BOOK THIS SPACE FOR AD
ARTICLE ADAssalamualaikum Bug Hunter & All Friends.
How are you?
I hope you’re okay.

In this article I found 2 XSS STORED vulnerabilities on the platform which I can’t name, because they don’t want to be mentioned in this article.
I originally discovered this vulnerability on 12th May 2021 when I accidentally tried to download the application to spare my time.
At that time there were a lot of features there, and I tried to find gaps in the application. And I also think that I’m unlikely to find a vulnerability in a well-known app, because I’m just a Senior High School graduate in the area where I live. And I also do not have a major related to IT Security, in fact I never took IT lessons when I was in school. And I also only do testing via cellphone.
When I tried to search for vulnerabilities in the app, I found a linked feature on the website as well. Then I tried to enter the payload :
“><img src=x onerror=prompt(document.domain)>
Then I tried to open it in the browser, and a pop up appeared.
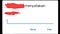
(Sorry my screenshots are censored, because I’m not allowed to show uncensored screenshots).
Then I tried to report it to the security team of the application.
Shortly after writing a report via email to them, and they replied to my email. And I was asked to send details of the vulnerability.
After I finished sending them the vulnerability details, then I thought of looking for it again.
Then I tried to check what features are connected to the website. Until finally I rediscovered the feature that is connected to the website.
In this step I still use the same method as before, which is to enter the payload :
"><img src=x onerror=prompt(document.domain)>
Then open it in the browser, and the pop up appears again :D
then, I reported it again to them via email. And no need to wait long, they immediately reply to emails. And both of my reports are being verified.
Shortly after, they emailed me that the vulnerability was valid, and was at MEDIUM risk.
I was confused why it was MEDIUM, and then I asked them that.
And they also challenged me on how to make it a HIGH impact.
And of course I’m challenged :D
Then I tried to find the account login feature via the browser. Then I tried to login, and booms, the account was successfully logged in via the browser.
Then I thought maybe this could create a potentially HIGH vulnerability. Because if a user logs in to an account, and sees the contents in the content that is included in the XSS payload, then he will be affected.
Then I tried to give the scenario to the Application Security team. And they accept it, so the vulnerability impact is changed from Medium to HIGH.

After a few months, they contacted me, and I was given a bounty.
Report 1: $600.00
Report 2: $700.00
Total $1300.00

Timeline :
Report : 12/05/2021
Valid Medium : 12/05/2021
Change Medium To HIGH : 13/05/2021
Rewards : $1300.00
.png)
 3 years ago
168
3 years ago
168 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·