BOOK THIS SPACE FOR AD
ARTICLE ADThe latest refinement of the APT’s BadHatch backdoor can leverage new malware on the fly without redeployment, making it potent and nimble.
The financially motivated FIN8 cybergang used a brand-new backdoor – dubbed Sardonic by the Bitdender researchers who first spotted it – in attempted (but unsuccessful) breaches of networks belonging to two unidentified U.S. financial organizations.
It’s a nimble newcomer, researchers wrote: “The Sardonic backdoor is extremely potent and has a wide range of capabilities that help the threat actor leverage new malware on the fly without updating components,” according to Bitdefender’s report.
FIN8 has typically gone after financial services and payment-card data from point-of-sale (PoS) systems, particularly those of retailers, restaurants and the hotel industry. It’s been active since at least January 2016, but it periodically pops in and out of dormancy in order to fine-tune tactics, techniques and procedures (TTPs) and thereby evade detection and ramp up its success rate.
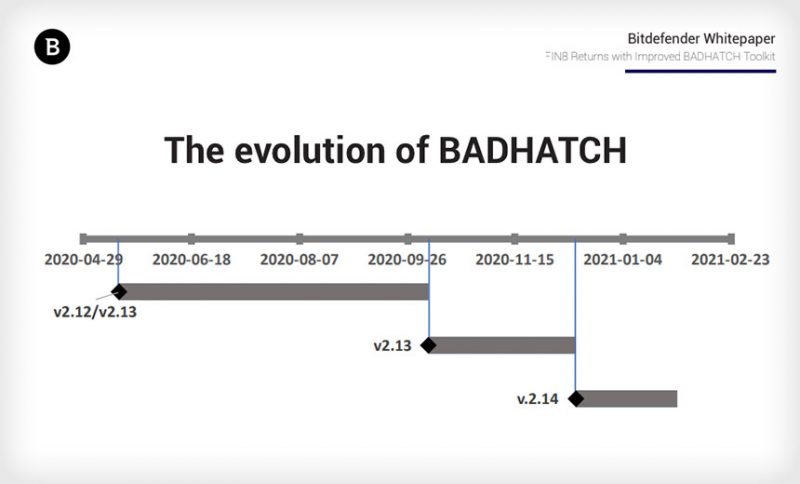
True to form, in March, Bitdefender spotted FIN8 re-emerging after a period of relative quiet with a new version of the BadHatch backdoor to compromise companies in the chemical, insurance, retail and technology industries. Sardonic is an updated version of BadHatch that’s apparently still under development, Bitdefender said.
It’s a refinement of BadHatch in that it can be automatically boosted with new functionality without the malware needing to be redeployed: A way to make it more agile, Bitdefender said.
Bogdan Botezatu, director of threat research for Bitdefender, told BankInfoSecurity that the security firm has seen FIN8 carrying out two attacks over the past few months, what he called “unusually high activity for a threat actor that used to take long breaks between attacks.”
Besides BadHatch – a backdoor that provides file transfer and reverse-shell functionality – FIN8’s well-stocked arsenal has included malware variants such as ShellTea, a backdoor also known as PunchBuggy, and the memory-scraper tool PoSlurp/PunchTrack. FIN8 has also used the TTPs of exploiting Windows zero-days and spear-phishing.
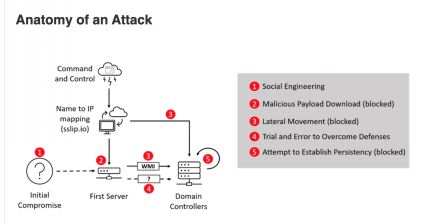
Bitdefender isn’t sure what the initial infection vector was on the thwarted bank attack, but based on FIN8’s prior attacks, it was likely via social engineering and spear-phishing campaigns.
Sardonic Still Being Refined
And now, there’s Sardonic. Earlier this week, Bitdefender published a deep dive describing a forensic investigation that led to the discovery of the new backdoor. Artifacts led researchers to conclude that the threat actors use that name to describe “an entire project including the backdoor itself, the loader and some additional scripts,” according to Bitdefender.
Sardonic is apparently still under development, and Bitdefender suspects that the threat actors will be using additional updates still to come.
The Two Attacks
During one of the attacks – a recent attack against an unidentified financial institution in the U.S. – FIN8 used a three-stage process to deploy and execute the Sardonic backdoor: A PowerShell script, a .NET loader and downloader shellcode.
After it was loaded, Bitdefender said that the embedded dynamic link library obtained the value of the Y1US environment variable and extracted the string that contained options for behavior customization so it could make changes.
Bitdefender said that the new backdoor tried to evade security monitoring by using TLS encryption in order to conceal Powershell commands. After it gains network access, FIN8 has used the access to scan for victim networks, give attackers remote access, install a backdoor and deliver other malware payloads.
Fending Off Financial Malware
Bitdefender recommends that companies in the targeted verticals – retail, hospitality and finance – check for potential compromise by applying the indicators of compromise (IoCs) listed in its whitepaper (PDF), and implementing endpoint detection and response (EDR), extended detection and response (XDR) and other security defenses.
Bitdefender offered these protective measures:
Separate the PoS network from the ones used by employees or guests Introduce cybersecurity awareness training for employees to help them spot phishing e-mails. Tune your e-mail security solution to automatically discard malicious or suspicious attachments. Integrate threat intelligence into existing SIEM or security controls for relevant indicators of compromise.Check out our free upcoming live and on-demand webinar events – unique, dynamic discussions with cybersecurity experts and the Threatpost community.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·