Security is only as strong as the weakest link. As further proof of this, Apple released an update to macOS operating systems to address an actively exploited zero-day vulnerability that could circumvent all security protections, thus permitting unapproved software to run on Macs.
The macOS flaw, identified as CVE-2021-30657, was discovered and reported to Apple by security engineer Cedric Owens on March 25, 2021.
"An unsigned, unnotarized, script-based proof of concept application [...] could trivially and reliably sidestep all of macOS's relevant security mechanisms (File Quarantine, Gatekeeper, and Notarization Requirements), even on a fully patched M1 macOS system," security researcher Patrick Wardle explained in a write-up. "Armed with such a capability macOS malware authors could (and are) returning to their proven methods of targeting and infecting macOS users."
Apple's macOS comes with a feature called Gatekeeper, which allows only trusted apps to be run by ensuring that the software has been signed by the App Store or by a registered developer and has cleared an automated process called "app notarization" that scans the software for malicious content.
But the new flaw uncovered by Owens could enable an adversary to craft a rogue application in a manner that would deceive the Gatekeeper service and get executed without triggering any security warning. The trickery involves packaging a malicious shell script as a "double-clickable app" so that the malware could be double-clicked and run like an app.
"It's an app in the sense that you can double click it and macOS views it as an app when you right click -> Get Info on the payload," Owens said. "Yet it's also shell script in that shell scripts are not checked by Gatekeeper even if the quarantine attribute is present."
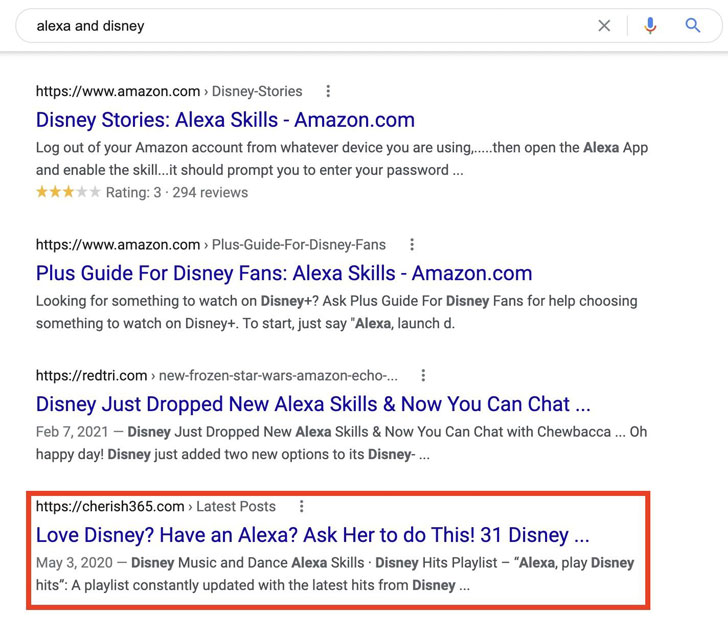
According to macOS security firm Jamf, the threat actor behind Shlayer malware has been abusing this Gatekeeper bypass vulnerability as early as January 9, 2021. Distributed via a technique called search engine poisoning or spamdexing, Shlayer accounts for almost 30% of all detections on the macOS platform, with one in ten systems encountering the adware at least once, according to Kaspersky statistics for 2019.
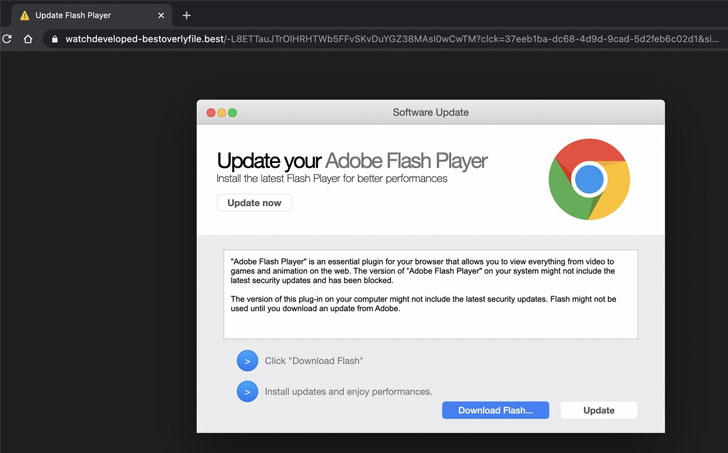
The attack works by manipulating search engine results to surface malicious links that, when clicked, redirects users to a web page that prompts users to download a seemingly benign app update for out-of-date software, which in this campaign, is a bash script designed to retrieve next-stage payloads, including Bundlore adware stealthily. Troublingly, this infection scheme could be leveraged to deliver more advanced threats such as surveillanceware and ransomware.
In addition to the aforementioned vulnerability, Monday's updates also address a critical flaw in WebKit Storage (tracked as CVE-2021-30661) that concerns an arbitrary code execution flaw in iOS, macOS, tvOS, and watchOS when processing maliciously crafted web content.
"Apple is aware of a report that this issue may have been actively exploited," the company said in a security document, adding it addressed the use-after-free weakness with improved memory management.
Aside from these updates, Apple has also released iCloud for Windows 12.3 with patches for four security issues in WebKit and WebRTC, among others, that could allow an attacker to cross-site scripting (XSS) attacks (CVE-2021-1825) and corrupt kernel memory (CVE-2020-7463).
Users of Apple devices are recommended to update to the latest versions to mitigate the risk associated with the flaws.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
174
3 years ago
174 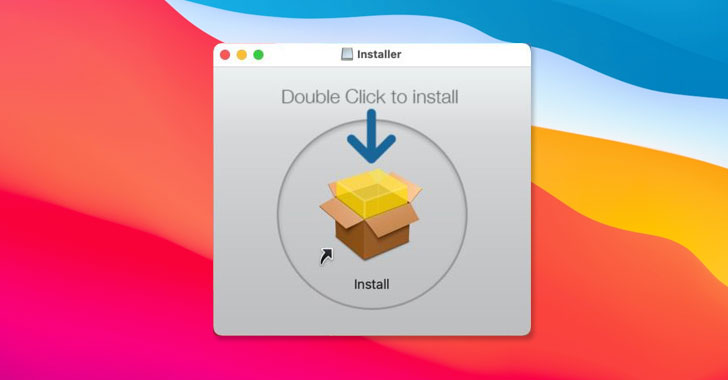

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·