BOOK THIS SPACE FOR AD
ARTICLE AD
So the ip address of our secret crush here was 10.10.10.187, the first thing to do based on general principles was a nmap scan to see what we are dealing with here.

Things to quickly note here.
- it was running on the latest FTP server, so unless you the time i skills to find a 0 day, we have to look away asap.
- also running on a ssh server, we all know that is where our flags are hidden, so on to the next as well.
- oh sweet webserver.
opening the webserver showed us this beauty right here.

Clicking around did nothing, it was as STATIC as a whatsapp STICKER.
first thing i do whenever i visit a webserver, be it for CTFs, Bounty or Worldly things, i like to fiddle with robots.txt and doing just that gave me the little breakthrough i needed.

As you would have guessed, without hesitation i opened the admin-dir but got a 403 error. i felt insulted so i called a very good friend GoBuster, and as usual it delivered. i found two juicy directories namely.
- contacts.txt
- credentials.txt

There wasn’t much usefulness from the contact, but the credentials looked like what we need for the job. Right away i logged into the ftp server to see what and what we could play with.

Found this two files, every hackerman love the .sql extension. Downloaded them locally to my system then started tearing it apart.
I write this with Dissappointment, the sql file had nothing useful (insert sad screeching sounds), so i proceeded to the html file and lord it was a trove of massive data, bank information, passwords, usernames. But there was something that stood out and that was a folder called “utilities-scripts”, cd into this folder and i saw some php files but i took liking to this two.
- admin_tasks.php
- db_admin.php

wEB InTerFaCE to Admin task, i promptly tried to opened it on my browser finally something of essence.

Oh wait, Rabbit hole, seriously though? at this point i was getting tired proceeded to check the db_admin.php.

Okay i really hit a very big luck here, during my childish and dark days whenever we saw something like this, it was mostly inside functions.php or database.php and when we something like this, we fire it straight up to Adminer.php i decided to push my luck , open adminer.php on my browser and right in my face i was blessed with this beautiful interface.
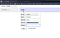
But none of the credentials was working, what could be wrong? ha, the version, so i used to hunt C2 and backdoors, many of this bad boys usually upload adminer.php to edit database info and what, however this pacticular version had a serious flaw that enabled you to read local files on the server, haven’t played with this so much in the past i knew what must be done.
You can read more of the technicalities here, basically Create a local server with remote access and try to login into the adminer dashboard, find the local files and take a peek into it’s content. Doing this we found a ssh credentials Waldo:&<h5b~yK3F#{PaPB&dA}{H> without delay i tried to login and i was successful and we got User.

.png)
 4 years ago
182
4 years ago
182 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·