BOOK THIS SPACE FOR AD
ARTICLE ADHi guys ,
This is Nazmul Haque a Newbie security researcher from Bangladesh.This is my 1st write-up and also I am not good at XSS so forgive all mistakes.
It was 11/18/2019 and my 1st day of bug hunting.I’m still newbie!
Today I am gonna to Share a Stored Xss vulnerability what was reported by me to Badoo Security team in their Bug Bounty Program in Hackerone.
So as usual i was created an account in Badoo and Visit a user profile and send message with xss payload.
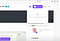
So I input a Normal payload :-
“><img src=x onerror=prompt(document.cookie)>
After message sent successfully i clicked on chat now option and i got this Response.
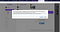
I reported this issue in NOV 18th. Report Triaged within 2 Hour and they paid me 1000$ for reporting this within 6 hour.

Video POC: https://www.youtube.com/watch?v=RgGz2z5bFBk
Thanks for reading . Happy Hunting .
Twitter: Nazmul Haque
Facebook: Nazmul Haque
LinkedIn: Nazmul Haque
.png)
 4 years ago
189
4 years ago
189 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·