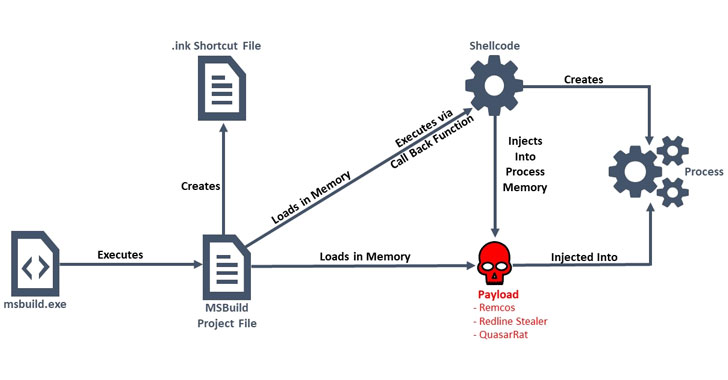
Threat actors are abusing Microsoft Build Engine (MSBuild) to filelessly deliver remote access trojans and password-stealing malware on targeted Windows systems.
The actively ongoing campaign is said to have emerged last month, researchers from cybersecurity firm Anomali said on Thursday, adding the malicious build files came embedded with encoded executables and shellcode that deploy backdoors, allowing the adversaries to take control of the victims' machines and steal sensitive information.
MSBuild is an open-source build tool for .NET and Visual Studio developed by Microsoft that allows for compiling source code, packaging, testing, deploying applications.
In using MSBuild to filelessly compromise a machine, the idea is to stay under the radar and thwart detection, as such malware makes use of a legitimate application to load the attack code into memory, thereby leaving no traces of infection on the system and giving attackers a high level of stealth.
As of writing, only two security vendors flag one of the MSBuild .proj files ("vwnfmo.lnk") as malicious, while a second sample ("72214c84e2.proj") uploaded to VirusTotal on April 18 remains undetected by every anti-malware engine. The majority of the samples analyzed by Anomali were found to deliver the Remcos RAT, with a few others also delivering the Quasar RAT and RedLine Stealer.
Remcos (aka Remote Control and Surveillance software), once installed, grants full access to the remote adversary, its features ranging from capturing keystrokes to executing arbitrary commands and recording microphones and webcams, while Quasar is an open-source .NET-based RAT capable of keylogging, password stealing, among others. Redline Stealer, as the name indicates, is a commodity malware that harvests credentials from browsers, VPNs, and messaging clients, in addition to stealing passwords and wallets associated with cryptocurrency apps.
"The threat actors behind this campaign used fileless delivery as a way to bypass security measures, and this technique is used by actors for a variety of objectives and motivations," Anomali researchers Tara Gould and Gage Mele said. "This campaign highlights that reliance on antivirus software alone is insufficient for cyber defense, and the use of legitimate code to hide malware from antivirus technology is effective and growing exponentially."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
289
3 years ago
289 















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·