BOOK THIS SPACE FOR AD
ARTICLE ADPublishing platform’s failure to verify session cookies resulted in ‘easy to exploit’ vulnerability
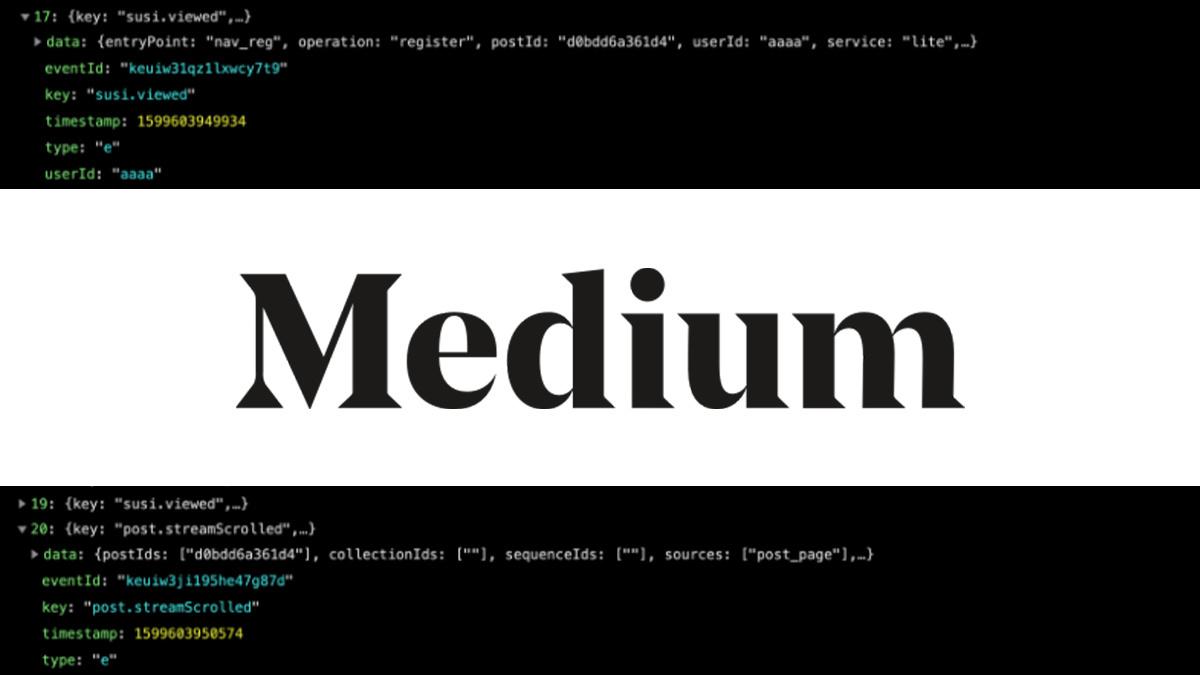
A business logic vulnerability in Medium’s Partner Program meant cybercrooks could siphon writers’ article engagement earnings, a security researcher has discovered.
The Medium Partner Program allows selected writers to earn a monthly fee based on the time subscribers spend reading their articles on the online publishing platform.
In a blog post on Medium itself that retraced his steps to unearthing the flaw, Mohammad-Ali Bandzar discovered that the platform “will embed any userID cookie value you transmit”.
Failing to validate the user’s “logged in session”, he added, the endpoint “blindly accepts userIDs and assumes they are correct”.
He said the flaw was “incredibly easy to exploit” and told The Daily Swig that there was no obvious ceiling on the earnings attackers could potentially pilfer undetected.
The find was assigned the second highest severity of four tiers under Medium’s vulnerability disclosure program, which attracted a reward of $250, Bandzar’s first-ever bug bounty.
The researcher told The Daily Swig that he understands the flaw has been fixed, although he hasn’t independently verified this.
 Bandzar published his Medium vulnerability write-up on Medium
Bandzar published his Medium vulnerability write-up on Medium
Discovery process
Bandzar says he initially set out not to find security vulnerabilities, but to ascertain how subscribers’ $5 monthly fee was shared between writers on the Medium platform.
A replay attack on , which transmits the metrics used to calculate earnings, revealed that the userID within every JSON object in the request payload was the only quality unique to the user.
His efforts to modify the userID then foundered on stringent code obfuscation deployed by Medium. This “really hampered my efforts in finding this bug”, he told The Daily Swig.
He then decided to mount a manipulator-in-the-middle (MitM) attack against himself in order to find and replace his own userID with one he could “impersonate while the data was in transit”.
The cookie crumbles
The breakthrough came when Bandzar changed the requesting userID cookie value for the request to the main HTML page of his article.
“To my absolute amazement, medium.com embedded the userID cookie value into the webpage as JSON data before validating that the session cookie and userID cookie represent a valid logged in session.
“Although the webpage does correctly identify my userID/session cookie as being invalid; it will still embed the userID data from the request cookie into the webpage.”
Read more of the latest security vulnerability news
The researcher added: “In the response, it sends back the headers with information of a new session UID starting with .”
Consequently, whatever userID cookie value forms the main web page request will be used by all batch requests as the ‘’.
Following this process to establish a proof of concept, the researcher said he was able to generate $0.34 in Medium Partner Program income by impersonating about 10 people in a single day before reporting the flaw.
Simple but effective
Speculating that a “generic detection system” might only detect “a single article/account generating an abnormal amount of earnings”, Bandzar believes that he could have “very easily created dozens of partner program accounts and sent” himself “a few thousand dollars a month indefinitely”.
But while exploitation was potentially costly for Medium writers and the discovery process multi-staged, Bandzar says the bug was remarkably simple from a technical perspective.
“I spent dozens of hours trying to discover this bug,” he said, yet the bug arises from a simple failure to verify session cookies.”
RECOMMENDED Santiago Lopez on his route to becoming the world’s first bug bounty millionaire
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·