BOOK THIS SPACE FOR AD
ARTICLE ADA new phishing campaign uses fake CAPTCHA verification pages to trick Windows users into running malicious PowerShell commands, installing the Lumma Stealer malware and stealing sensitive information. Stay informed and protected.
Cybersecurity researchers at CloudSec have discovered a new phishing campaign that is tricking users into running malicious commands through fake human verification pages. The campaign, which primarily targets Windows users, aims to install the Lumma Stealer malware, leading to the theft of sensitive information.
How the Attack Works
Threat actors are creating phishing sites hosted on various platforms, including Amazon S3 buckets and Content Delivery Networks (CDNs). These sites mimic legitimate verification pages, such as fake Google CAPTCHA pages. When users click the “Verify” button, they are presented with unusual instructions:
Open the Run dialog (Win+R) Press Ctrl+V Hit EnterUnknown to the user, these actions execute a hidden JavaScript function that copies a base64-encoded PowerShell command to the clipboard. When the user pastes and runs the command, it downloads the Lumma Stealer malware from a remote server.
CloudSec’s report shared with Hackread.com ahead of publishing on Thursday, revealed that the downloaded malware often downloads additional malicious components, making detection and removal more difficult. While currently used to spread Lumma Stealer, this technique could be easily adapted to deliver other types of malware.
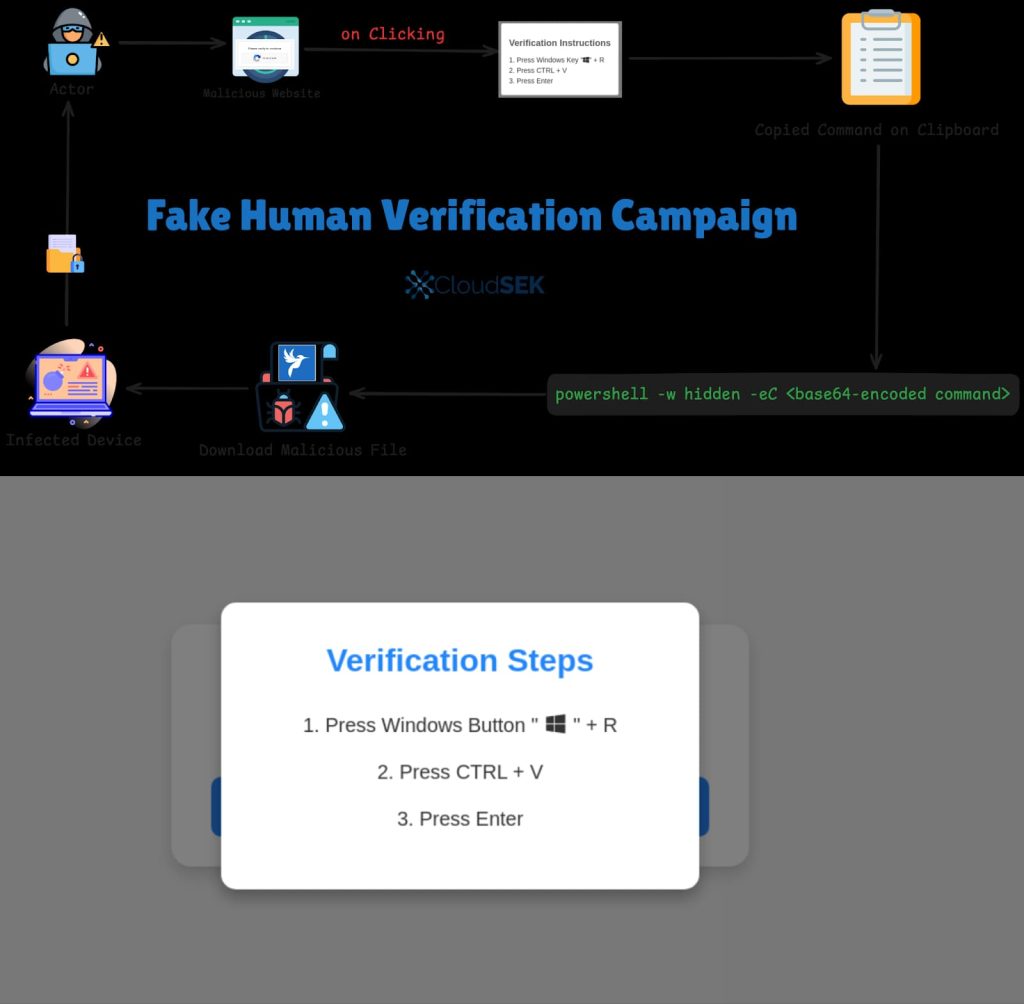 Attack flow and fake verification process triggered when the user clicks on the fake Google CAPTCHA prompt (Screenshot: CloudSec)
Attack flow and fake verification process triggered when the user clicks on the fake Google CAPTCHA prompt (Screenshot: CloudSec)For your information, the Lumma Stealer is designed to steal sensitive data from the infected device. While the specific data targeted can vary, it often includes login credentials, financial information, and personal files. This latest campaign came just days after the malware was caught disguising itself as an OnlyFans hacker tool, infecting the devices of other hackers.
In January 2024, Lumma was discovered to be spreading through cracked software distributed via compromised YouTube channels. Earlier, in November 2023, researchers had identified a new version of LummaC2, called LummaC2 v4.0, which was stealing user data using trigonometric techniques to detect human users.
I hereby confirm. https://t.co/1q4cARQLDM pic.twitter.com/GEBzqJeaSs
— Waqas (@WAK4S) December 31, 2023What Now?
Now that the new Lumma stealer infection spree has been reported, businesses and unsuspecting users need to stay alert and avoid falling for the latest fake verification scam. Here are some common-sense rules and simple yet essential tips for protection against Lumma and other similar stealers:
Educate yourself and others: Share this information with friends, family, and colleagues to raise awareness about this new threat. Be wary of unusual verification requests: Legitimate websites rarely ask users to execute commands through the “Run” dialogue box. Be suspicious of any site that makes such requests. Don’t copy and paste unknown commands: Avoid copying and pasting anything from untrusted sources, especially commands meant to be run in a terminal or command prompt. Keep your software updated: Ensure your operating system and antivirus software are up-to-date to patch known vulnerabilities. Most Important: Follow Hackread.com for the latest cybersecurity news..png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·