BOOK THIS SPACE FOR AD
ARTICLE ADLumma Stealer malware uses fake CAPTCHA to deceive victims. This information-stealing malware targets sensitive data like passwords and cryptocurrency details.
The Qualys Threat Research Unit (TRU) has discovered that Lumma Stealer, a malware available through a Malware-as-a-Service (MaaS) model, has evolved its tactics considerably to deceive users.
Qualys shared its findings with Hackread.com regarding an active Lumma Stealer campaign using fake CAPTCHA pages to trick users into executing a persistent payload. The attack uses multi-stage fileless techniques, making it deceptive and persistent.
Fake CAPTCHA Verification
Qualys TRU explained that users are lured to a fake CAPTCHA verification page, often through compromised legitimate software or public-facing applications. Clicking the “I’m not a robot” button triggers a malicious PowerShell command, which downloads an initial stager (malware downloader) onto the target machine. The downloaded payload is a crafted PE file with an obfuscated JavaScript code embedded within it.
What happens is that clicking the verification button triggers a Base64-encoded PowerShell script download. This script leverages the trusted Windows tool “mshta.exe” to download a remote payload disguised as a legitimate Windows tool named “Dialer.exe.” This downloaded payload is a crafted PE file with an obfuscated JavaScript code embedded within it.
Interestingly, the embedded script utilizes a technique called polyglot, where valid HTA content is concealed within executable files. When triggered, the script downloads and executes another obfuscated JavaScript code using PowerShell. This script decrypts a final payload and downloads two archives containing the actual Lumma Stealer executable (Vectirfree.exe).
Information Gathering and Evasion Techniques
Vectirfree.exe employs process hollowing, a common malware tactic, to inject its malicious code into a legitimate program like “BitLockerToGo.exe.” The malware drops files like “Killing.bat” and “Voyuer.pif” in the temporary directory that checks for and terminates antivirus processes to evade detection.
In the next stage of the attack, Lumma Stealer searches for sensitive files and data related to cryptocurrency and passwords. Stolen data is sent to a command and control (C2) server, typically using “.shop” top-level domains, to exfiltrate the stolen data.
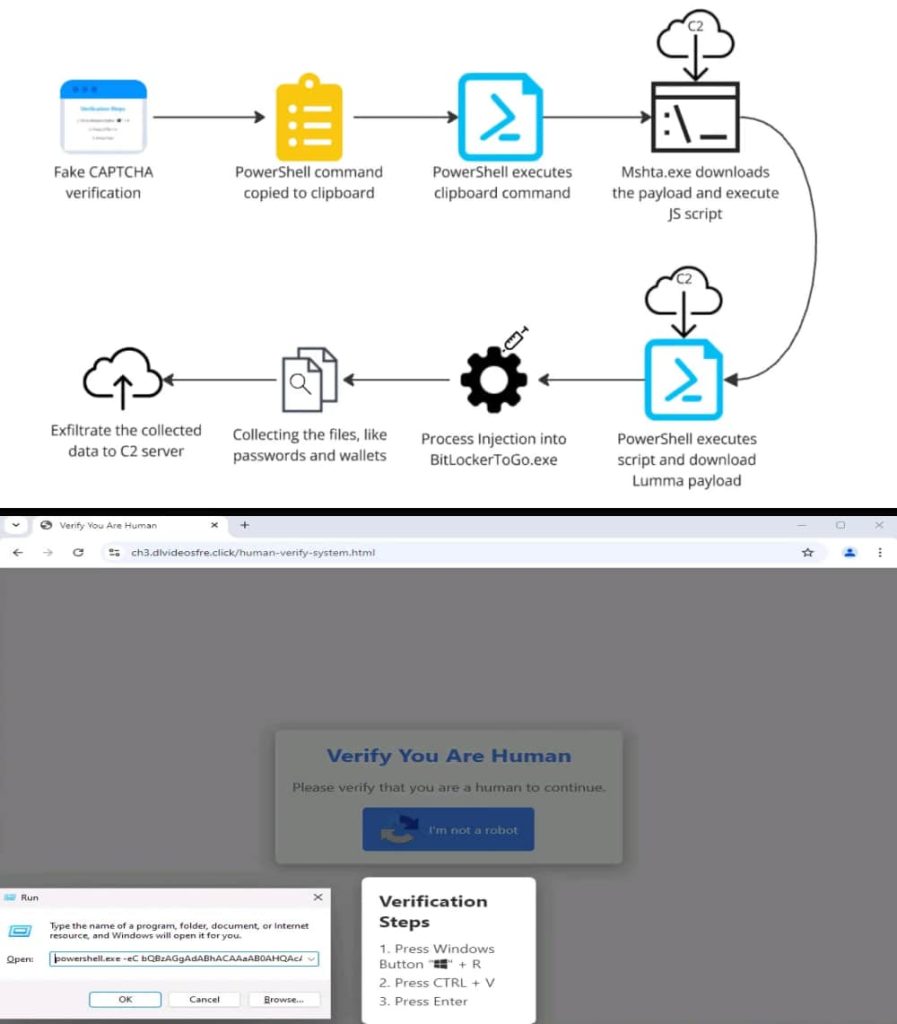 Infection chain and a fake CAPTCHA page involved in the Lumma Stealer malware campaign (Via Qualys Threat Research Unit)
Infection chain and a fake CAPTCHA page involved in the Lumma Stealer malware campaign (Via Qualys Threat Research Unit)Lumma Stealer is a fileless malware that executes directly from memory without creating permanent files. It targets sensitive data like passwords, browser information, and cryptocurrency wallet details. By using techniques like polyglot and obfuscated scripts to hinder analysis, and process hollowing to hide its malicious activity within a legitimate process, the malware presents itself as a persistent threat.
“Our analysis of its infection chain highlighted how the fileless malware exploits common tools like PowerShell and mshta.exe, as well as the critical role of embedded payloads and process injection in its operations,” researchers noted in the report.
By understanding the Lumma Stealer attack process and implementing robust security measures, organizations can effectively protect themselves against this evolving threat.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·