BOOK THIS SPACE FOR AD
ARTICLE ADLast year, Google Project Zero tracked a record 58 exploited-in-the-wild zero-day security holes.
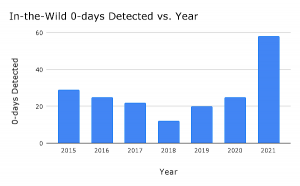
Google Project Zero reported 58 exploited zero-day vulnerabilities in 2021, a record in the short time the team of security researchers has been keeping tabs.
In a year-in-review report on the number instances a zero-day bug has been exploited in the wild, researchers noted the number a twofold jump in detected flaws since 2020. Google said 25 zero-day bugs in 2020 and 2019.
Google said the report highlights the importance of the security industry to take an aggressive approach at making it harder for attackers to exploit zero-day vulnerabilities.
“We heard over and over and over about how governments were targeting journalists, minoritized populations, politicians, human rights defenders, and even security researchers around the world. The decisions we make in the security and tech communities can have real impacts on society and our fellow humans’ lives,” researchers wrote.
The report referenced recent and past work by Citizen Lab, which earlier in the week shed light on multiple zero-day bugs exploited by commercial firms NSO Group and Candiru. Those firms were tied to efforts to use zero-day bugs in a multi-year campaign targeting autonomous region of Spain, called Catalonia.
 Google attributes the uptick in reported zero-day bugs, not to higher volumes of bugs, rather an increase in detection and disclosure. Also, not a revelation, is attacker methodology, researchers wrote.
Google attributes the uptick in reported zero-day bugs, not to higher volumes of bugs, rather an increase in detection and disclosure. Also, not a revelation, is attacker methodology, researchers wrote.
“Attackers are having success using the same bug patterns and exploitation techniques and going after the same attack surfaces,” wrote the author of the report Maddie Stone, security researchers with Google Project Zero.
While this was Google’s third-annual review of zero-days exploited in the wild, researchers said they have been tracking instances of zero-day bugs since mid-2014. “We’ve tracked publicly known in-the-wild 0-day exploits in this spreadsheet since mid-2014,” Stone wrote.
The important distinction in Google’s research is between known in-the-wild bugs and exploited in-the-wild bugs.
“While we often talk about the number of 0-day exploits used in-the-wild, what we’re actually discussing is the number of 0-day exploits detected and disclosed as in-the-wild,” she wrote.
Types of Zero-Days
Google reported of the 58 in-the-wild 0-days for the year, 39 were memory corruption vulnerabilities, 17 use-after-free, 6 out-of-bounds read/write bugs, 4 buffer overflow and the remaining 4 integer overflow.
Google also provided a list of platforms impacted, such as Chromium (Chrome) with 14 zero-days. “Chromium had a record high number of 0-days detected and disclosed in 2021 with 14. Out of these 14, 10 were renderer remote code execution bugs, 2 were sandbox escapes, 1 was an infoleak, and 1 was used to open a webpage in Android apps other than Google Chrome,” Stone wrote.
Seven zero-day bugs were found in the Safari WebKit component. Microsoft’s Internet Explorer had a reported four zero-days exploited in the wild. Microsoft’s Windows operating system had 10 zero-days and Apple had a total of 6, with 5 iOS zero-days exploited and macOS with one.
Hopes for 2022
Looking to 2022, Google Project Zero said it hoped to see progress on several fronts.
It proposed:
All vendors agree to disclose the in-the-wild exploitation status of vulnerabilities in their security bulletins. Exploit samples or detailed technical descriptions of the exploits are shared more widely. Continued concerted efforts on reducing memory corruption vulnerabilities or rendering them unexploitable. Launch mitigations that will significantly impact the exploitability of memory corruption vulnerabilities..png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·