BOOK THIS SPACE FOR AD
ARTICLE AD
The makers of Flipper Zero have responded to the Canadian government's plan to ban the device in the country, arguing that it is wrongfully accused of facilitating car thefts.
In early February 2024, the Canadian Industry Minister, François-Philippe Champagne, announced a proposal to ban imports of "consumer hacking devices, like flippers" as criminals reportedly use those to steal cars.
The authorities also presented statistics that showed a rise in car thefts, reaching 90,000 annually, which Canadian lawmakers believe is linked to the availability of Flipper Zero and similar hacking tools.
The Flipper Zero is a portable and programmable pen-testing tool that allows users to experiment with and debug various hardware and digital devices using multiple protocols, including RFID, radio, NFC, infrared, and Bluetooth.
However, much of Flipper Zero's functionality can be reproduced using other devices, including computers, Android phones, and Raspberry Pi, which are not being targeted by any country-wide ban.
Flipper Devices, the maker of the portable pen-testing tool, argues that these accusations are ill-informed and Flipper Zero is incapable of stealing cars using keyless entry systems.
"We believe that proposals like this are harmful to security and slow down technological progress," reads a new blog post from Flipper Devices.
"They are usually made by those who do not really understand how security works and will do nothing to solve the car theft problem."
The developers explain that car theft requires signal repeaters costing between $5,000 and $15,000, which can be bought online.
 Repeater used in car thefts (flipper.net)
Repeater used in car thefts (flipper.net)Car thieves approach the front door of the car owner with those repeater devices and re-transmit the key fob's passive signal to their accomplice standing close to the car, and the vehicle unlocks as if the actual key is in proximity.
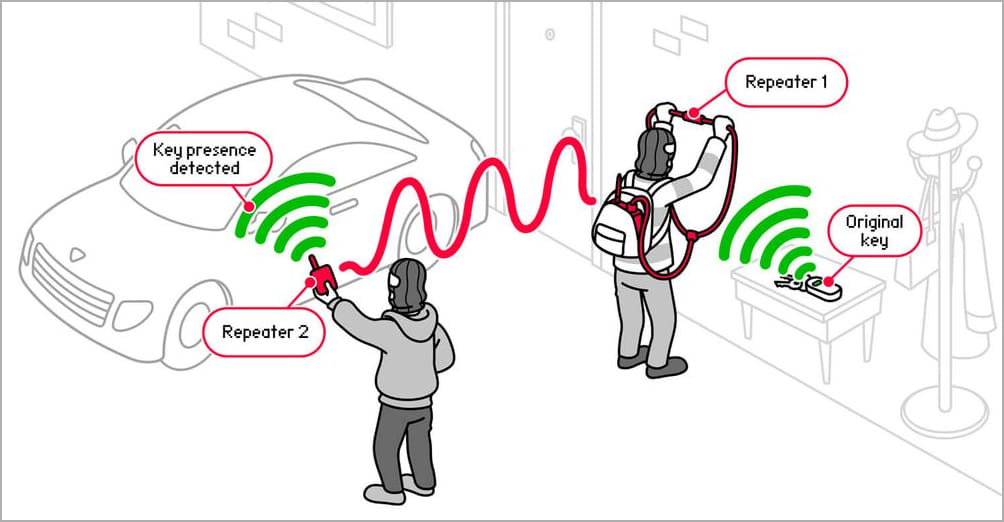 How the attack works (flipper.net)
How the attack works (flipper.net)These repeater devices feature multiple radio modules and several watts of power, making the attack possible.
On the other hand, Flipper Zero relies on a single radio module and is limited to just ten milliwatts, which makes it severely underpowered and impractical for use cases such as actual car thefts.
"To transmit signals to key fobs through walls, thieves need huge antennas and powerful repeaters," explains Flipper Devices.
"All video-documented cases of car theft show that theft equipment takes up a lot of space in thieves' backpacks."

The Flipper Zero team also criticizes the ban decision as highly selective, considering that the internal electronics the device uses have been widely available for many years and are used by numerous other devices.
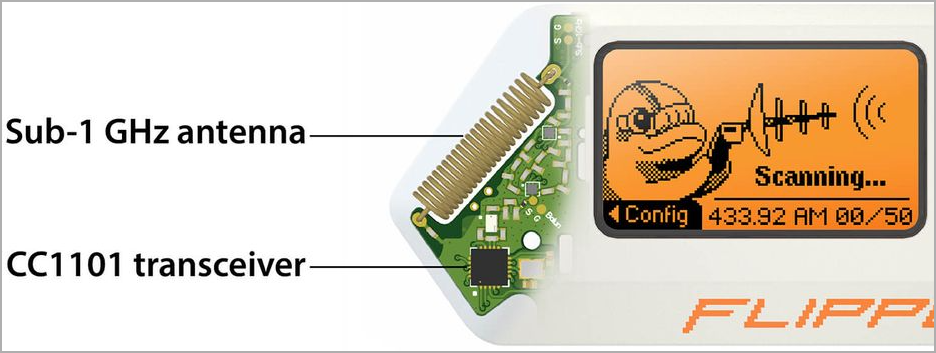 Internal components (flipper.net)
Internal components (flipper.net)Fix the root of the problem
The device makers highlight the underlying error in focusing on the means rather than the actual problem, which is the widespread use of outdated and vulnerable access control systems found in automobile systems.
"The Flipper Zero is built with hardware components used in thousands of devices ranging from radio toys to educational DIY kits. For example, the CC1101 radio transceiver inside the Flipper Zero has been widely used since its release in 2007. The problem is not in the available radio hardware, but rather in the insecurity of outdated access control systems." - Flipper Devices.
Security through obscurity is a fundamentally flawed strategy and a lost battle. The developers emphasize that prohibiting tools researchers use to identify security flaws will only exacerbate the issue, leaving devices vulnerable to exploitation for extended periods.
Finally, the Flipper Zero team calls for the support of the security research and pen-testing community, asking people to sign a petition against the ban of Flipper Zero and similar devices.
Canadian fans of the device have also created the 'Save Flipper' website to raise awareness, urging citizens to contact their parliament representatives and demand that they oppose the proposed measures.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·