BOOK THIS SPACE FOR AD
ARTICLE ADNew SMS Stealer Alert! The massive campaign targets Android users globally. The scope of this campaign is staggering with over 107,000 malware samples identified so far. Learn how deceptive apps steal your data and how to secure your phone!
Zimperium researchers have uncovered a large-scale SMS stealer campaign dubbed SMS Stealer, targeting Android users across the globe. This malicious campaign leverages deceptive applications to infiltrate user devices and steal sensitive personal information.
Discovered and tracked by Zimperium’s zLabs since February 2022, the scope of this campaign is staggering with over 107,000 malware samples identified so far.
The attackers have used deceptive tactics, including malicious advertisements and Telegram bots, to trick victims into clicking on malicious links or downloading sideloaded applications.
According to Zimperium’s blog post, the targeted devices were infected by clicking on malicious web links and interacting with Telegram bots while searching for unofficial or free Android applications. The malware likely masquerades as legitimate applications impersonating popular utilities, games, or even financial services to trick users into installing them.
Researchers discovered a well-developed C&C platform with a user-defined geographic selection in one of their analyzed samples. Further probing revealed that various techniques are used to establish a C&C channel with victims. Early versions used Firebase, and in later versions, alternative methods like GitHub repositories were used for sharing C&C details. Malware also distributes malicious APKs on GitHub and most C&C servers use the Laravel Framework.
According to Zimperium’s research, over 95% of malware samples are unknown or unavailable, with over 600 global brands affected. Around 4,000 samples contained pre-embedded phone numbers in Android kits. 13 C&C servers were used to potentially receive stolen SMS messages. Over 2,600 Telegram bots were linked to the campaign.
Once installed, the malware intercepts incoming SMS messages, allowing the attackers to steal sensitive information like verification codes, login credentials, and one-time passwords (OTPs) received via SMS.
One-time passwords (OTPs) are crucial for online security, but they are also valuable to attackers as through mobile malware and clever tactics, it is possible to steal these codes and bypass their protection, allowing malicious infiltration into corporate networks and data.
The stolen information is then exfiltrated to the attacker’s servers, potentially enabling them to hijack user accounts, steal identities, or commit financial fraud.
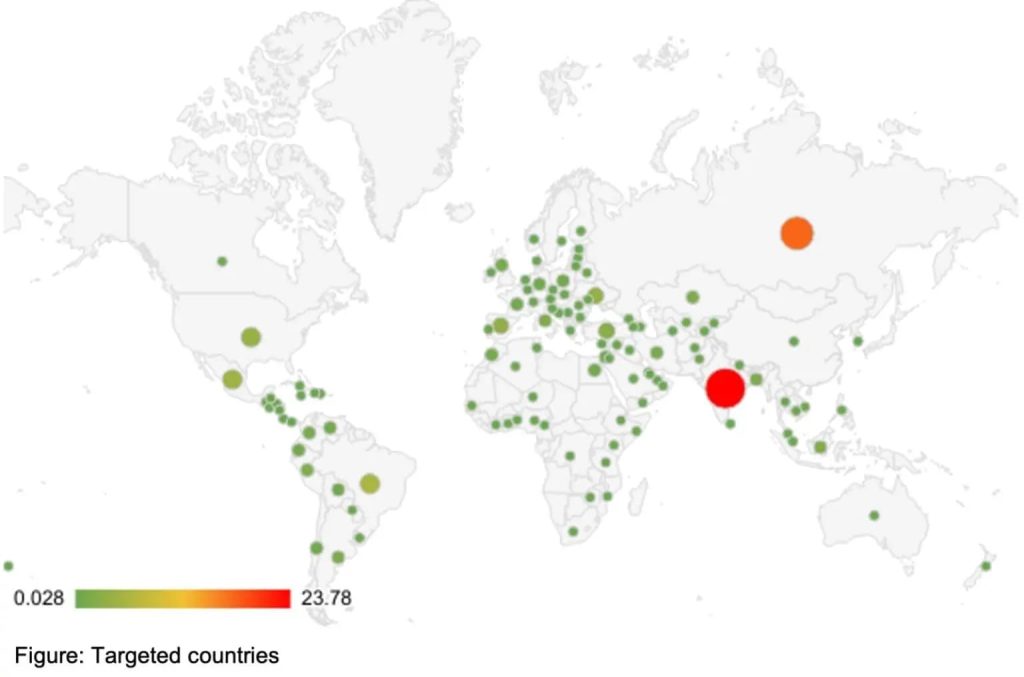 Targeted countries (Via: Zimperium)
Targeted countries (Via: Zimperium)
“These stolen credentials serve as a springboard for further fraudulent activities, such as creating fake accounts on popular services to launch phishing campaigns or social engineering attacks,” researchers noted.
While the exact attribution remains unknown, the widespread nature and sophisticated techniques employed suggest a group with considerable resources and technical expertise. Researchers discovered a connection between fastsms.su and the malware sample, establishing a financial motive behind this campaign.
Ken Dunham, Cyber Threat Director at Qualys Threat Research Unit commented on the new development stating “Subversion of mobile phones is of increasing interest to bad actors seeking to subvert weakly defended one-time password accounts and other sensitive information that can be compromised via SMS malware.“
“Text messages increasingly contain a wealth of sensitive information that can be used for secure authentication as well as extortion of a victim,“ Ken explained. “SMS malware, when combined with other identity access broker data, becomes a toxic cocktail for victims targeted by sophisticated adversaries.“
To protect yourself, download apps from trusted sources, be wary of unsolicited SMS, and treat messages urging immediate action with suspicion.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·