A new variant of AsyncRAT malware dubbed HotRat is being distributed via free, pirated versions of popular software and utilities such as video games, image and sound editing software, and Microsoft Office.
"HotRat malware equips attackers with a wide array of capabilities, such as stealing login credentials, cryptocurrency wallets, screen capturing, keylogging, installing more malware, and gaining access to or altering clipboard data," Avast security researcher Martin a Milánek said.
The Czech cybersecurity firm said the trojan has been prevalent in the wild since at least in October 2022, with a majority of the infections concentrated in Thailand, Guyana, Libya, Suriname, Mali, Pakistan, Cambodia, South Africa, and India.
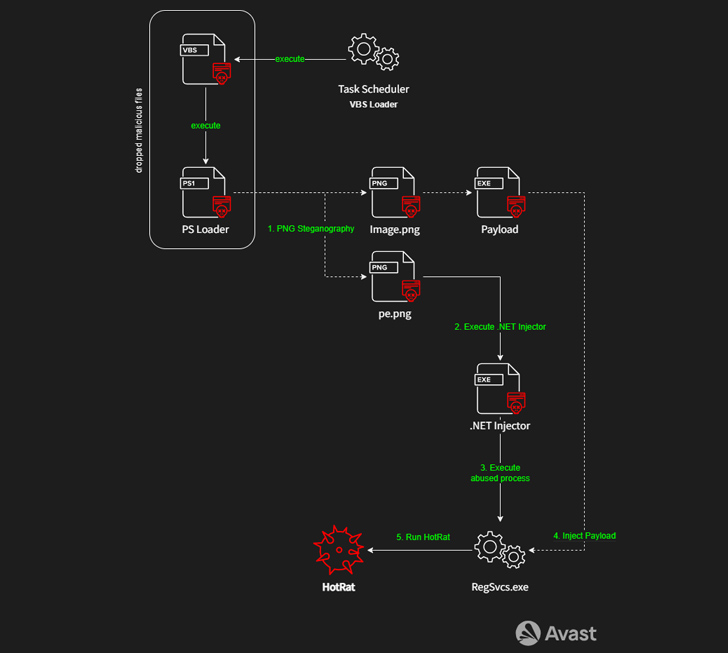
The attacks entail bundling the cracked software available online via torrent sites with a malicious AutoHotkey (AHK) script that initiates an infection chain designed to deactivate antivirus solutions on the compromised host and ultimately launch the HotRat payload using a Visual Basic Script loader.
UPCOMING WEBINARShield Against Insider Threats: Master SaaS Security Posture Management
Worried about insider threats? We've got you covered! Join this webinar to explore practical strategies and the secrets of proactive security with SaaS Security Posture Management.
Join TodayHotRat, described as a comprehensive RAT malware, comes with nearly 20 commands, each of which executes a .NET module retrieved from a remote server, allowing the threat actors behind the campaign to extend its features as and when required.
That said, it's worth noting that the attack requires administrative privileges to successfully realize its goals.
"Despite the substantial risks involved, the irresistible temptation to acquire high-quality software at no cost persists, leading many people to download illegal software," Milánek said. "Therefore, distributing such software remains an effective method for widely spreading malware."
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.
.png)
 1 year ago
93
1 year ago
93 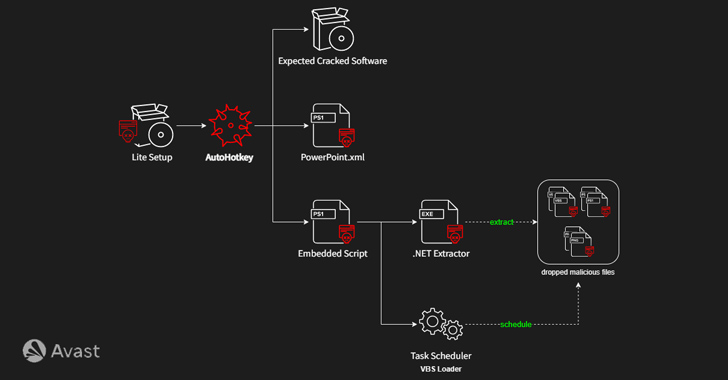















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·