BOOK THIS SPACE FOR AD
ARTICLE ADThe banking trojan keeps switching up its lies, trying to fool Android users into clicking on a fake Flubot-deleting app or supposedly uploaded photos of recipients.
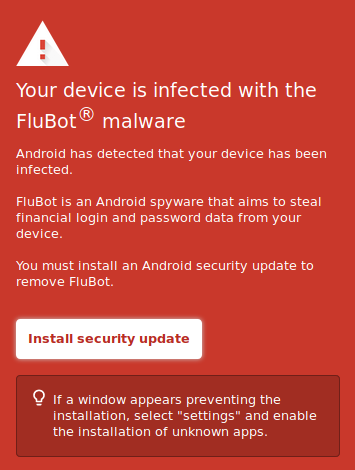
The Flubot banking trojan is using a fake security warning to try to trick Android users into thinking that they’ve already been infected … with Flubot.
It’s a lie, but it will become a reality if recipients of the text message fall for it and click on the “install security update” button.
“Android has detected that your device has been infected,” the message reads, along with instructions on how to install a security update that will purportedly scrub off the malware.
On Friday morning, New Zealand’s computer emergency response team (CERT NZ) warned that clicking to “install security update” will actually trigger the Flubot infection.
If you are seeing this page, it does not mean you are infected with Flubot however if you follow the false instructions from this page, it WILL infect your device. https://t.co/KrcPhCQB90
— CERT NZ (@CERTNZ) September 30, 2021
Fast-Changing Text Messages
In an advisory published Friday morning, CERT NZ warned that Flubot malware is spreading via text messages on Android phones, using wording that’s continually in flux.
When the scourge first started earlier this week, New Zealand’s telecommunications sector warned that the new scam text was pretending to be an alert from a courier company that asked users to click on a link or download an app to get information about delivery of a parcel.
Telecommunications Forum chief executive Paul Brislen told e-Commerce News that “The payload appears to resend the text via the users address book and also asks for bank information. Needless to say at a time when everyone is using courier delivery services, this has the potential to cause a lot of damage.”
As of Friday, the threat actors had switched it up, with scam text that pretends that photos of the recipient have been uploaded. The most recent scam twist is this 100% garbage “security update.”
Expect yet more creative writing exercises still to come, CERT NZ recommended, adding that New Zealanders should forward the texts to 7726 and then delete them:
“Given that the wording of these texts has changed within a short timeframe, it is likely the wording will change again. Be wary of any suspicious text messages you receive, asking you to click on a link, and forward any new suspicious texts to 7726.” —CERT NZ
In all cases, there will be a link asking recipients to install an app or a security update.
“Messages are sent from phones infected with this app so there is no simple way to prevent your phone from receiving these messages,” according to the advisory. “Forwarding them to 7726 helps the Department of Internal Affairs (DIA) and CERT NZ to shut down the links in the text messages and contact people who have been infected by the app.”
iPhones Are Flubot-Free
Flubot is only a danger to Android devices. While Apple iPhones can receive the text, they can’t be infected, according to CERT NZ.
Neither are phones infected until and unless hapless users download and install the purported anti-FluBot software.
Below are some examples of what the installation messages may look like. The first, the parcel-related message, has been used in previous Flubot campaigns:

What If I Clicked But Didn’t Download?
Users who clicked on the link but didn’t download anything likely didn’t trigger a Flubot infection. However, New Zealand’s security overseer “strongly recommends” that such users change all their online account passwords and contact their banks just to be safe.
The same goes for users who entered personal information into a form – particularly payment card details: change passwords and contact your bank to check for unusual activity.
What is Flubot?
The Flubot banking trojan is after banking and credit card information as well contact lists that it updates to a server and uses to keep spreading itself. “Once a device has been infected with this malicious app it can result in significant financial loss,” according to CERT NZ.
“The malicious app automatically sends text messages from infected devices to contacts it has received from other infected devices,” according to CERT NZ’s scam alert. “Once the message is sent, the phone blocks the number so the recipient is unable to respond to avoid raising suspicion.”
The New Zealand Flubot campaign is a copy-paste repeat of one that hit in April 2021. At that time, the malware spread rapidly, using a similar parcel-related message. The “missed package delivery” come-on was similarly spread through SMS texts, prompting urgent scam warnings from mobile carriers as Android mobile phone users across the U.K. and Europe were targeted.
These types of SMS phishing scams are known as smishing attacks, and they’re far from new. In February, attackers were harvesting personal data of users in the U..K. with fake messages promising tax refunds for overpayment. Mobile phishing has been a booming business since the start of the COVID-19 pandemic, experts say, and is expected to keep growing.
Discussing that February campaign, Paul Ducklin, a researcher at Sophos, explained why smishing is becoming such a popular choice for threat actors.
“SMSes are limited to 160 characters, including any web links,” Ducklin wrote. “So there’s much less room for crooks to make spelling and grammatical errors, and they don’t need to bother with all the formalized cultural pleasantries (such as ‘Dear Your Actual Name’) that you’d expect in an email.”
What If My Android Is Infected?
CERT NZ said that you’re going to have to do a full factory reset as soon as possible if your device is infected, deleting all your phone’s data. Restoring from backups is, unfortunately, off the table, it said: “Do not restore from backups created after installing the app. Seek the services of a qualified IT professional if you require assistance.”
Also change all online account passwords, particularly to online bank accounts and, again, contact your bank if you see suspicious activity.
Check out our free upcoming live and on-demand webinar events – unique, dynamic discussions with cybersecurity experts and the Threatpost community.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·