BOOK THIS SPACE FOR AD
ARTICLE AD
An affiliate of the GandCrab ransomware-as-a-business (RaaS) has been arrested, according to an official release. Authorities were able to identify the individual in cooperation with law enforcement in Romania and the U.K.
The cybercriminal’s identity has not been published but Office “K” of the Ministry of Internal Affairs in Belarus says that he is a 31-years old living in Gomel, a city in southeastern Belarus.
Encrypted computers in nearly 100 countries
The arrested GandCrab member was an affiliate, or 'Advert', for the organization and was responsible for distributing the ransomware to victims.
"It was established that a 31-year-old resident of Gomel who had no previous convictions infected more than a thousand computers. For decrypting each of them, he demanded an amount equivalent to 1.2 thousand US dollars. Access to the admin panel for managing the ransomware botnet was carried out via the darknet, which allowed the attacker to remain anonymous for a long time," said Vladimir Zaitsev, Deputy Head of the High-Tech Crimes Department of the Ministry of Internal Affairs.
"Part of the profit was transferred to the administrators (operators) of the server he leased. The victims of the hacker were users from almost a hundred countries, and the largest number of victims were in India, the USA, Ukraine, Great Britain, Germany, France, Italy and Russia," Zaitsev added.
It is unclear how much money the criminal made from this operation but he shared part of the paid ransoms with GandCrab administrator(s) who kept a server hidden in the darknet, allowing affiliates to remain hidden.
As part of their role of infecting victims, GandCrab affiliates would earn 60% for the first three ransom payments they are responsible for. After the third payment, their revenue share would jump to 70%.
This means if the arrested affiliate was demanding $1,200 as a ransom payment, they would earn $840 per victim and the GandCrab developers would earn $360.
Larger affiliates who demanded millions of dollars would stand to make far greater amounts of payments.
GandCrab shut down their operation on June 1st, 2019, after claiming to have generated more than $2 billion in ransom payments and personally earning $150 million.
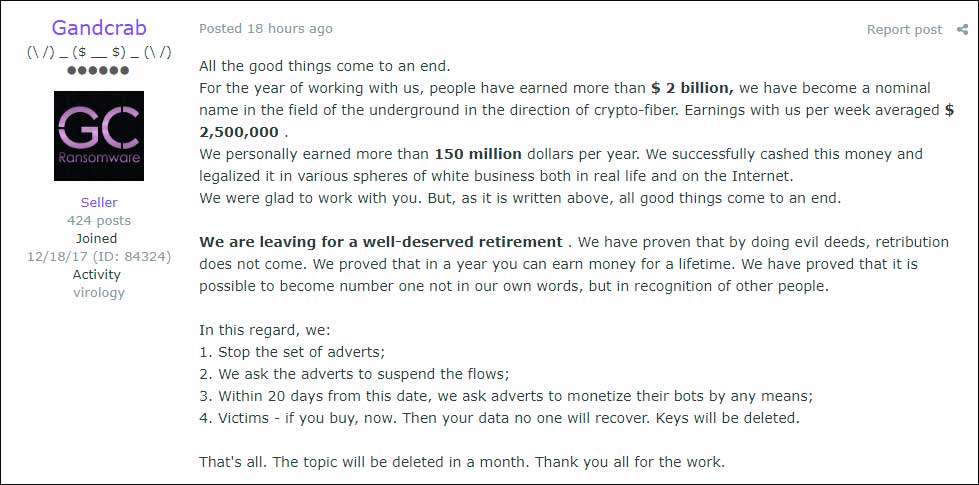
After GandCrab was shutdown, the FBI released the master decryption keys for the ransomware and BitDefender released a decryptor that allowed victims to recover their files for free.
It is not known how law enforcement obtained these keys, but it could have been through a seizure of one of the Tor payment servers.
After GrandCrab shut down, another ransomware variant called REvil, or Sodinokibi, was created to fill the void left behind.
It has been reported that there are code similarities and ties between the operators/affiliates of REvil ransomware and GandCrab.
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·