BOOK THIS SPACE FOR AD
ARTICLE AD
Image: Midjourney
Non-profit healthcare service provider Group Health Cooperative of South Central Wisconsin (GHC-SCW) has disclosed that a ransomware gang breached its network in January and stole documents containing the personal and medical information of over 500,000 individuals.
However, the attackers couldn't encrypt the compromised devices, which allowed GHC-SCW to secure its systems with the help of external cyber incident response experts and bring them back online after they were isolated to contain the breach.
"In the early morning hours of January 25th, 2024, GHC-SCW identified unauthorized access to their network. Their Information Technology (IT) Department purposefully isolated and secured their network, causing several of their systems to be temporarily unavailable," the healthcare organization said in a press release published on Tuesday.
"On February 9, 2024, during our investigation, we discovered indications that the attacker had copied some of GHC-SCW's data, which included protected health information (PHI). Our discovery was confirmed when the attacker, a foreign ransomware gang, contacted GHC-SCW claiming responsibility for the attack and stealing our data."
Health data stolen during the January ransomware attack includes affected individuals' names, addresses, telephone numbers, e-mail addresses, dates of birth and/or deaths, social security numbers, member numbers, and Medicare and/or Medicaid numbers.
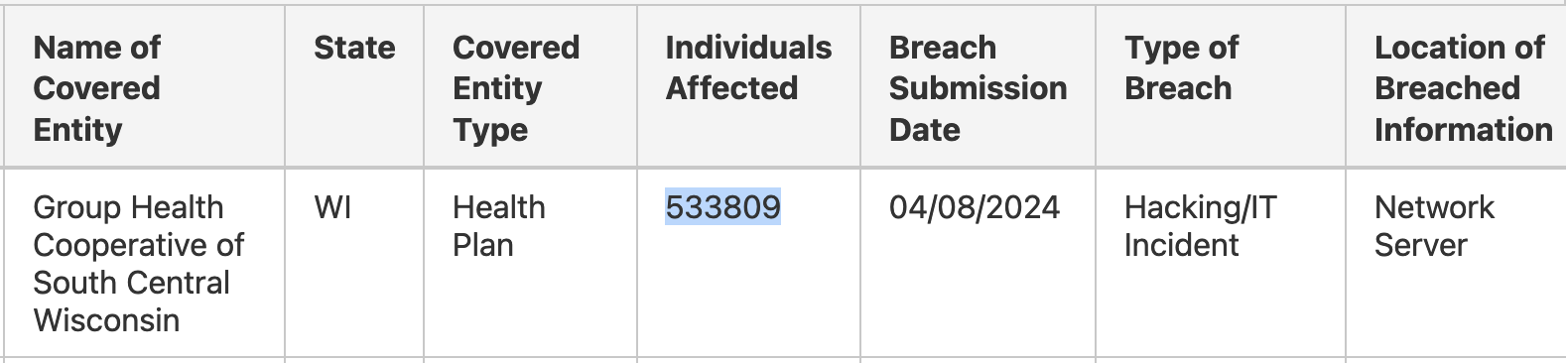
Although it didn't provide the exact number of affected people, additional information shared with the U.S. Department of Health and Human Services shows that the data breach impacted 533,809 individuals.
 GHC- SCW breach on HHS' portal (BleepingComputer)
GHC- SCW breach on HHS' portal (BleepingComputer)In response to the incident, GHC-SCW says it took security measures to prevent such breaches from happening again, including strengthening existing controls, data backup, and user training.
Impacted individuals are advised to monitor all communications from healthcare providers, including electronic messages, billing statements, and other communications, and to report any suspicious activity to GHC-SCW immediately.
GHC-SCW has yet to find evidence of the stolen information being used for malicious purposes.
Claimed by BlackSuit ransomware
While the Wisconsin-based healthcare non-profit didn't reveal the name of the threat group behind the January breach, the BlackSuit ransomware gang claimed the attack in March.
According to the attackers' claims, the stolen files also contain affected patients' financial information, employees' data, business contracts, and e-mail correspondence.
 GHC-SCW entry on BlackSuit leak site (BleepingComputer)
GHC-SCW entry on BlackSuit leak site (BleepingComputer)Even though BlackSuit's dark web leak site was first spotted last May and has since been updated with dozens of new victims, little is known about the group behind this ransomware operation.
In June, the highly active Royal ransomware gang—believed to be the direct successor of the notorious Conti cybercrime group—began testing a new encryptor called BlackSuit after rumors of a rebrand began surfacing in April.
Since then, Royal has rebranded into BlackSuit and reorganized into a more centralized operation, similar to the model they used when they were part of the Conti syndicate as Team 2 (Conti2).
The FBI and CISA revealed in a November joint advisory that the Royal ransomware gang had breached the networks of at least 350 organizations worldwide since September 2022 and linked the operation to more than $275 million in ransom demands.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·