A team of security researchers from Google has demonstrated yet another variant of the Rowhammer attack that bypasses all current defenses to tamper with data stored in memory.
Dubbed "Half-Double," the new hammering technique hinges on the weak coupling between two memory rows that are not immediately adjacent to each other but one row removed.
"Unlike TRRespass, which exploits the blind spots of manufacturer-dependent defenses, Half-Double is an intrinsic property of the underlying silicon substrate," the researchers noted.
"This is likely an indication that the electrical coupling responsible for Rowhammer is a property of distance, effectively becoming stronger and longer-ranged as cell geometries shrink down. Distances greater than two are conceivable."
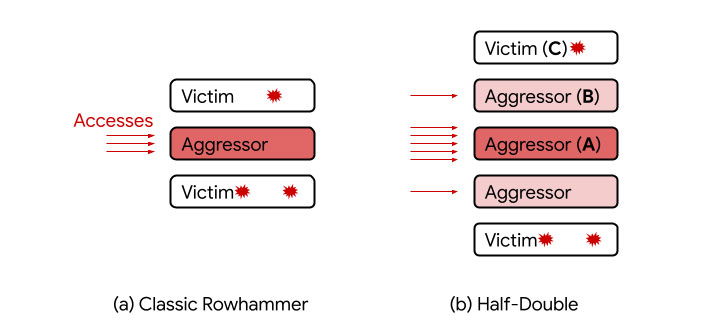
Rowhammer attacks are similar to speculative execution in that both break the fundamental security guarantees made by the underlying hardware. Discovered in 2014, Rowhammer refers to a class of DRAM vulnerabilities whereby repeated accesses to a memory row ("aggressor") can induce an electrical disturbance big enough to flip bits stored in an adjacent row ("victim"), thereby allowing untrusted code to escape its sandbox and take over control of the system.
While DRAM manufacturers deployed countermeasures like Target Row Refresh (TRR) to thwart such attacks, the mitigations have been limited to two immediate neighbors of an aggressor row, thus excluding memory cells at a two-row distance. The imperfect protections meant TRR defenses in DDR4 cards could be circumvented to stage new variants of Rowhammer attacks such as TRRespass and SMASH.
The distance-two assisted Rowhammer — aka Half-Double — now joins that list. "Given three consecutive rows A, B, and C, we were able to attack C by directing a very large number of accesses to A, along with just a handful (~dozens) to B," the researchers explained. In this new setup, A is the "far aggressor," B is the "near aggressor," and C is the "victim."
Google said it's currently working with the Joint Electron Device Engineering Council (JEDEC), an independent standardization body and semiconductor engineering trade organization, along with other industry partners, to identify possible solutions for Rowhammer exploits.
"To evaluate the effectiveness of a [SoC-level] mitigation, a DRAM vendor should test a mix of hammering distances rather than only testing at individual distances," the researchers said. "In other words, hammering a single row or a pair of sandwiching rows on the raw medium will not show this effect. Instead, pairs of rows on one or both sides of an intended victim need to be hammered."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
203
3 years ago
203 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·