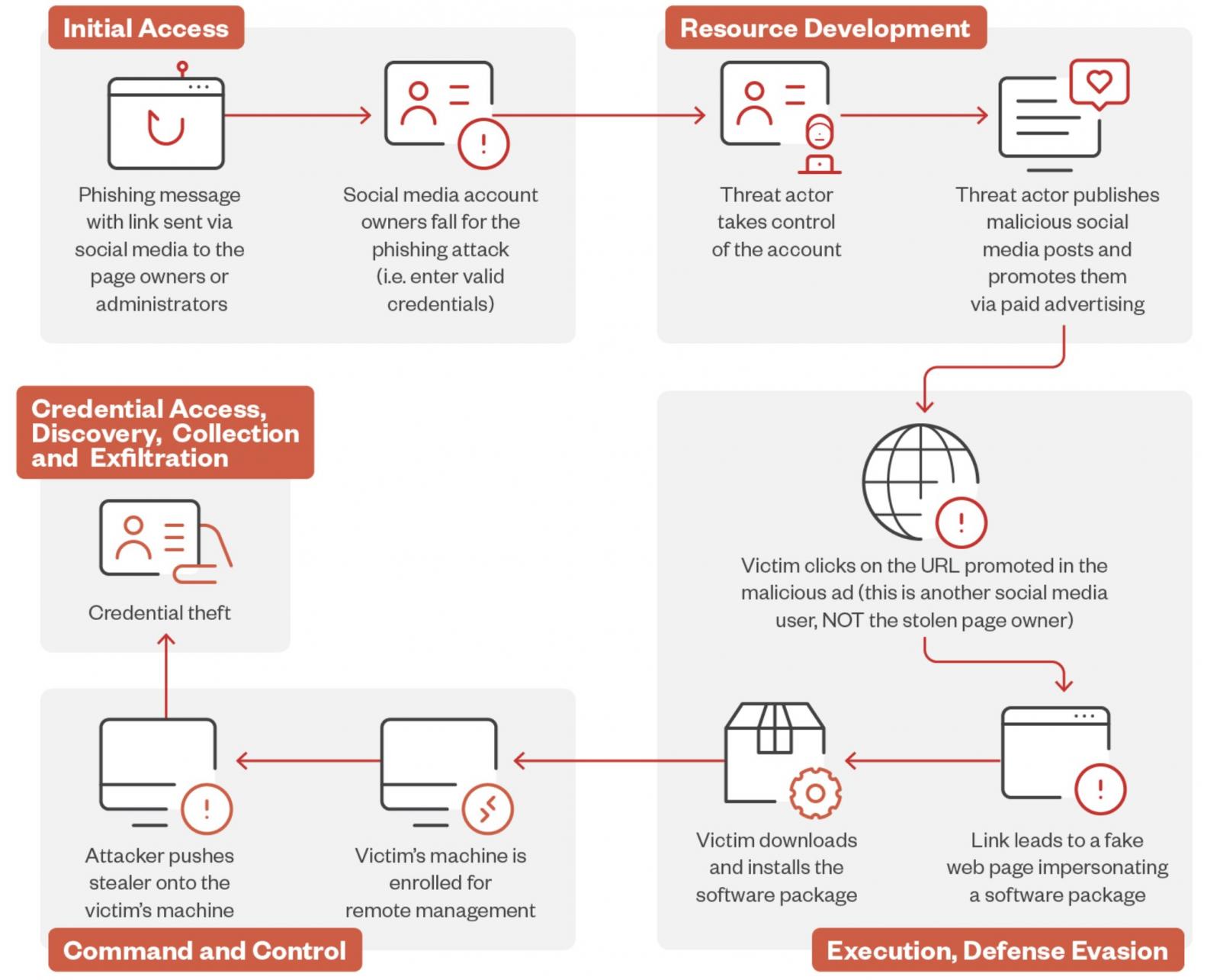 Attack flow (Trend Micro)
Attack flow (Trend Micro)"Users should enable multi-factor authentication (MFA) on all social media accounts to add an extra layer of protection against unauthorized access," Horejsi advised.
"Organizations should educate their employees on the dangers of phishing attacks and how to recognize suspicious messages and links. Users should always verify the legitimacy of links, especially those asking for personal information or login credentials."
In April, a similar Facebook malvertising campaign promoted a malicious page impersonating Midjourney to target almost 1.2 million users with the Rilide Stealer Chrome browser extension.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·