DevOps platform GitLab has released software updates to address a critical security vulnerability that, if potentially exploited, could permit an adversary to seize control of accounts.
Tracked as CVE-2022-1162, the issue has a CVSS score of 9.1 and is said to have been discovered internally by the GitLab team.
"A hardcoded password was set for accounts registered using an OmniAuth provider (e.g., OAuth, LDAP, SAML) in GitLab CE/EE versions 14.7 prior to 14.7.7, 14.8 prior to 14.8.5, and 14.9 prior to 14.9.2 allowing attackers to potentially take over accounts," the company said in an advisory published on March 31.
GitLab, which has addressed the bug with the latest release of versions 14.9.2, 14.8.5, and 14.7.7 for GitLab Community Edition (CE) and Enterprise Edition (EE), also said it took the step of resetting the password of an unspecified number of users out of an abundance of caution.
"Our investigation shows no indication that users or accounts have been compromised," it added.
The company has also published a script that administrators of self-managed instances can run to single out accounts potentially impacted by CVE-2022-1162. After the affected accounts are identified, a password reset has been advised.
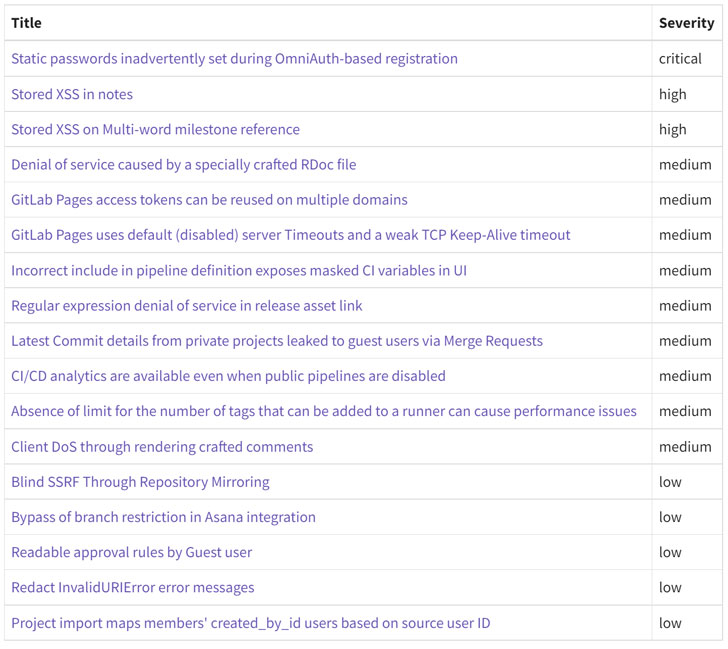
Also addressed by GitLab as part of the security update are two high-severity stored cross-site scripting (XSS) bugs (CVE-2022-1175 and CVE-2022-1190) as well as nine medium-severity flaws and five issues that are rated low in severity.
In light of the criticality of some of the issues, users running affected installations are highly recommended to upgrade to the latest version as soon as possible.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
140
2 years ago
140 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·