BOOK THIS SPACE FOR AD
ARTICLE AD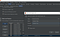
False positives are a bane of… well, everything. Scientists have to deal with it, and so do pentesters and bug bounty hunters. The difference is that as a bug bounty hunter if something is false positive and you’ve spent hours on it, you just got burned. You’ve earned some experience, though. That has to count for something.
Either way, if you are really serious about bug hunting, or hacking in general, you have to be up-to-date with new attacks, new tricks, and tips, etc. But, because these attacks are new to you, it means you may not be aware of the potential pitfalls within those attacks.
False2True:
This one was quite a revelation when I first heard about it. Here’s the link that got me started down that path.
The basic idea is to keep an eye for the Response bit of requests (I had more luck with responses to POST requests rather than GET) and note places where it shows “isAdmin”:false, “staff”:false, “userLevel”:basic, etc. You get the idea. Experiment, basically.
The attack is to use Match & Replace in burp (you don’t need the pro version either) and to add the rule like this:

Then refresh the page and see if you’ll be presented with some additional options, text, buttons, anything that wasn’t there before. You can open the same page in a browser that isn’t going through burp proxy, login as the same user and compare it with the browser that is going through burp proxy. And then play: spot the difference :)
At first, I didn’t have much luck in finding it. Nothing. But then…
Admin access bypass:
This was quite an exciting roller coaster, for a moment there. And then — crash.
The website had a request to /index.html which, as I followed the burp history, was followed with a request to /userinfo.json, before loading javascript files.
Userinfo.json looked something like this:
{“canEditUsername”:true,”canUploadFiles”:true,”isStaff”:false,”isAdmin”:false,”isUser”:true}
I think you can see where I’m going with this. What if “isAdmin”:false is changed, in the response, to “isAdmin”:true? Admin access enabled.
Obviously, as soon as I was able to access pages that were showing a list of website pages, and the Add/Edit/Remove was present, I immediately wrote a report and submitted it, expecting glory :)
Admin access, but without admin rights?
I soon got a response that it was Read only access. It was lacking any really serious impact, and therefore I got a very limited bounty.
Elevation? Possible, but only in some cases:
The story could have ended a paragraph earlier, but I figured this is an important thing to point out — always try to elevate the impact of the found bug. Even if at first it doesn’t look like much, you got your bounty, case closed, time to move on. Stop, and think.
Now that the pressure is off because you reported the bug, you got the bounty, no matter how small, with a relaxed mind give it another look. Maybe there is something you missed due to all the initial excitement. But, you’re chill now.
With that in mind, I decided to give it another look. I just couldn’t shake off this feeling that there had to be something more, but I was just too blind during the roller coaster ride to notice it.
And, as it turned out, during the registration, any user was able to specify a name of an existing company. But, as a user, you’d get very limited information about that particular company when going to its page from within your dashboard (I do apologize for such a vague explanation, but I respect the disclosure policy of that bbp.)
Therefore, when I achieved the admin access, I didn’t bother going to those pages, I focused on Admin dashboard button, Edit pages, the obviously sensitive stuff. With a calm in my mind, I had Match & Replace set to “isAdmin”:true again, and I figured let’s see what else is there.
Fortunately, I wasn’t in panic over how much time it would take the affected company to fix it because of previous experiences with them. I knew that I’d have some decent time to play with it some more. And, to my surprise, I noticed that visiting the company’s page with “isAdmin”:true would disclose some seemingly interesting info.
I added that to my original report, and soon enough I got a nice bonus because they agreed that the interesting info in question wasn’t something that they wanted others to have access to (btw, it wasn’t anything like usernames/passwords/etc., it was more like the business side of things).
.png)
 4 years ago
177
4 years ago
177 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·