BOOK THIS SPACE FOR AD
ARTICLE AD
Threat actors are taking advantage of the massive popularity of the Hamster Kombat game, targeting players with fake Android and Windows software that install spyware and information-stealing malware.
Hamster Kombat is a clicker mobile game for Android where players earn fictional currency by completing simple tasks, primarily by tapping the screen.
Launched in March 2024, the game has already garnered significant interest due to the potential to earn a new TON-based crypto token tied to it, scheduled to be introduced later this year.
Hamster Kombat is Telegram-based, requiring players to join its channel on Telegram, scan a QR code provided by a bot, and then launch a web app on their Android devices to play it.
The game has seen massive growth since its launch, with over 250 million players and 53 million users on it's Telegram channel.
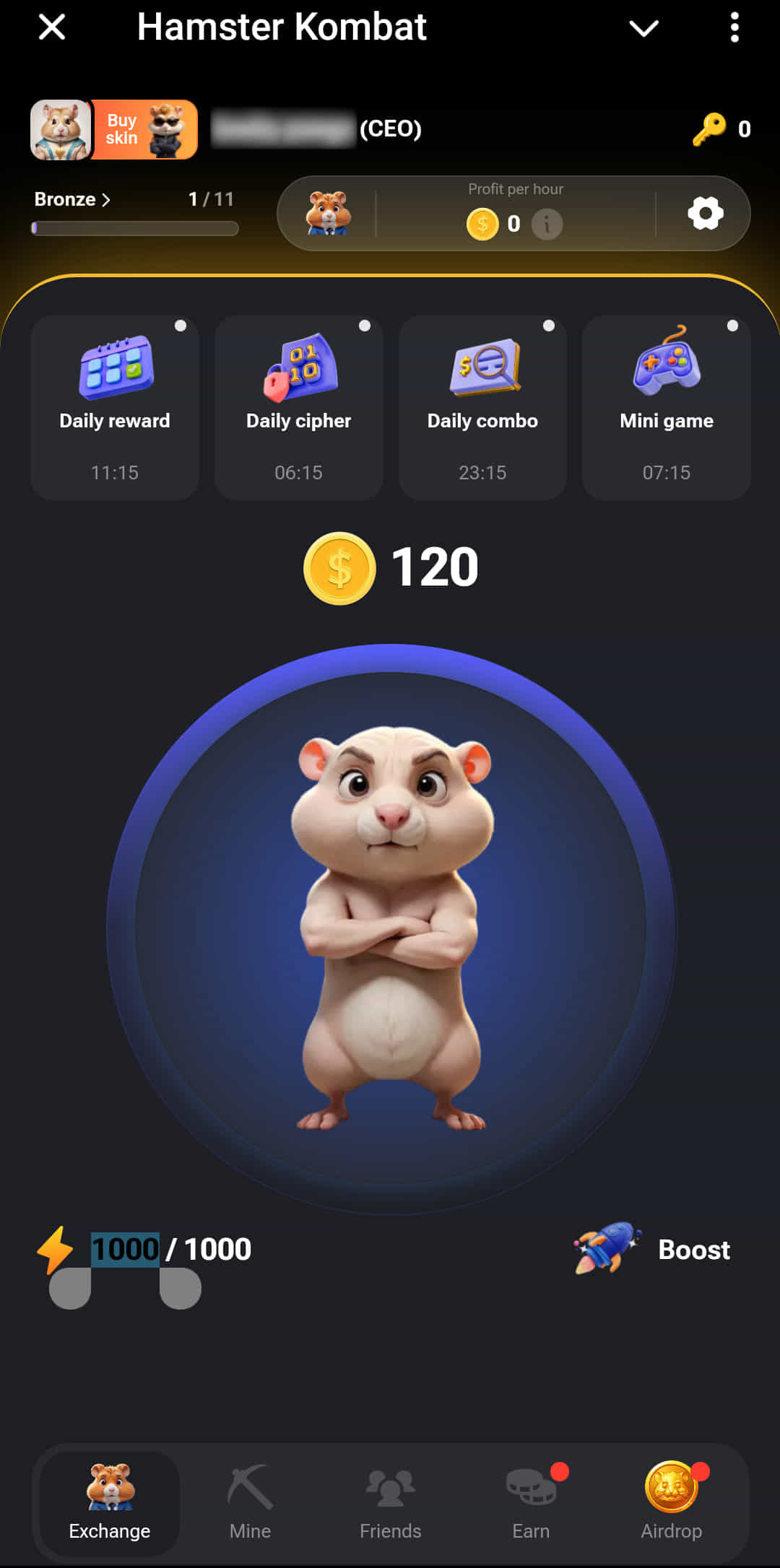 The Hamster Kombat app interface
The Hamster Kombat app interfaceSource: BleepingComputer
Targeting the "hamsters"
Although a clone app on Google Play named 'Hamster Kombat – Earn Crypto,' the genuine project isn't available on any official channels but Telegram, making those interested in joining easy prey for cybercriminals and scammers.
ESET has found multiple cases where threat actors use the Hamster Kombat game as bait, even extending to other platforms beyond Android, like Windows.
The first risk lies in Telegram, where various Hamster-branded channels distribute Android malware to users searching for the official channel.
ESET highlights a channel named 'HAMSTER EASY' that distributes the Ratel Android spyware as an APK file ('Hamster.apk') that does not contain any legitimate functionality.
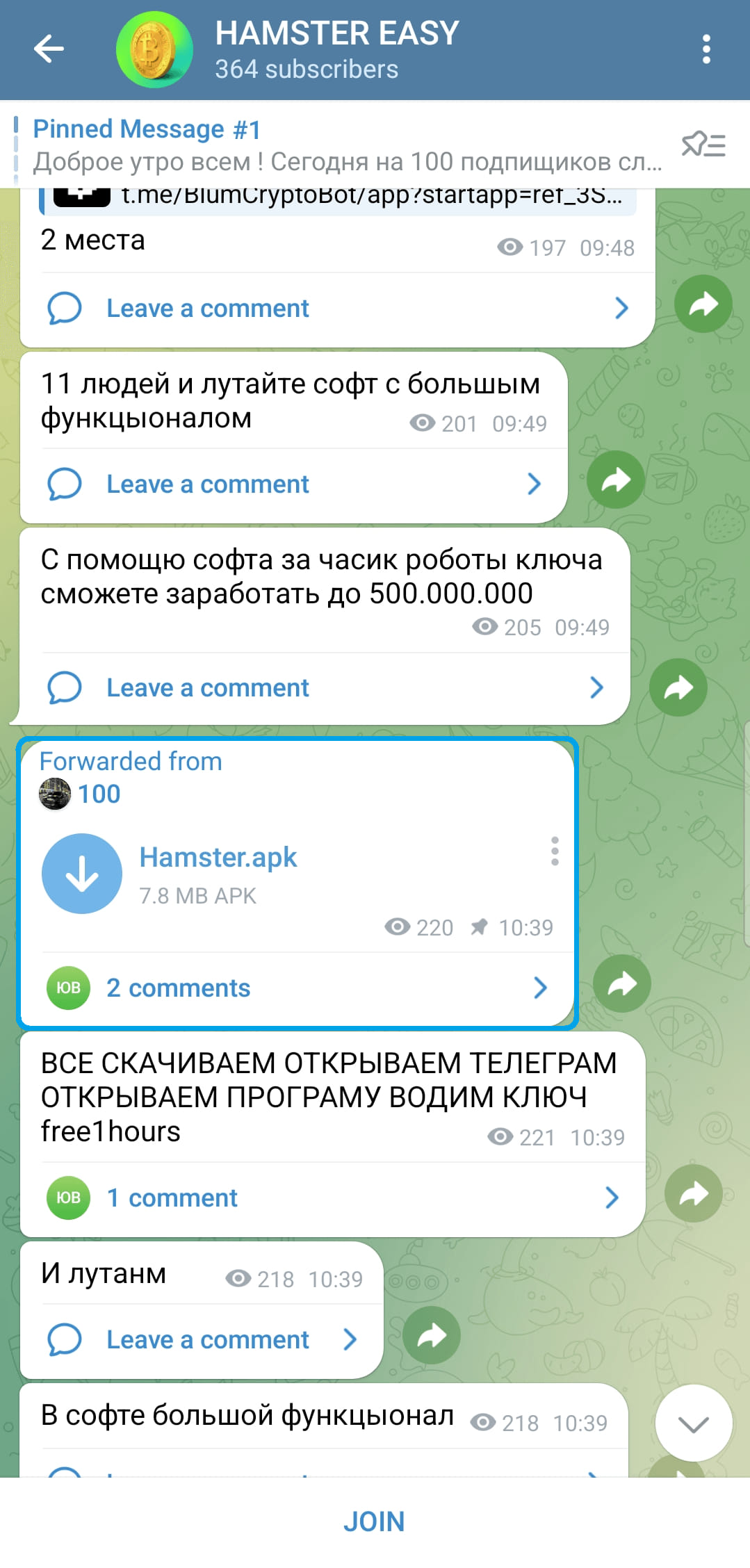 Malicious APK distributed on Telegram
Malicious APK distributed on TelegramSource: ESET
Ratel can intercept SMS and device notifications, but it's used mainly to subscribe the victim to premium services, from which the malware operators get a cut.
The malware hides notifications from 200 apps, so the victim never realizes they have subscribed to various premium services.
Another malicious campaign uses fake websites like 'hamsterkombat-ua.pro' and 'hamsterkombat-win.pro' that claim to offer the game but instead redirect visitors to advertisements so they can generate money.
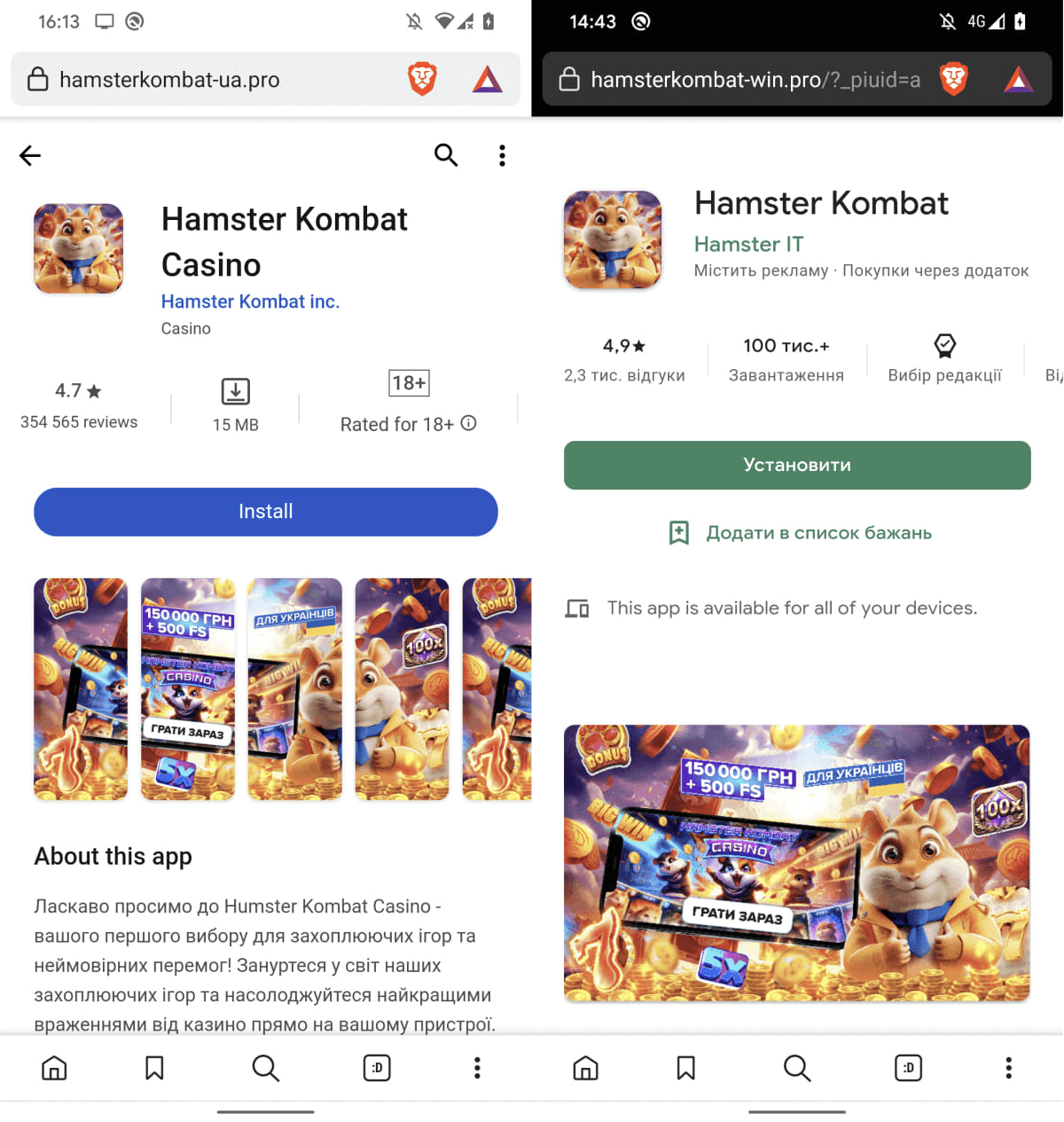 Fake sites mimicking the Google Play interface
Fake sites mimicking the Google Play interfaceSource: ESET
ESET notes that Hamster Kombat-branded scams also target Windows users, with Lumma Stealer being distributed through malicious GitHub repositories claiming to offer farming bots for the cryptocurrency game.
"The GitHub repositories we found either had the malware available directly in the release files, or contained links to download it from external file-sharing services," reads ESET's report.
"We identified three different versions of Lumma Stealer cryptors lurking within the repositories: C++ applications, Go applications, and Python applications."
Of the three, the Python version was prepared with better care, even featuring a graphical installer to further the deception until the end of the malware installation process.
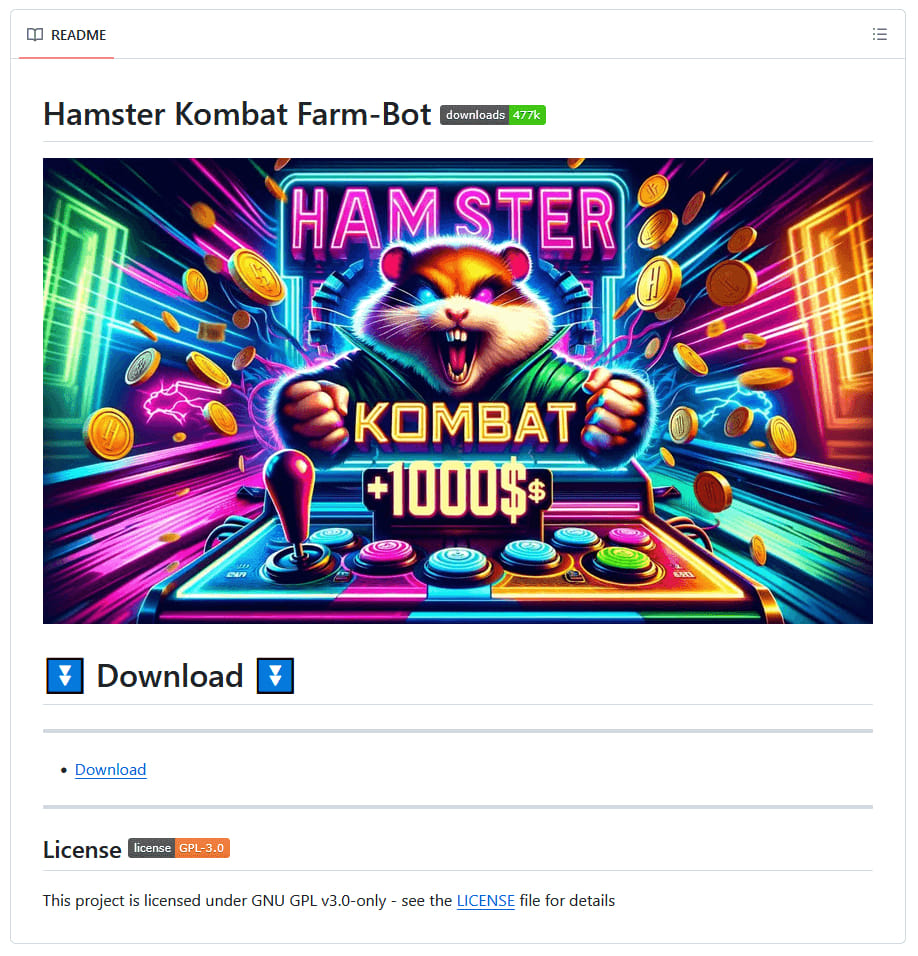 Fake Hamster Kombat farmer bot spreading Lumma Stealer
Fake Hamster Kombat farmer bot spreading Lumma StealerSource: ESET
Note of caution
If you're interested in the Hamster Kombat project, you should get it straight from its official channel on Telegram or visit the project's website.
However, it should be noted that even the genuine game itself has not been scrutinized for its security, as it is not on Google Play or the App Store. The project's whitepaper hasn't been published yet, and the token launch promises remain unfulfilled.
It should also be noted that the clone app on Google Play has several reports claiming that it scams users asking for withdrawal fees and never performs the money withdrawal.
People should treat any Hamster Kombat copycat apps distributed via any platform or method with distrust, as even if not all contain malware, they're almost definitely scams.
Decrypt.co has compiled a list of cryptocurrency gaming projects that launched tokens in 2024 and which have a functional system in place, so if you're interested in this concept, you may want to consider investing your time on those instead.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·