BOOK THIS SPACE FOR AD
ARTICLE ADVolt Typhoon, initially identified by both Microsoft and U.S. authorities, infiltrated a diverse range of critical infrastructure organizations within the country.
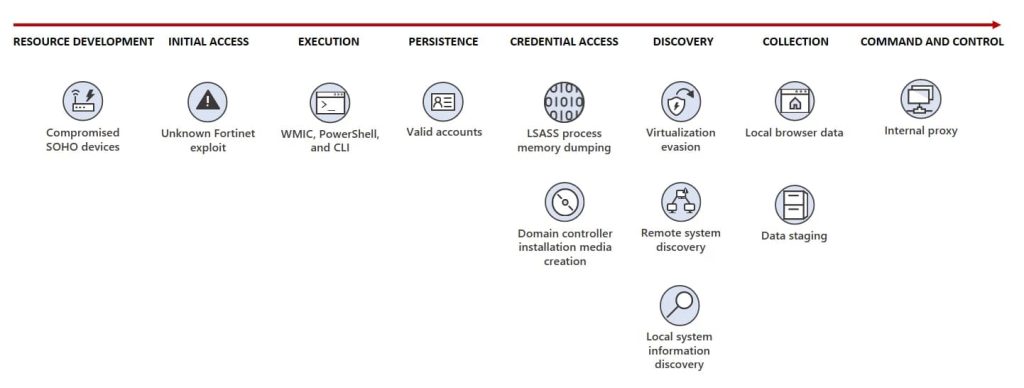
In a recent court-authorized operation conducted in December 2023, significant disruption was made to a botnet comprised of hundreds of U.S.-based small office/home office (SOHO) routers. These routers had been hijacked by state-sponsored hackers affiliated with the People’s Republic of China (PRC), a group known in private sectors as “Volt Typhoon.”
The operation targeted routers infected with the “KV Botnet” malware, which the hackers used to conceal the origin of their hacking activities directed against U.S. and other foreign targets.
Identified by both Microsoft and U.S. authorities, Volt Typhoon, infiltrated a wide array of critical infrastructure organizations in the United States, including communications, manufacturing, utilities, transportation, construction, maritime, government, IT, and education.
The sophistication and dangers posed by the threat actors were also highlighted in a May 2023 advisory from the FBI, National Security Agency, Cybersecurity and Infrastructure Security Agency (CISA), and foreign partners.
The botnet primarily comprised Cisco and NetGear routers that had reached “end of life” status, meaning they were no longer supported by security patches or updates from their manufacturers. The operation aimed to remove the KV Botnet malware from these routers and sever their connection to the botnet, thereby preventing further exploitation.
In a press release, FBI Director Christopher Wray condemned the actions of the Volt Typhoon, noting the potential real-world threat their activities posed to the safety of American citizens and critical infrastructure. He underscored the FBI’s determination to thwart such malicious activities and work with partners to protect against cyber threats.
For additional insights, we reached out to Toby Lewis, Global Head of Threat Analysis at Darktrace, a leading provider of global cyber security artificial intelligence. Toby cautioned that while the botnet may be a thing of the past, the group behind it still exists and could potentially resurface with a fresh botnet.
“The actions by the US government have likely significantly disrupted Volt Typhoon’s infrastructure, but the attackers themselves remain free. Targeting infrastructure and dismantling attacker capabilities usually leads to a period of quiet from the actors where they rebuild and retool, which we’re probably going to see now,” said Toby.
“The government’s ambitious approach to mimic the attacker’s own command network is a win in the short term, but there is no way to guarantee that this has a lasting impact on the threat landscape,” Toby explained. “Organizations need intelligent systems which can detect subtle, emerging, and novel threats and take targeted action without relying on knowledge of the attacker’s specific systems,” he warned.
Nevertheless, the FBI provided notice of the operation to owners or operators of infected SOHO routers and encouraged them to replace end-of-life routers to prevent future exploitation. The investigation into the Volt Typhoon’s activities continues, with efforts ongoing to mitigate further cyber threats posed by the group.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·