BOOK THIS SPACE FOR AD
ARTICLE ADA DarkSide doppelganger mounts a fraud campaign aimed at extorting nearly $4 million from each target.
Several organizations in the oil, gas and food sectors have received threatening emails from cybercriminals posing as DarkSide – the ransomware gang behind the Colonial Pipeline hack.
According to researchers at Trend Micro, threat actors are taking advantage of the notoriety around the pipeline ransomware incident and the DarkSide name, in order to mount a fear-based social-engineering campaign.
The emails warn targets that the group has successfully hacked the recipient’s enterprise network and lifted sensitive information, which will be disclosed publicly if a ransom of 100 Bitcoin (BTC) is not paid. That’s roughly $3.8 million, given the exchange rate at press time.
That somewhat dovetails with the DarkSide playbook of double extortion – however, not all is as it seems, according to Trend Micro.
“The content used on the emails has led us to believe that they did not come from the said threat group, but from an opportunistic low-level attacker trying to profit off the current situation around DarkSide ransomware activities,” researchers said, in a Thursday blog post.
For instance, DarkSide generally offers proof that it has obtained stolen sensitive data, researchers pointed out – but no such assurances are provided in the recent spate of campaigns. Also, even though the fraudsters claim to be a ransomware gang, there’s no encryption of any files or other content on the supposed “victim” networks.
Then there’s a rookie attribution mistake: The emails mention DarkSide’s previous attacks that have hit the headlines of late, and include meat-industry giant JBS as a victim. However, that strike wasn’t DarkSide’s handiwork, but was rather attributed to REvil (a.k.a. Sodinokibi).
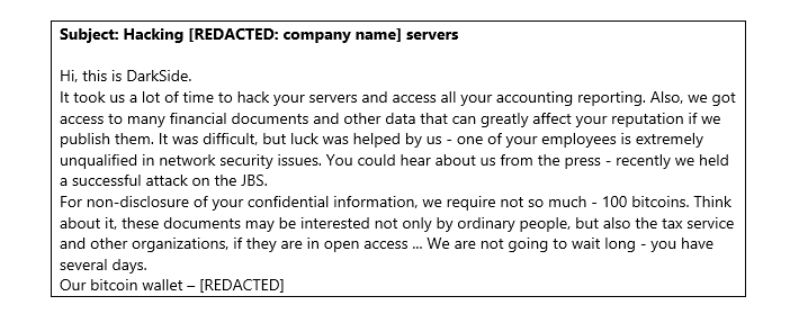
The extortion email. Source: Trend Micro.
It’s also worth noting that DarkSide generally asks for between $200,000 to $2 million according to previous reporting – not the almost $4 million requested in the recent emails.
“All in all, this campaign looks amateurish compared to known previous DarkSide activities,” according to Trend Micro. “We believe that most companies will not be urged to pay that amount without being shown any real evidence that the network has been compromised and sensitive data is about to leak in public.”
Mechanics of the Email Campaign
Trend Micro observed emails hitting a few targets daily, starting June 4. The messages were sent to generic email addresses within the organizations (i.e., addresses such as “support@[companyname].com” or similar). The sender emails are darkside@99email[.]xyz and darkside@solpatu[.]space.
The Bitcoin wallet at the end of the email is always the same for every target, according to the analysis.
The firm also saw that the same attacker also filled out contact forms on several companies’ websites, submitting the same content via web form as what’s included in the emails.
“In one case, we were able to get the sender’s IP address, 205[.]185[.]127[.]35, which happens to be a Tor network exit node,” researchers said.
The campaign cast a wide, global net: It affected Japan the most, followed by a tier of several other countries: Argentina, Australia, Canada, India and the U.S. The rest of the affected countries include China, Colombia, Mexico, Netherlands, Thailand and the U.K.
Even so, it appears that the DarkSide doppelganger is striking out – likely due to the lack of any encryption and the questionable email details: “As of writing, the said wallets have not received or sent any Bitcoin payment,” researchers said. “No actual attack has been traced back to the emails, and no new targets have been spotted.
“However, this does not remove the possibility that an attacker with more believable methods could successfully ensnare targets,” analysts warned.
Energy and Food Industries in Ransomware’s Sights
Based on the telemetry data, it seems the threat actor is zeroing in with laser-like focus on the energy and food industries, with all of the targets encompassed in these sectors, researchers noted. The likely thinking behind that is that the stakes are simply higher for these organizations.
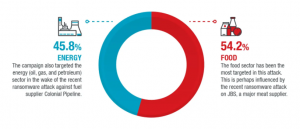
Targets by sector. Click to enlarge. Source: Trend Micro.
“These sectors are expected to provide essential goods and/or services on the daily basis,” according to Trend Micro’s analysis. “The longer the attack remains unthwarted and the companies’ operations subsequently interrupted, the more the affected organization losses profit and reputation. The shutdown of these services might also cause public uproar and panic, especially when it potentially affects a large number of people.”
And so, the logic follows that these types of companies will be more likely to give into extortion attempts.
“While the rest of the campaign shows clumsy techniques, it is worth noting that the attacker deliberately selected companies in specific industries for a reason,” according to Trend Micro. “In the aftermath, an attack’s impact could raise fears about food and/or energy security, triggering panic buying as the public worries about possible spikes in prices that could be caused by the attack.”
The energy and food sectors are among the most-targeted by cybercriminals of all stripes, including real ransomware gangs, the firm added – but it goes without saying that organizations should always verify the validity of any threat before taking any action when faced with a threatening notice.
Join Threatpost for “Tips and Tactics for Better Threat Hunting” — a LIVE event on Wed., June 30 at 2:00 PM ET in partnership with Palo Alto Networks. Learn from Palo Alto’s Unit 42 experts the best way to hunt down threats and how to use automation to help. Register HERE for free!
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·