BOOK THIS SPACE FOR AD
ARTICLE ADAPIs are the keys to an organization’s databases, so it’s essential to control who has access to them. Industry-standard authentication and authorization mechanisms such as OAuth/OpenID Connect, in conjunction with Transport Layer Security (TLS), are crucial.
When APIs are open to the public, they face the challenge of determining if incoming requests should be trusted. Is the request a customer? Or is it an attacker? In some cases, even if the API detects and successfully denies an untrusted request, the API may nevertheless allow the potentially malicious user to try again — and again and again and again. This kind of security oversight may allow attackers to attempt to playback or replay a legitimate user request until they are successful. Countermeasures against these brute force attacks include rate-limiting policies to throttle requests, two-factor authentication, or a short-lived access token facilitated by OAuth
There are many methods to find these api-keys in a application.
Inspecting the Source CodeOpen the web application in a browser.Use developer tools (F12 or Ctrl+Shift+I):Look at the HTML source, JavaScript files, or other client-side resources.Search for terms like key, token, api, or anything resembling sensitive credentials.2. Analyzing JavaScript Files
. Check external JavaScript files (.js) linked in the application.
. Use Jsleak tool to find secrets in the Js files
https://github.com/byt3hx/jsleak
3. Checking Git Repositories
Look for publicly exposed Git repositories related to the web application.Use tools like git log, git grep, or TruffleHog to search for leaked secrets.KeyFinder is a chrome extension developed by Mo’men Basel that searches the DOM for any embed script link, as script tag may contain keys for specific API.
https://github.com/momenbasel/keyFinder
Installation of Key-Finder
Download the Zip File in the system & Extract itopen the Google ChromeType “chrome://extensions” in the urlEnable the Developer mode5. Drag & drop the key-finder folder here
How to use Key-Finder to find the Public/Hidden API-Keys
1. Open the Extension & add some keywords you want to search
Common Keywords :
api-key, api_key , api_keys , api-keys , SECRET_KEY , ACCESS_TOKEN , AUTH_TOKEN, BEARER_TOKEN ,PRIVATE_KEY PUBLIC_KEY , CLIENT_SECRET , APP_SECRET , CONSUMER_KEY , access_key , access-key , secret-token , secret_token , app_token , api-token , api-id
2. Now You can go to your target & visit pages. The extensions will automatically capture hidden/public api keys. Click on Results in the extension to check the findings
Now the most interesting part, you found some keys and don’t know what to do further. So below the details shows the ways to check if they are valid or not
https://github.com/streaak/keyhacksthis repo contains all the methods to use the api-keys
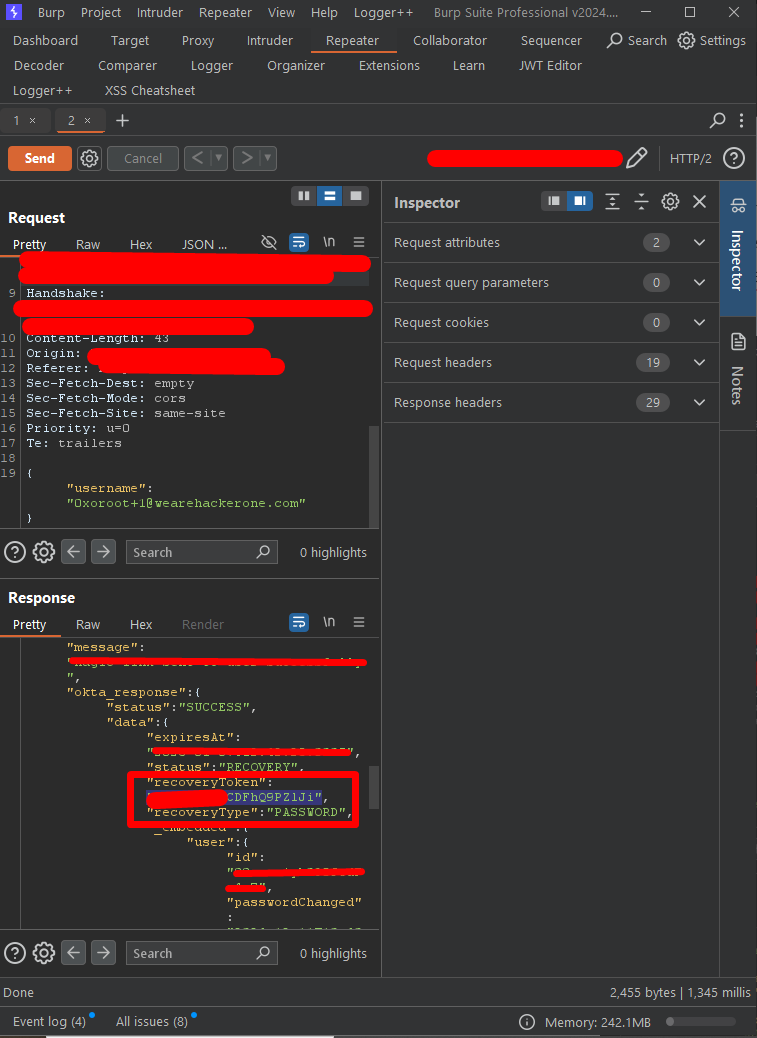
Some Example Reports that are publicly disclosed on Hackerone
Lastly , if you find this article helpful , share with your fellow researchers
Thank You
Sumit Jain
Linkedin : https://www.linkedin.com/in/sumitjainofficial/
Youtube : https://www.youtube.com/@thecybersecurityzone
Twitter : https://x.com/sumit_cfe
.png)
 4 days ago
16
4 days ago
16 












 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·