BOOK THIS SPACE FOR AD
ARTICLE AD
Adam Bannister
09 September 2021 at 15:07 UTC
Updated: 09 September 2021 at 15:56 UTC
Project maintainers patch integer overflow flaw that has various potentially damaging outcomes

Security researchers have disclosed a HTTP request smuggling vulnerability in HAProxy, the popular open source load balancer.
Users of HAProxy, which ships with most mainstream Linux distributions and is particularly geared towards use by high traffic websites, have been urged to update their systems.
RECOMMENDED Black Hat USA: HTTP/2 flaws expose organizations to fresh wave of request smuggling attacks
Researchers at DevOps platform JFrog demonstrated how an integer overflow flaw (CVE-2021-40346) can be abused to perform HTTP request smuggling attacks that bypass any access control lists (ACLs) defined in HAProxy.
Contingent on front- and back-end server configurations, attacks could also potentially see adversaries hijack user sessions, access or modify sensitive data, or exploit reflected XSS (cross-site scripting) vulnerabilities without user interaction, according to JFrog.
HTTP request smuggling explained
HTTP request smuggling, which first emerged in 2005, interferes with how websites process sequences of HTTP requests received from users.
Load balancers (aka reverse proxies) typically forward multiple HTTP requests, consecutively, to back-end servers over the same network connection.
If front- and back-end servers disagree about the boundaries separating requests then they can also interpret malicious, ambiguous requests divergently – with potentially devastating results.
Smuggling via integer overflow
The technique is typically executed by “supplying both the and headers with contradicting lengths in the same request and aiming for parsing inconsistencies between the frontend and backend servers,” reads a blog post penned by Ori Hollander and Or Peles of JFrog-owned software security automation platform Vdoo.
“In our case, however, the attack was made possible by utilizing an integer overflow vulnerability that allowed reaching an unexpected state in HAProxy while parsing an HTTP request – specifically – in the logic that deals with headers.”
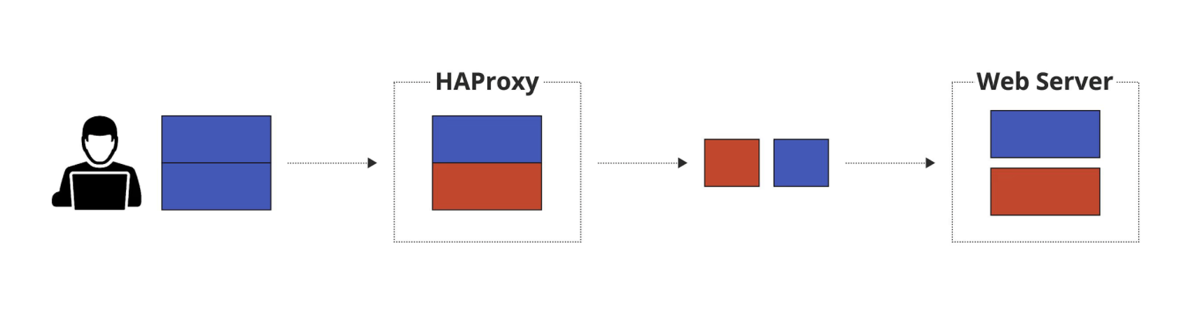 HTTP request smuggling with HAProxy
HTTP request smuggling with HAProxy
Preceded by an explanation of HAProxy’s twin phases for handling HTTP request logic, the researchers’ detailed a bypass of security controls in which “HAProxy is only aware of a single HTTP request being forwarded and thus only returns a single HTTP response (the first) from the backend server back to the client”.
Subsequently they explained how to also receive the HTTP response for the smuggled request by sending two consecutive requests.
The research duo then outlined a potential means of automating discovery of the flaw and similar integer overflow vulnerabilities.
Updates and workaround
The vulnerability was fixed in HAProxy versions 2.0.25, 2.2.17, 2.3.14, and 2.4.4 by adding size checks for the name and value lengths.
Hollander and Peles provided a workaround for users unable to immediately apply updates that reconfigures HAProxy in such a way that “should mitigate all variants of this attack that we’ve encountered”.
Request smuggling revitalized
The venerable request smuggling technique was developed further last month when James Kettle, head of research at PortSwigger Web Security (The Daily Swig’s parent company) showcased his exploits targeting HTTP/2 infrastructure at Black Hat USA 2021.
Kettle, whose 2019 Black Hat presentation also focused on HTTP request smuggling, fashioned desynchronization attacks that saw him steal secrets from websites running Amazon’s Application Load Balancer, poison every page on Bitbucket, and force Atlassian to universally sign users out of Jira.
Catch up on the latest hacking techniques
A novel alternative to HTTP request smuggling was recognized as 2020’s top web hacking technique by Kettle’s employer.
Unveiled by Bishop Fox researchers in September, HTTP/2 cleartext (H2C) smuggling “abuses H2C-unaware front-ends to create a tunnel to backend systems, enabling attackers to bypass frontend rewrite rules and exploit internal HTTP headers,” said Kettle in summarizing the winning entry’s impact.
Attendees at Black Hat 2020, meanwhile, were treated to a quartet of novel variants of HTTP request smuggling attacks by Amit Klein, vice president of security research at SafeBreach.
RELATED HTTP request smuggling vulnerability in Apache Tomcat ‘has been present since 2015’
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·