BOOK THIS SPACE FOR AD
ARTICLE ADSUMMARY
Phishing Scam Targets Job Seekers: Cybercriminals impersonate CrowdStrike recruiters to distribute cryptominer malware via fake job offers. Malware Delivery: Victims are tricked into downloading a malicious app from a fake CrowdStrike website, and installing XMRig to mine Monero cryptocurrency. Evasion Tactics: The malware limits CPU usage, scans for security tools, and uses startup scripts to remain undetected and persistent. Rising Fake Job Scams: Similar tactics are increasingly common, with groups like Lazarus using fake job offers to deploy malware. Safety Tips: Verify job offers through official channels, avoid unsolicited software downloads, and use endpoint protection to detect threats.Cybercriminals are deploying a tricky new phishing campaign impersonating the cybersecurity firm CrowdStrike‘s recruiters to distribute a cryptominer on unsuspecting job seekers’ devices. This malicious scheme leverages the allure of employment at a reputable cybersecurity firm to trick victims into downloading malware.
According to CrowdStrike’s blog post, the attack was detected on 7 January 2025 and began with a phishing email that appears to be part of CrowdStrike’s recruitment process. The email entices the target with the prospect of a junior developer interview and provides a link to schedule the meeting. Clicking the link directs the victim to a cleverly designed imposter website that mimics CrowdStrike’s branding.
This deceptive website offers downloadable “employee CRM applications” for both Windows and macOS users. Regardless of the chosen platform, downloading the application triggers the installation of a malicious Windows executable written in Rust. This executable acts as a downloader for XMRig, a well-known cryptominer, which starts mining Monero cryptocurrency. This privacy coin is a popular choice for cybercriminals because it is hard to trace.
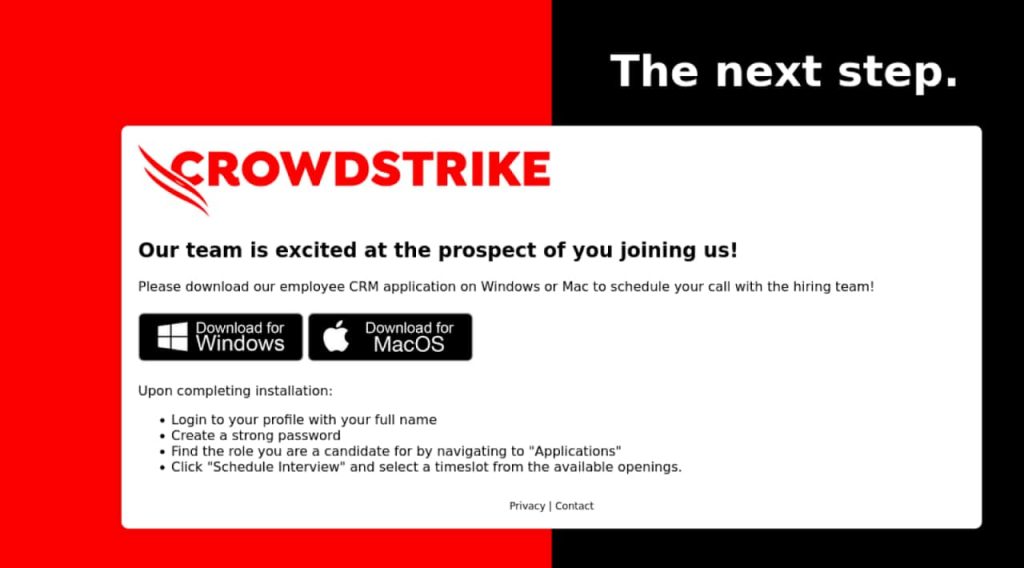 The screenshot shows the malicious phishing site containing download links for the fake CRM application (Via CrowdStrike)
The screenshot shows the malicious phishing site containing download links for the fake CRM application (Via CrowdStrike)The executable is designed to evade detection by scanning the system’s processes for malware analysis tools or virtualization software, verifying the presence of at least two CPU cores, and checking for debuggers. If successful, it displays a fake error message to lull the victim into a false sense of security, while downloading additional payloads to establish persistence on the infected device and initiate the XMRig cryptomining process.
However, in this attack, XMRig’s power consumption has been limited to 10% to avoid detection. Moreover, attackers added a batch script in the Start Menu Startup directory to ensure it runs on boot.
For your information, cryptominers are a type of malware that surreptitiously hijack a computer’s processing power to mine cryptocurrency for the attacker’s benefit. This unauthorized use of resources can cause the device to overheat, potentially leading to hardware damage and a shortened lifespan.
This isn’t a new trend, as fake job scams are becoming more prevalent online, with North Korean group Lazarus persistently using this method to trick unsuspecting users. Hackread recently reported Lazarus group deploying a new macOS trojan called “RustyAttr” since May 2024 to carry out its operations undetected.
Remember, legitimate recruiters rarely request candidates to download software or conduct interviews through unconventional channels. Always verify the authenticity of any job offer before proceeding and rely on official company websites for career opportunities and application processes.
CrowdStrike advises job seekers to be cautious of unsolicited interview offers, including those conducted via instant messaging or group chat, requests for product purchases or payment processing, and software download requirements.
“Organizations can reduce the risk of such attacks by educating employees on phishing tactics, monitoring for suspicious network traffic and employing endpoint protection solutions to detect and block malicious activity.”
CrowdStrikeTo verify the legitimacy of any communication from CrowdStrike, job seekers should contact the company’s recruiting team at [email protected].
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·