BOOK THIS SPACE FOR AD
ARTICLE ADAt SAS@Home, Luta Security CEO Katie Moussouris stressed that bug bounty programs aren’t a ‘silver bullet’ for security teams.
SAS@Home 2020– After a Grindr security flaw was disclosed this week, the dating site promised it would launch a bug-bounty program in an effort to “[keep its] service secure.” But Katie Moussouris, CEO of Luta Security and a bug bounty program expert, warned at this week’s SAS@home virtual event that simply launching a bug-bounty program won’t result in better security.
The Grindr bug, which allowed attackers to launch password resets without accessing a user’s email inbox, made news headlines as it was extremely trivial to exploit. Speaking during a Tuesday virtual session, Moussouris said that if organizations have that level of “low-hanging fruit” when it comes to vulnerabilities, bug-bounty programs can sometimes pose more problems than they solve.
“We have a lot of hope for bug-bounty programs, but they’re not the ‘easy button’ we thought they were,” she said, speaking on Tuesday at SAS@Home, which is Kaspersky’s virtual Security Analyst Summit conference.
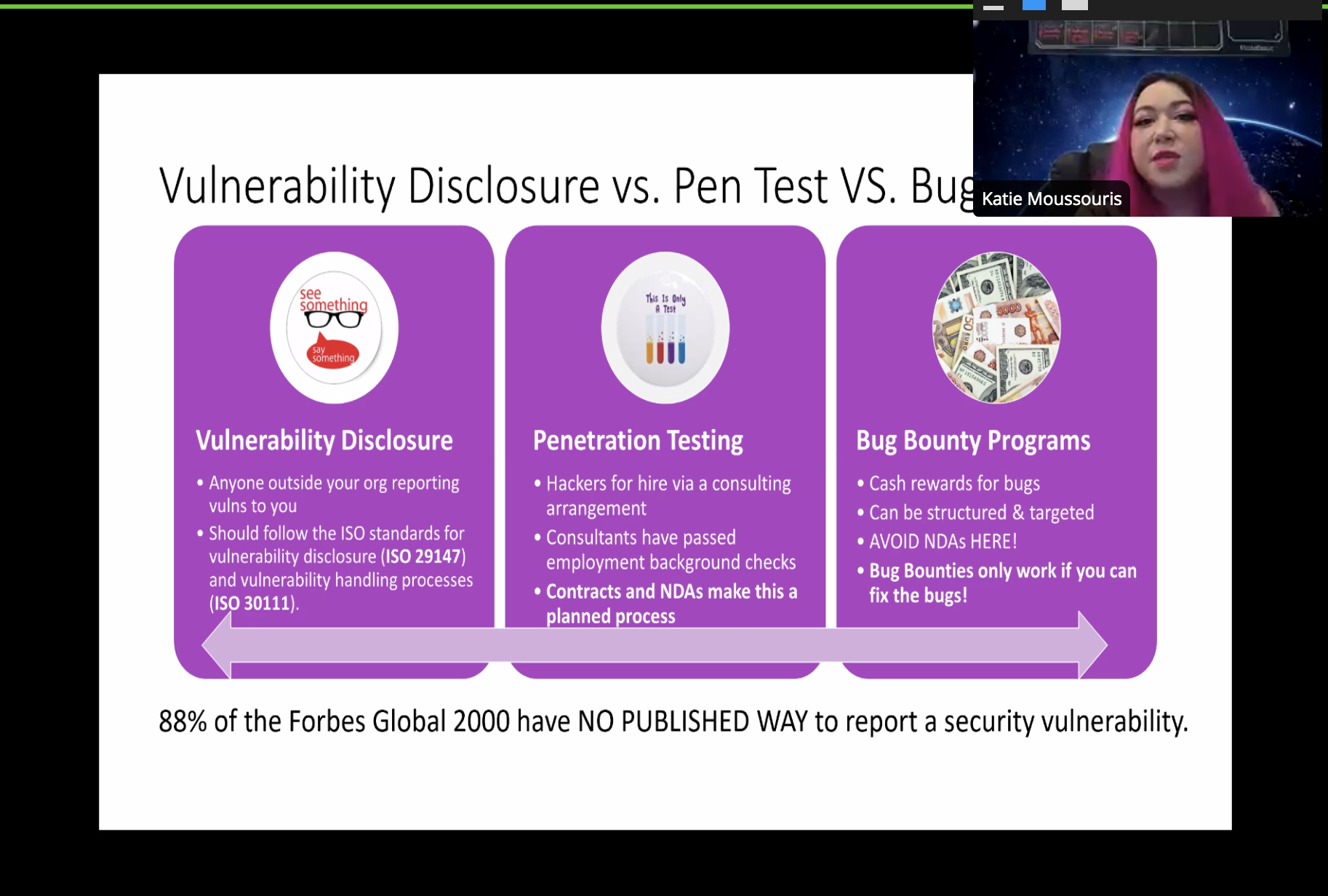
Grindr isn’t alone – many companies are looking to adopt, or have already adopted, bug-bounty programs or vulnerability-disclosure programs (VDPs). It’s important to distinguish the two: A bug-bounty program offers cash rewards for finding flaws (which in theory should then be fixed by the organization), while a VDP covers when a vulnerability is reported by a third party to an organization. Ideally, those involved would follow the ISO standards for vulnerability disclosure (ISO 29147) and vulnerability handling (ISO 30111) processes.
Katie Moussouris talks about the separate definitions of VDPs, bug-bounty programs and pentesting during SAS@Home.
But companies are rushing in to adopt bug-bounty programs and VDPs without first fleshing out important issues — whether that’s defining what’s in scope, looking at how an organization can handle an influx of vulnerabilities being reported, or properly training triage teams.
In December, for instance, a CISA directive was proposed that would require all U.S. agencies to develop and implement vulnerability disclosure processes for their internet-connected systems. While CISA recommended that agencies consider guidance around what’s in-scope and who to contact, Moussouris noted that holes remained in terms of setting up the back-end processes to receive reports, or gaining the resources that are necessary to fix the bugs reported.
Another potential issue that many organizations forget about is having the right tools and resources to deal with a potential influx of vulnerabilities reported, as seen with Zoom. While Zoom had a bug-bounty platform at one point, it wasn’t able to handle the security issues that came with a flood of remote workforces using its platform during the pandemic. After troves of security vulnerabilities were discovered in the online video conferencing platform, Zoom announced it would revamp its bug-bounty program with the help of Moussouris.
Moussouris recommended that organizations looking to implement bug-bounty programs and VDPs need to do the prerequisite work and manage their vulnerability processes internally. While working with Zoom for instance, she helped bolster the team’s internal resources so that it was better equipped to handle reports internally.
And finally, Moussouris recommended that companies remember that “security is an ongoing journey” and that there’s no silver bullet.
“People thinking VDP is a good first step for bug bounty programs have got it backwards,” she said. “Secure deployment [is] a good first step – not casting it out in the world and expecting results.”
On October 14 at 2 PM ET Get the latest information on the rising threats to retail e-commerce security and how to stop them. Register today for this FREE Threatpost webinar, “Retail Security: Magecart and the Rise of e-Commerce Threats.” Magecart and other threat actors are riding the rising wave of online retail usage and racking up big numbers of consumer victims. Find out how websites can avoid becoming the next compromise as we go into the holiday season. Join us Wednesday, Oct. 14, 2-3 PM ET for this LIVE webinar.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·