BOOK THIS SPACE FOR AD
ARTICLE ADHey there, those(if any) who follow me and track my work know that I haven’t posted about my findings in a while(I haven’t been hunting a lot lately), it’s time to fix that!
Today, I’m sharing with you how a simple payload chained with Google Keep notes functionalities could have allowed me to block any Google User to access its keep notes.
Also, I’ll be sharing more of my findings(I miss doing write-ups) and start tweeting Threads also about Cybersecurity and Bug Bounty.
Stay tuned to hear more about some sweet bugs on Vale, Wickr, Acronis, Basecamp, and more.
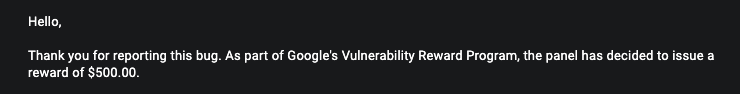
Why only $500 for such an impactful bug? DoS is rarely even accepted these days, I’m “lucky” they rewarded me.
While testing I noticed that Keep has a maximum number of characters that can be in a note. And it has filters to prevent an attacker to write more.
I figured that if I am able to bypass the filter, some great things could happen. And that’s what I did.
After a bit of testing, I found out that the very special character Ⱦ allowed me to write more than permitted. Why is that?
I don’t exactly know, I’d have to take a look at the code that processes the input server-side, but I do have a couple of opinions why:
There is an issue when processing weird Unicode stringsThe Ⱦ has special behavior(which is why I used this character): when processed server-side and put lowercase the Unicode of the character turns double. Meaning that when Ⱦ is submitted, it is counted as 1 by the client, instead is processed as 2 by the server who then stores 2 Ⱦ on keep. Meaning that if I send 1000 Ⱦs, they will be stored on keep as 2000 Ⱦs.A note with lots of Ⱦ chars would cause the Keep app to crash(on both mobile and desktop).
This was a game-changer for me that allowed my report to be rewarded. You can share notes on Keep. And you do not have to accept to open them, they are displayed on your Keep page as soon as I share them with you.
Meaning that I just needed to share with a mail address the note with the DoS payload and the Keep account associated with that email address was blocked.
Feb 26, 2021 08:23PM — Reported
Mar 1, 2021 12:22PM — Triaged
Mar 5, 2021 05:23PM — Validated
Mar 9, 2021 06:20PM — $500 Bounty Awarded
Also, don't forget to connect with me on Twitter where I’m just starting to post Threads about Crypto, Programming, and Bug Bounty!
.png)
 3 years ago
190
3 years ago
190 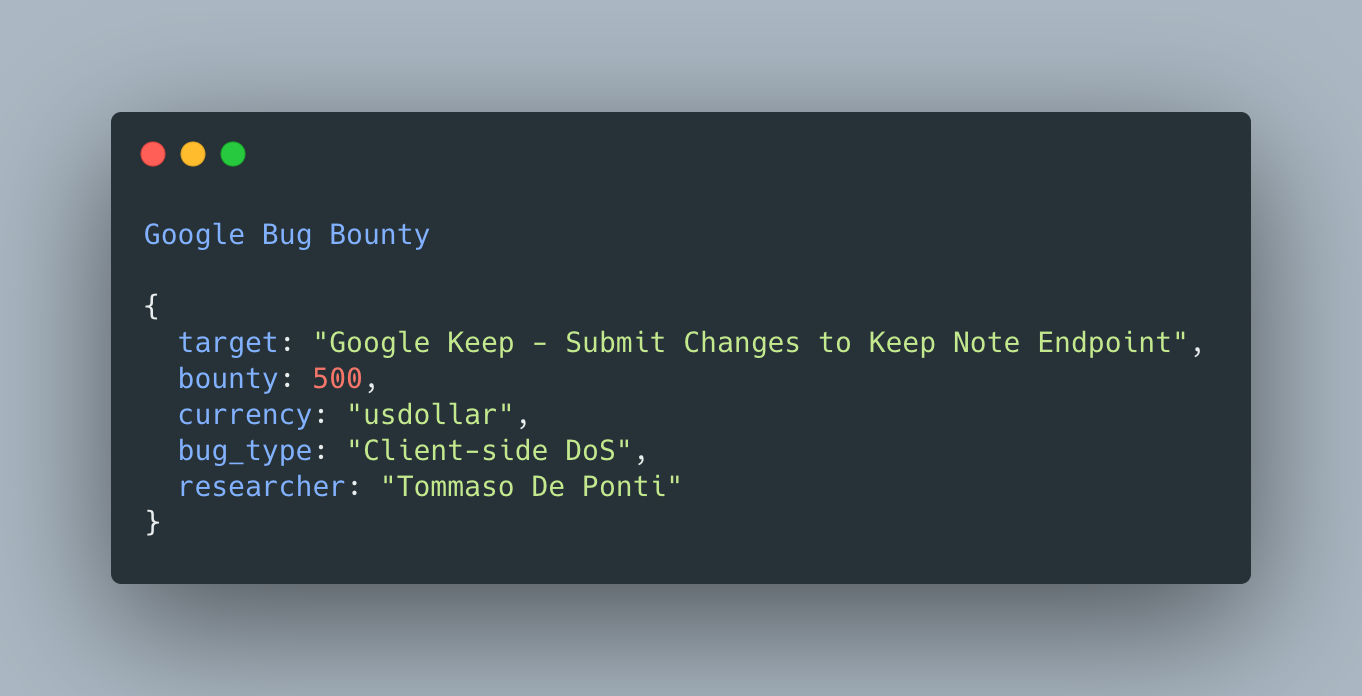















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·