BOOK THIS SPACE FOR AD
ARTICLE ADLimeVPN has confirmed a data incident, and meanwhile its website has been knocked offline.
The VPN provider known as LimeVPN has been hit with a hack affecting 69,400 user records, according to researchers.
A hacker claims to have stolen the company’s entire customer database before knocking its website offline (Threatpost confirmed that as of press time, the website was down). The stolen records consist of user names, passwords in plain text, IP addresses and billing information, according to PrivacySharks. Researchers added the attack also included public and private keys of LimeVPN users.
“The hacker informed us that they have the private keys of every user, which is a serious security issue as it means they can easily decrypt every LimeVPN user’s traffic,” the firm said in a posting.
The potential for decryption is worrying, experts say, given that VPNs tunnel all of their users’ internet traffic, which is a potential gold mine of information for cyberattackers.
The whole purported cache has been put up for sale on the hacker destination RaidForums. The hacker, who goes by the handle “slashx,” originally said the database consisted of 10,000 records for $400 (on Tuesday) before expanding the tally (on Wednesday). Slashx told researchers that the heist was carried out via a security breach rather than any connection with an insider threat or older hack.
Then, on Thursday, the site went offline — with an apparent malware infection in play. “Worryingly, our access was blocked by Malwarebytes [antivirus protection] due to a potential trojan found on the site,” PrivacySharks said.
LimeVPN Confirms Breach to Researchers
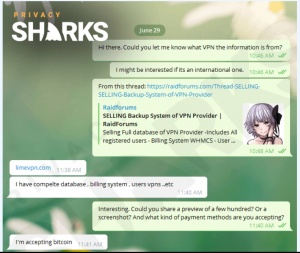
Telegram chat with “slashx”. Source: PrivacySharks
A PrivacySharks spokesperson told Threatpost that LimeVPN confirmed that there has been a data incident, and that the hacker who stole the database also claimed responsibility for the site being down. And the firm RestorePrivacy, which separately confirmed the leak, noted that LimeVPN told it that “our backup server has been hacked” and that it has “reset our access credentials and started a system audit.”
Threatpost has also reached out to LimeVPN for comment, but no response has yet been forthcoming.
Sample Review of Stolen Data
Both sets of researchers made contact with the perpetrator and reviewed samples of the alleged collected data.
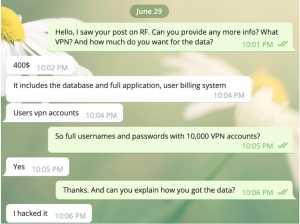
Another chat. Source: RestorePrivacy
When analyzing the available sample data provided by slashx, RestorePrivacy researchers noticed that transaction details for users buying the service were available (as in dollar amounts and payment method), but actual payment-card data or bank details are not included.
“This is because the VPN uses a third-party payment processor called WHMCS,” the firm noted. “However, the hacker claims to have obtained the entire WHMCS database with the LimeVPN hack.”
Some of the transactions in the sample date up to this week, and include the full names of current subscribers, both firms found.
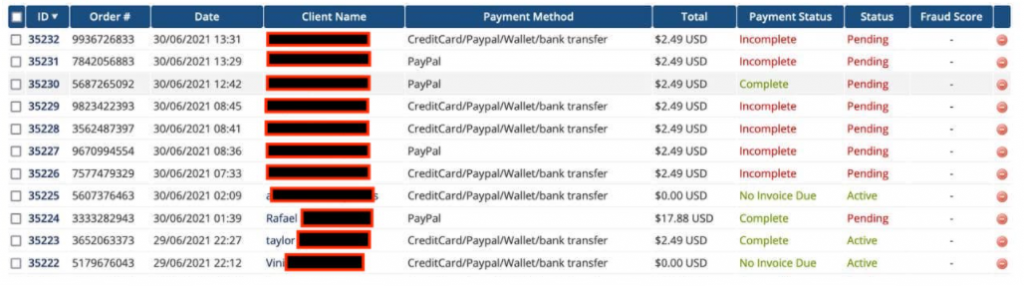
Source: RestorePrivacy
“Even though LimeVPN is not a large provider like Surfshark or NordVPN, the fact that its entire database was scraped raises the question of security among VPN providers,” Cliff Durward, PrivacySharks’ head of security, told Threatpost. “Although most VPN companies, like LimeVPN, employ no-logs policies, identifiable data such as email addresses and payment information can still be stolen and sold if security breaches occur.”
No Logs?
LimeVPN, like many other providers, advertises a log-less service, meaning that it doesn’t track its users or keep personal data on them. But the very existence of the allegedly stolen records and the database calls that proposition into question, researchers said.
“It is not entirely clear from the data we were provided if LimeVPN is collecting usage or connection logs from their users,” according to RestorePrivacy. “And we were not willing to pay the $400 in Bitcoin to see all data. Nonetheless, this incident looks to be a major blow to the VPN service’s reputation.”
PrivacySharks had a similar take: “LimeVPN’s no-logs policy will also be thrown into question since this massive data breach may lead some users to question how much of their data the company actually stores. Without an independent audit of the provider’s privacy policy, the phrase ‘no-logs’ doesn’t have much weight, and the current situation will cause a lot of skepticism from customers.”
LimeVPN did not respond to Threatpost’s query about its logging policies and practices.
What LimeVPN Users Should Do
As with the recent LinkedIn data-scraping incident, the information allegedly contained in the collection could potentially be used to carry out a variety of social-engineering attacks, including mounting phishing efforts and more.
“Hackers can take information to build profiles on individuals, making it easier to find out more details, leading to identity theft, fraud or scams,” PrivacySharks noted. “For this reason, it is important to be vigilant when creating online accounts with your personal details.”
PrivacySharks recommended that users change their passwords and freeze/replace their credit cards. It’s also a good idea to change passwords and activate two-factor authentication on other accounts that may use the same credentials, and consider using “burner” email addresses for high-risk accounts.
Check out our free upcoming live and on-demand webinar events – unique, dynamic discussions with cybersecurity experts and the Threatpost community.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·