BOOK THIS SPACE FOR AD
ARTICLE ADMcAfee Web Gateway vulnerability affects several other vendors, researcher claims

Multiple web content inspection and antivirus gateways are opening up their enterprise users to data exfiltration, according to new research.
The finding, from Portuguese security researcher José Moreira, came after he dug deeper and found that the vulnerability (CVE-2019-3635) in McAfee’s Web Gateway he discovered last year also appeared to affect similar malware defense products from rival vendors Fortinet, Symantec, and Zscaler.
The Zscaler issue is still going through the disclosure process, while neither FortiGuard nor Symantec have been able to replicate the flaw.
Moreira is nonetheless sure of his ground and has published a technical blog post that, he says, features evidence to back up his claims.
‘This content is blocked’
McAfee‘s Web Gateway and similar products are essentially web proxies that intercept HTTP packets and block undesirable content, according to filtering rules,
Blocked content can include illegal or otherwise undesirable web content, as well as websites containing malware.
Any content these security products perceive as dangerous is replaced with a warning page.
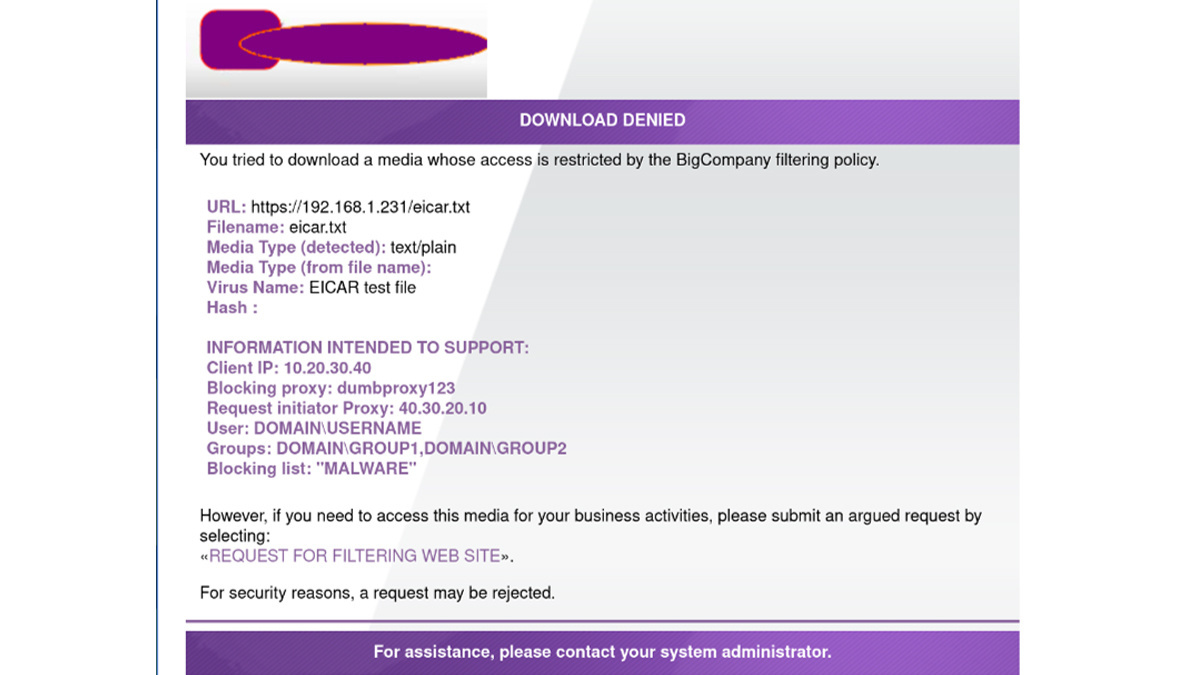
Secure web gateways throw up a message if a user attempts to visit a blocklisted site
This warning page contains sensitive information including Internal IP, proxy IP, Active Directory username, and more, Moreira discovered.
Moreira was able to develop a data exfiltration exploit that took advantage of this security weakness.
This was done by using a web page containing an iFrame pointing to an EICAR page (a test sequence of non-malicious characters that every antivirus product flags as ‘dangerous’), on a site under his control.
RELATED Netsweeper: Severe RCE vulnerability in content filtering system has been patched
Providing the iFrame and EICAR page were on the same domain, it was possible to siphon off sensitive information, as Moreira demonstrated.
“The main page embeds an iFrame that will contain the blocking message displaying all the sensitive data; then, the regular page will retrieve the iframe content using JavaScript and exfiltrate it to a server of ours,” he explains.
McAfee acknowledged the security flaw and resolved it with a patch released in August 2019.
Pwnage by proxy
In follow-up work since the original discovery, Moreira found that web proxy gateways with the same architecture as McAfee’s gateway were similarly vulnerable, including Bluecoat from Symantec.
Fortiguard from Fortinet had a slightly different security architecture, but this too could be bypassed using XMLHttpRequest and Cross-Origin Resource Sharing header trickery.
Not all tested products in the category were insecure.
Web content inspection gateways from Check Point, for example, were not vulnerable to this data exfiltration technique. This is because these products used a HTTP redirect rather than replacing unsafe content with a blocking message.
Read more of the latest security vulnerability news
“Checkpoint’s solution doesn’t replace the content by the blocking message, it replaces it by using an HTTP redirect, which redirects to another domain with properly secure HTTP headers,” Moreira writes.
“At this point, iFrames and XMLHttpRequests are not possible anymore.”
Moreira concludes that his research raises the provocative question of whether enterprise proxies are securing or exposing the corporate networks they are designed to protect.
“Although some vendors can argue that the blocking message is not providing any sensitive information (yet), those messages can be customized and include sensitive information within a network,” he said.
READ MORE Browser fingerprinting ‘more prevalent on the web now than ever before’ – research
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·