BOOK THIS SPACE FOR AD
ARTICLE ADIt’s been a long time since my last post, writing somethings I have learned from my job or little research. So, please read and I write. I don’t push you to read but I am appreciate if you want to read and clap. LOL.
As usual, I have task of mobile application penetration testing. It turns out that the application was made by Flutter. More detail of Flutter can be found on official Flutter site.
Like most mobile penetration testing, we have to check network traffic (Request and Response), SSL Pinning, Root Detection and many more.
So here’s the problem: root CA is implemented in unique way, which need a custom bypassing strategy. I came across some websites which gives detail explanation:
https://blog.nviso.eu/2019/08/13/intercepting-traffic-from-android-flutter-applications/https://orangewirelabs.wordpress.com/2019/06/04/bypassing-root-ca-checks-in-flutter-based-apps-on-android/In short, we do SSL pinning bypass without script, just traffic redirection. Here’s the concept:

In normal ways FlutterApp send data to backend and we want to get traffic on burpsite, let’s say we connect The Wi-Fi and FlutterApp has 192.168.1.8 and PC has 192.168.1.5.

First we have to make port forwarding all traffic passing our machine (PC/Laptop/Notebook). There are several ways to do so, depends on your OS (Windows/Linux/Mac). In this case, I use Mac OS X.

In your device, make sure you use your PC as gateway by giving static address.
ip address : set it, in this case (192.168.1.8)
gateway : your pc ip address in this case (192.168.1.5)
After forwarding all trafiic from device passing machine let’s check target with wireshark. After long analyzing the apps with wireshark, we got the ip address and DNS target


Let’s continue, pass our traffic to burp suite, the favorite tool for hacker.
Filter the packet so we only forwarding HTTPS related packet to Burp, using packet filter control, save it into pfctl.txt.
rdr pass inet proto tcp from 192.168.1.5 to redacted.redacted.co.id port 443 -> 127.0.0.1 port 6969
For detail command please come to pfctl manual (google it).
Then run the pfctl
sudo pfctl -f pfctl.txt
then check it with
sudo pfctl -s nat
Configure our Burp Suite to handle the request/response

Request Handling Configuration
Check “Force use of TLS” if your target using SSL, if not dont check it
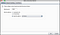
Binding Configuration

Proxy Listener

Request from FlutterApp

Response from backend
Thank you for reading and i hope this useful for everyone.
.png)
 4 years ago
268
4 years ago
268 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·