BOOK THIS SPACE FOR AD
ARTICLE ADInitially targeting Zoom users; the phishing scam aims for Outlook and Office365 credentials.
As the digital world deals with the added responsibility of hosting more and more meetings online, popular video conferencing apps like Zoom and Microsoft Teams have increasingly come under fire from cybercriminals.
With over 300 million participants every day, this makes Zoom a highly lucrative target for malicious elements. Keeping this in mind, in the latest, researchers from INKY have revealed how the app is being subject to a dedicated phishing campaign in several countries designed to extract credentials from users.
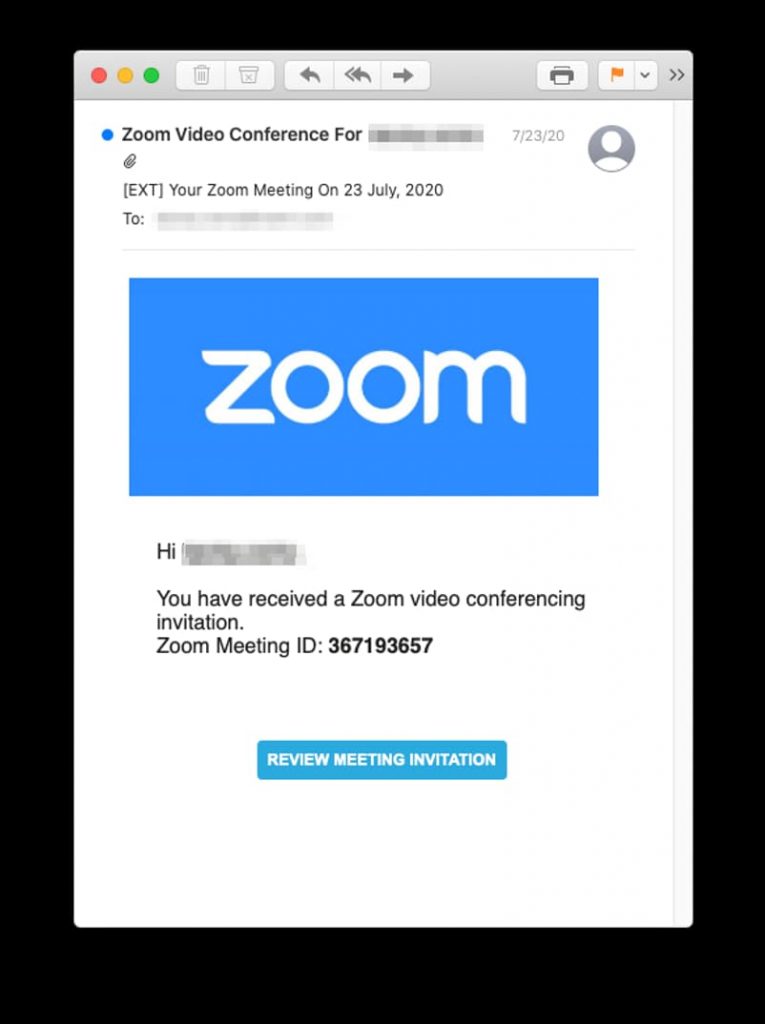
To start with, the attackers sent very convincing phishing emails to Zoom users with a variety of messages including but not limited to reviewing a meeting invitation, downloading a file attached to access details about a meeting invitation, and downloading a particular attachment to start the meeting in itself.
See: ‘Zoom account suspended’ phishing scam aims at Office 365 credentials
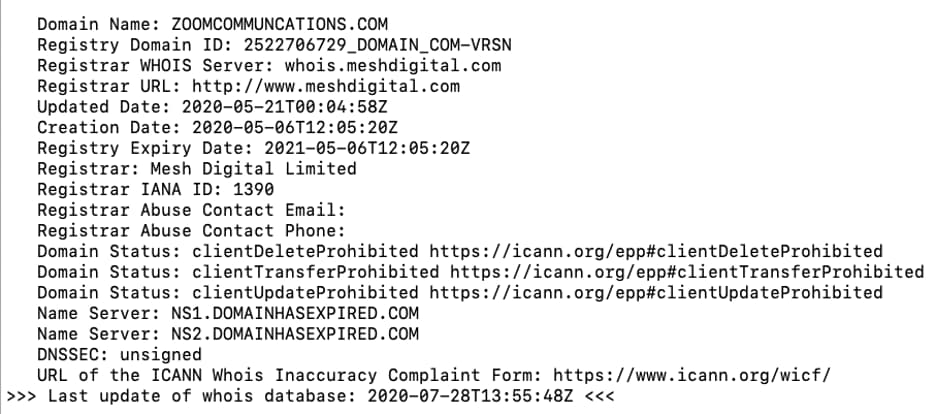
These originated from both hijacked accounts and also newly purchased domain names such as zoomcommuncations[.]com and zoomvideoconfrence[.]com which gives an aura of legitimacy to anyone who looks a bit deeper. Moreover, these also help bypass an email provider’s conventional filters.
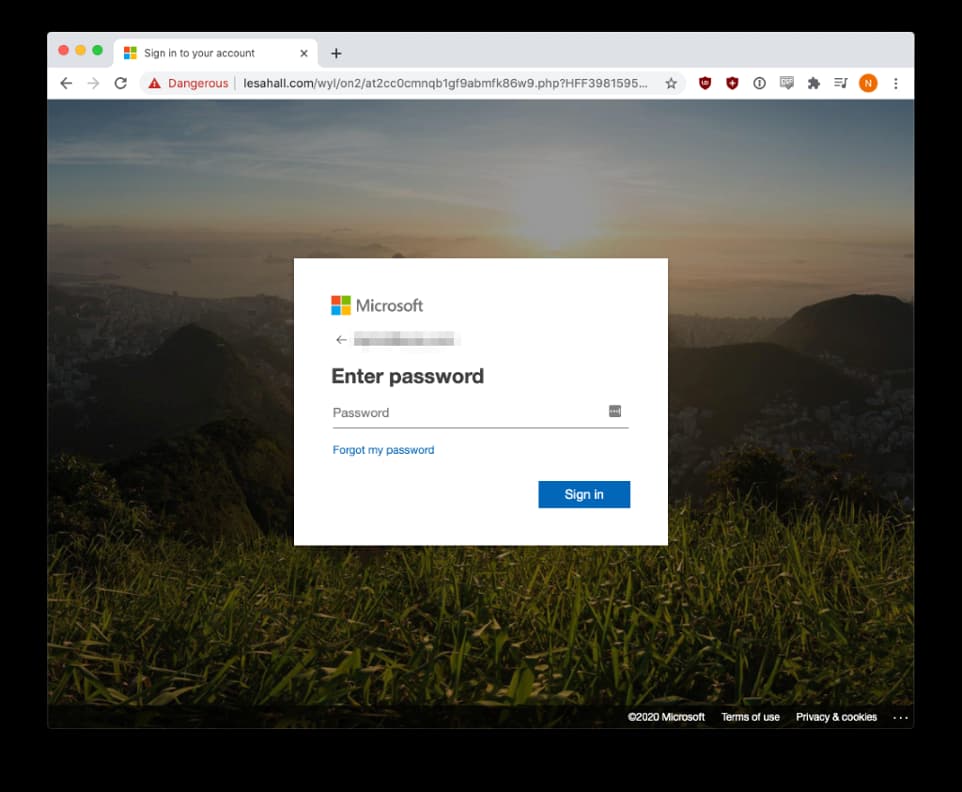
However, there’s a twist in the next step. Instead of asking users for Zoom details, once someone clicked on the links, they were instead redirected to a very real looking Microsoft Office365 or Outlook login page which in reality was of course fake.
See: Zoom web client flaw could’ve let hackers crack meetings passcode
In the case of attachments, a fake page that was mostly hosted on the attacker’s computer was opened asking for the same details. Elaborating on the effectiveness of these methods, the researchers state:
To make matters worse, the HTML, JavaScript, and PHP code is usually encoded so it’s unreadable to humans and automated security tools. It’s is a clever way to remain undetectable and evade URL reputation checkers.
If someone fell for these, not only could their own account be compromised but an attacker could also leverage the hacked account to conduct social engineering and therefore target other users of the same organization. In short, a ripple effect is created placing the security of everyone in jeopardy.
To conclude, according to INKY’s blog post, while the company itself has stopped about 5000 of these attacks as a part of their own efforts, it is very important for every business to take measures in educating their employees about such scams. This is because otherwise, companies could collectively lose several billion dollars a year in addition to the hit to their reputation.
See: Fake Zoom installers infect PCs with RevCode WebMonitor RAT
Useful tips include carefully checking the browser URL of every site before entering any login details and also not clicking on attachments from any unknown email address. Perhaps, in a world where email spoofing is on the rise, clicking on attachments even from trusted senders should be done with precaution.
Did you enjoy reading this article? Do like our page on Facebook and follow us on Twitter.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·