BOOK THIS SPACE FOR AD
ARTICLE AD
NVD published two advisories this week for critical command injection vulnerabilities purportedly impacting Fortinet's FortiSIEM products, but there's more to what meets the eye.
BleepingComputer has confirmed that these CVEs are not "new," but duplicates of a previously known FortiSIEM vulnerability and were issued in error.
Fortinet: 'No new vulnerability' in FortiSIEM in 2024
Two critical severity vulnerability advisories have emerged on NVD, implicating ForiSIEM, Fortinet's SIEM solution.
These OS command injection vulnerabilities, tracked as CVE-2024-23108 and CVE-2024-23109 were each scored as a 10/10, the highest on the CVSS scale that is used to define the severity associated with a vulnerability.
Confusingly enough, Fortinet's advisory associated with these CVEs bears a publication date of "Oct 10, 2023"—not yesterdaty's, and additionally lists a previously known CVE-2023-34992, also a critical FortiSIEM OS command injection flaw.
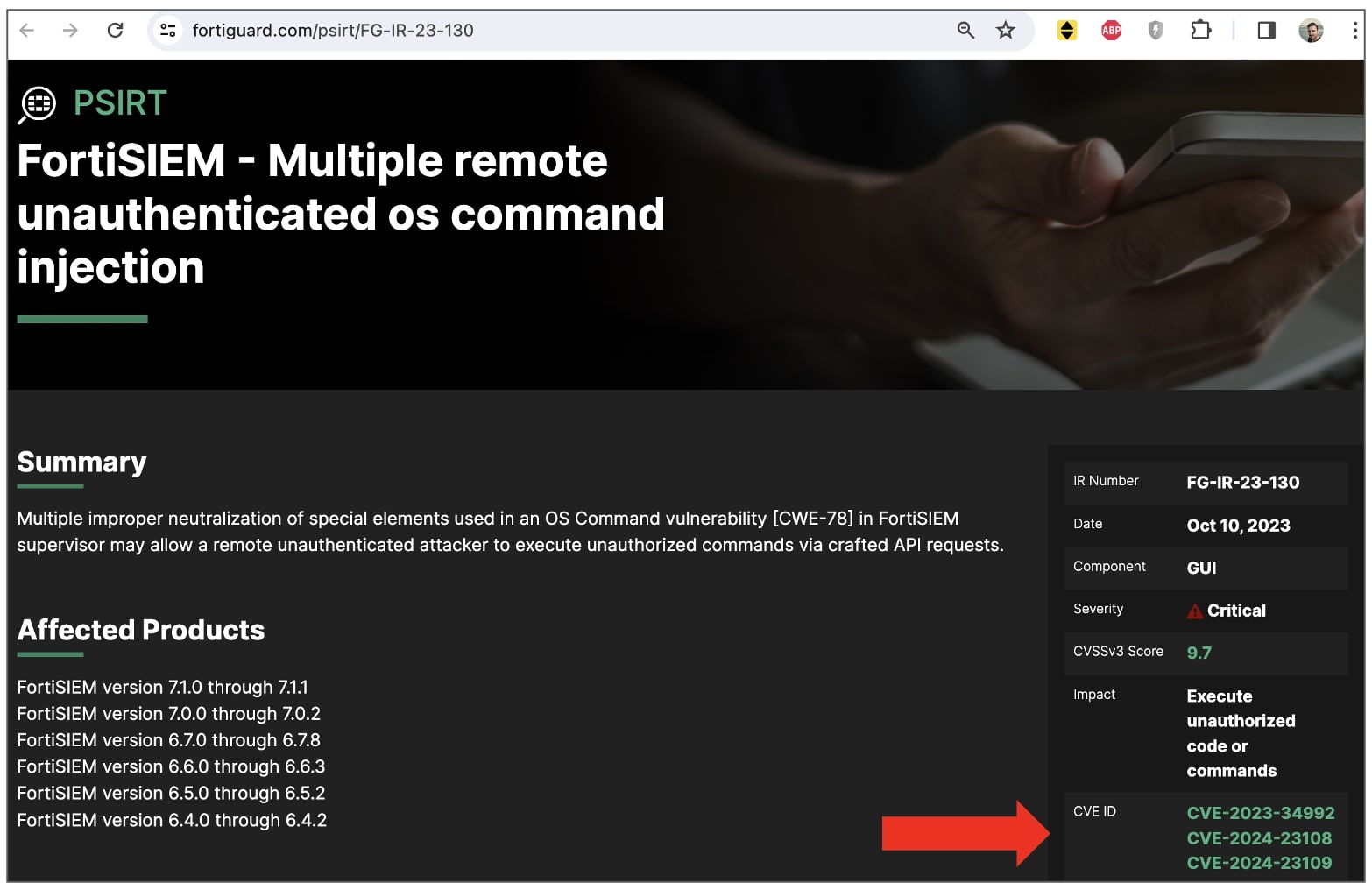 Fortinet advisory for critical FortiSIEM vulnerability lists 3 CVEs
Fortinet advisory for critical FortiSIEM vulnerability lists 3 CVEs(BleepingComputer)
BleepingComputer reached out to the vendor for clarification and turns out, there's nothing to see here—the two new CVE IDs, CVE-2024-23108 and CVE-2024-23109 have been generated in error.
"A modification was made to the original FG-IR-23-130 - which commonly happens to ensure ongoing accuracy of information and updates are pushed to the NVD Database in parallel to keep the two systems in sync," a Fortinet spokesperson told BleepingComputer.
"In this instance, due to an issue with the API which we are currently investigating, rather than an edit, this resulted in two new CVEs being created, duplicates of the original CVE-2023-34992. There is no new vulnerability published for FortiSIEM so far in 2024, this is a system level error and we are working to rectify and withdraw the erroneous entries."
As such, MITRE, NVD, and other vulnerability intel sources should ideally shortly start revoking advisories for CVE-2024-23108 and CVE-2024-23109.
Consequently, InfoSec/IT teams that have already addressed last year's CVE-2023-34992 in their environments should not need to take any further action. We still recommending checking out Fortinet's latest advisory on the CVE to be certain of affected products and versions with a fix.
Command injection vulnerability in review
Disclosed in October last year, the now-patched CVE-2023-34992 is an OS Command Injection vulnerability in FortiSIEM supervisor that could allow unauthenticated remote attackers "to execute unauthorized commands via crafted API requests."
In November 2023, a variant of CVE-2023-34992 emerged, tracked at the time as CVE-2023-36553 and similar in terms of its nature and severity.
Fortinet products include firewalls, endpoint security, and intrusion detection systems commonly used by enterprises. These have often been targeted by sophisticated, state-backed hacking groups, for access to an organization's network.
Last year, various cybersecurity reports confirmed bugs in Fortinet products being exploited by Iranian hackers to attack U.S. aeronautical firms and Chinese cyber-espionage clusters [1, 2].
Additionally, there have been cases where hackers exploited zero-day vulnerabilities in Fortinet products to breach government networks, discovered after painstakingly reverse-engineering specific FortiGate OS components.
Sergiu Gatlan of BleepingComputer contributed to this report.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·