The Metropolitan Police Department (MPD) of the District of Columbia has become the latest high-profile government agency to fall victim to a ransomware attack.
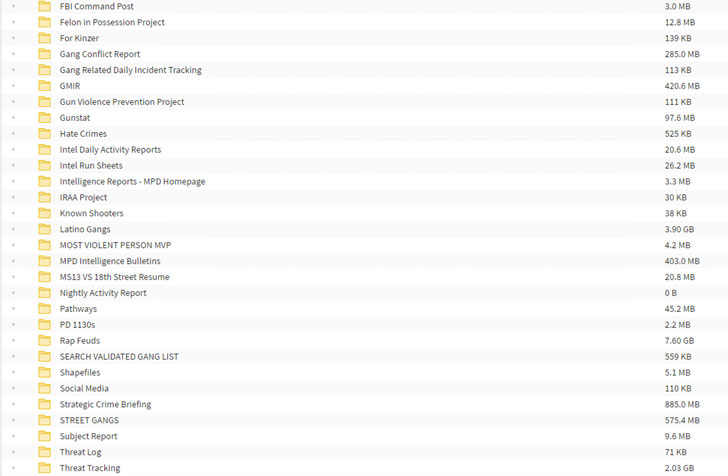
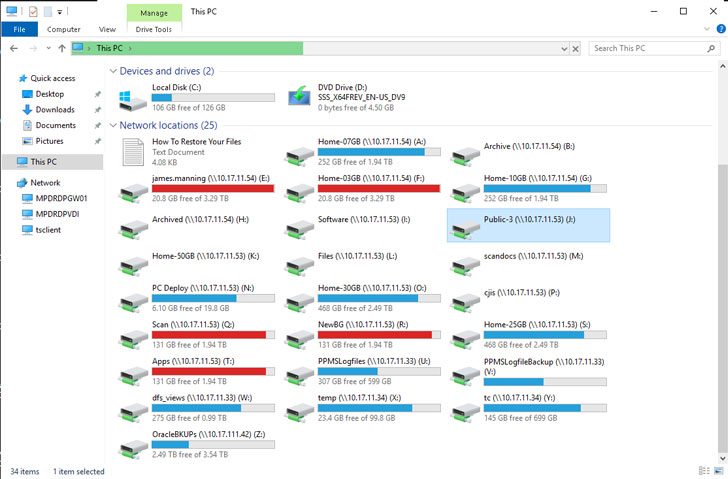
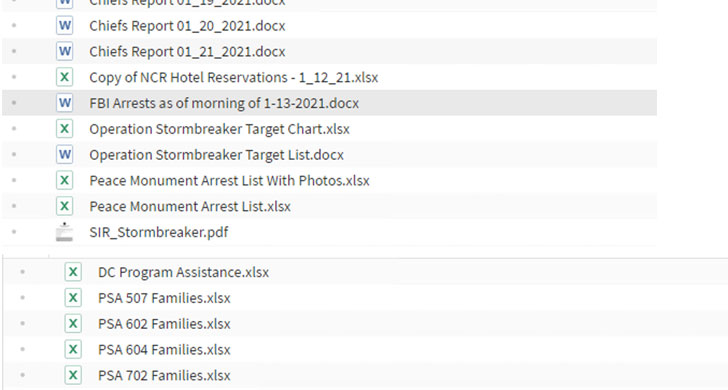
The Babuk Locker gang claimed in a post on the dark web that they had compromised the DC Police's networks and stolen 250 GB of unencrypted files. Screenshots shared by the group, and seen by The Hacker News, include various folders containing what appears to be investigation reports, arrests, disciplinary actions, and other intelligence briefings.
Also called the DC Police, the MPD is the primary law enforcement agency for the District of Columbia in the U.S.
The ransomware gang has given the department three days to heed to their ransom demand or risk leaking sensitive files that could expose police informants to criminal gangs.
"Hello! Even an institution such as DC can be threatened, we have downloaded a sufficient amount of information from your internal networks, and we advise you to contact us as soon as possible, to prevent leakage, if no response is received within 3 days, we will start to contact gangs in order to drain the informants, we will continue to attack the state sector of the usa, fbi csa, we find 0 day before you, even larger attacks await you soon," the ransomware group said on their data leak site.
Babuk Locker is a relative newcomer in the ransomware landscape, with the group targeting transportation, healthcare, plastic, electronics, and agricultural sectors across the U.S., U.K., U.A.E., China, India, South Africa, Spain, Germany, and Italy at least since the beginning of 2021. The syndicate is also known for attacking Linux-based systems such as VMware ESXi.
"The Babuk gang highlighted the key problem that all organizations face when confronting threats, and that is speed," Cymulate CTO Avihai Ben-Yossef said. "The time it takes for known vulnerabilities to get patched on all systems is too long. Defenders that rely on manual security testing methodologies are unable to match the pace of threat actors in finding security gaps and fixing them."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
180
3 years ago
180 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·