BOOK THIS SPACE FOR AD
ARTICLE ADHello Guys! I am a part-time bug hunter at Bugcrowd and I will share how I found a Blind SQL INJECTION manually just by browsing and checking http history in BURPSUITE.
So basically, I was Invited to a private program on Bugcrowd. That site was based on Laravel Framework and I thought they might be using MYSQL DATABASE. So I decided to test Blind SQL INJECTION on that site.
I manually browsed all the URLS and they were getting collected in BURPSUITE HTTP HISTORY. I found a unique POST request which weren’t normally available. So I suddenly remembered that sometimes manually browsing can get you unique URLS if you use a PROXY like Burpsuite, I read it in WEB APPLICATION HACKER HANDBOOK.
I found many parameters in that POST request and I started checking those parameters with this payload
‘XOR(if(now()=sysdate(),sleep(5*1),0))OR’
And to my surprise, It worked and slept for 5 seconds. I immediately copied the request and used SQLMAP on that.
I used different SQLMAP command but a firewall was blocking me for the fetching current database.
I then launched this command
sqlmap.py -r request.txt -p “value” -v 3 — level=5 — risk=3 — time-sec=15 — tamper=between — current-db — no-cast
and guess what?
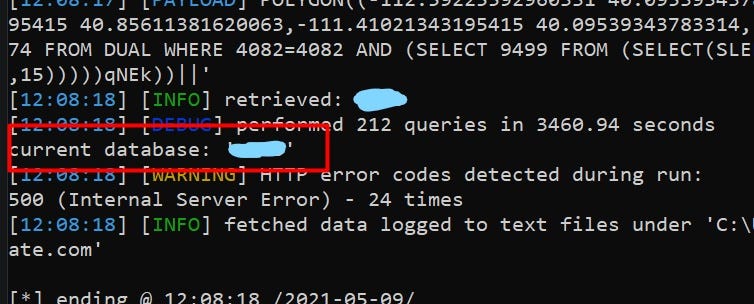
I was able to retrieve the current database name.
Takeaways
Always check each and every request which you think might be querying with database and check SQL INJECTION there with manual testing and fuzzing and check those response carefully.
Thank you for reading!
.png)
 3 years ago
174
3 years ago
174 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·