BOOK THIS SPACE FOR AD
ARTICLE AD
Google's Threat Analysis Group (TAG) has discovered that threat actors exploited a zero-day vulnerability in Zimbra Collaboration email server to steal sensitive data from government systems in multiple countries.
Hackers leveraged a medium-severity security issue now identified as CVE-2023-37580 since June 29, nearly a month before the vendor addressed it in version 8.8.15 Patch 41of the software on July 25.
The flaw is an XSS (cross-site scripting) issue present in the Zimbra Classic Web Client.
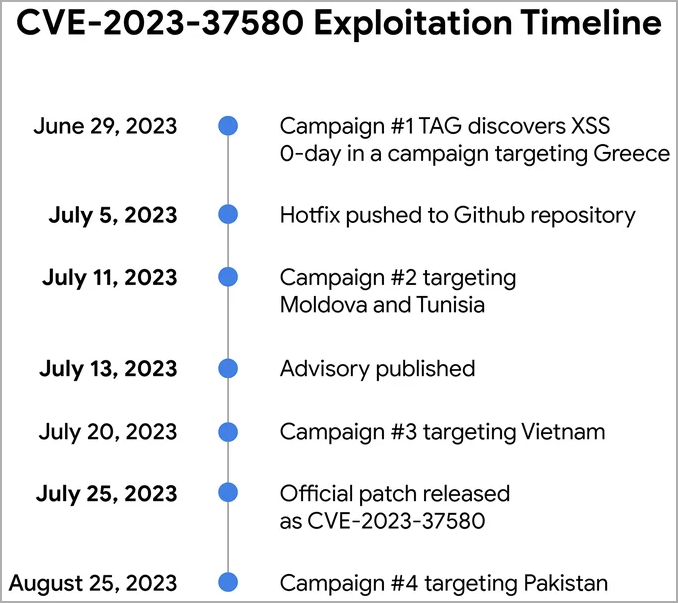
Attack and response timeline
According to Google's threat analysts, the threat actors exploited the vulnerability on government systems in Greece, Moldova, Tunisia, Vietnam, and Pakistan to steal email data, user credentials, and authentication tokens, perform email forwarding, and lead victims to phishing pages.
Google observed four distinct threat actors using the vulnerability that was unknown at the time of exploitation in late June 2023 against a government organization in Greece.
The attackers sent emails with a malicious URL that allowed email data exfiltration and enabled auto-forwarding to an attacker-controlled address.
Zimbra pushed an emergency hotfix on GitHub after Google analysts alerted the company of the observed compromises.
The second campaign was conducted on July 11 by a threat actor tracked as "Winter Vivern," who targeted government organizations in Moldova and Tunisia. The exploit URLs in this case loaded malicious JavaScript on the target systems.
On July 13, Zimbra published a security advisory recommending mitigations for the vulnerability but there was no note about hackers actively exploiting the bug.
A third campaign began on July 20 from an unidentified threat group targeting a Vietnamese government organization. These attacks used an exploit URL to direct victims to a phishing page.
Five days later Zimbra finally released an official patch for CVE-2023-37580, yet still omitting information about the active exploitation.
Google notes that the three threat actors exploited the vulnerability before the release of the official fix.
In a fourth campaign on August 25, a threat actor that likely learned the bug after the vendor addressed it, the bug was leveraged on the systems of a Pakistani government organization to steal Zimbra authentication tokens.
 (Google TAG)
(Google TAG)Google's report does not disclose many details about the attackers but still serves as a reminder about the importance of timely security updates, even when those concern medium-severity vulnerabilities because adversaries already on the system may use them to further their attack.
The exploitation of CVE-2023-37580 is one of the multiple examples of XXS flaws leveraged to attack mail servers, like CVE-2022-24682 and CVE-2023-5631, which impact Zimbra and Roundcube.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·