BOOK THIS SPACE FOR AD
ARTICLE ADThe Elasticsearch database was left exposed without any security authentication which means it could have been accessed by anyone with access to a web browser, and a valid URL.
Comparitech researchers published a report revealing details of an unprotected marketing database that leaked private details of about 35 million residents across Chicago, San Diego, and Los Angeles. Interestingly, the owner of this database hasn’t yet been identified.
SEE: Hacker dumps sensitive household records of 250M Americans
Reportedly, the Elasticsearch database wasn’t protected by a password, which is why it could have been accessed by anyone with access to a web browser, and a valid URL. The database was discovered by Bob Diachenko, head of Comparitech’s cybersecurity research team, on 26 June 2021.
Amazon Took Down the Database
Diachenko suspects that this database could be a marketing firm’s scraping attempt, and the company stored it on a misconfigured server.
Since the exposed database’s owner couldn’t be discerned, and it remained accessible until 27 July 2021, Amazon Web Services (AWS), which hosted the server where the database was stored, had to intervene and take it down to prevent it from landing in the wrong hands.
However, it is pretty discomforting that it remained exposed for about a month, which was ample time for cybercriminals. Its time zone was set to Kolkata, India.
About the Exposed Data
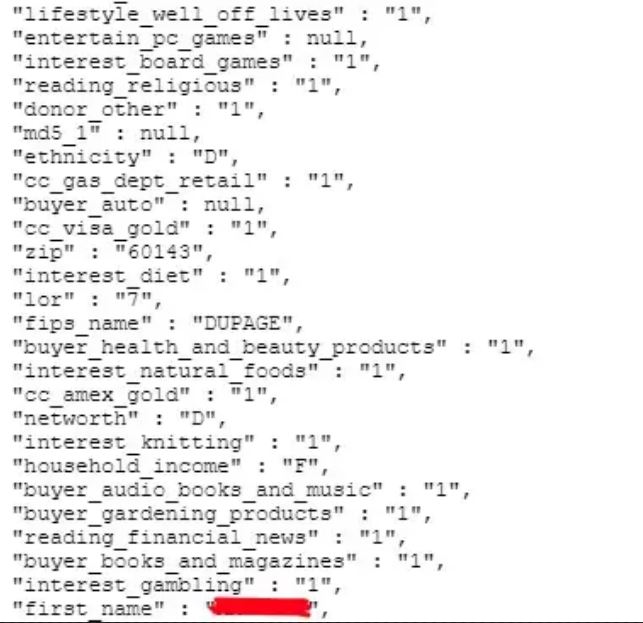
The exposed database contained:
Gender Full names Ethnicities Date of birth Marital status Email addresses Contact information Residential addresses.Furthermore, the information contained other exploitable demographic information such as:
Assets Shopping habits Media preferences Pet ownership details Hobbies and interests Estimated income, and net worth.According to Comparitech’s report, the data was gathered between 2010 and May 2021, and hence, contained many recent records.
It is unfortunate that this sort of information is highly personal and could be used by threat actors to launch spam and scam campaigns as well as phishing attacks, as each entry contained 268 fields of information. Therefore, this is a treasure trove of personal data for cybercriminals.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·