BOOK THIS SPACE FOR AD
ARTICLE ADHey fellows!
This is my first write-up in 2020, Which about a recently Bugs found in a random BugBounty program, hope you enjoy it and increase your knowledge with one of my methodologies. :3
Note: I don’t like to mention the company name or even any related information about the company, cause the company don’t want to disclosing bugs that found by Security Researchers 😬, So I just use redacted.com or redacted company instead of real name!.
let’s start and stop wasting time 😅…
As all researchers doing at the first time of researching, I just started to check subdomains (sometimes there is critical bugs in hidden directories in subdomains!), I just used aquatone tool for finding subdomains, I know there is many tools for doing it but aquatone is better than most of them, this tool collects and gives subdomains and also gives available subdomains and also checks them for Subdomain TakeOver.
Use this command after installing aquatone tool
aquatone-discover -d sitetarget.com
Download aquatone in Github
https://github.com/michenriksen/aquatone
And also download some tools for Subdomain finder and subdomain Enumerating:
1- Sublist3r > https://github.com/aboul3la/Sublist3r
2- assetfinder > https://github.com/tomnomnom/assetfinder
3- Knockpy > https://github.com/guelfoweb/knock
Or some online tools:
1- https://www.nmmapper.com/sys/tools/subdomainfinder
2- https://spyse.com/tools/subdomain-finder
after finishing of aquatone I got 50+ subdomains which most of them were active on the website.
then I chose one of them and focused on it and made it my primary target, as always I use my all methodologies on the selected target, the first thing to do is Dorking via Google Search and DuckDuckGo, so I just searched with this keyword:
site:subdomain.redacted.com

just for your info, we can find directories, files, parameters, on the websites via Google Searching or other websites for search engines with random keywords such as:
site:example.com admin
site:example.com login
site:example.com key
site:example.com log
site:example.com php or site:example.com html
site:example.com id=
or just random numbers
site:example.com 1
site:example.com 2020
so I found an endpoint with that showing page:

so the first thing I tried was XSS, I tried this XSS payload “><svg/onload=alert(document.domain)> and an alert excused.
I reported it directly to the Company and after a few hours they replied me and rewarded me with a 150$ Bounty, and the story beginning in here 😋.
After a few hours waiting for fixing this bug, I visited the directory and I found out that the bug had been fixed by the company security team, and tried some XSS payloads for bypassing the filter, but it was useless and couldn’t get any result with it, so I opened BurpSuite tool and just reloaded the page again, Then I got the request and sent it to the Scanner and minimized it then tried some other ways to find other bugs, but after a few minutes I just maximized the Burp and Shocked 😐 The Burp found an SQLi bug, I opened an Terminal and used SQLmap tool for automatic injecting the database, using this command:
sqlmap — wizard
and entered the Vulnerable URL
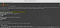
I could inject the main website database and made it as a PoC then reported it to the website security team and they replied within 5–15 minutes!

So I got (150$ for Reflected XSS) and (300$ for SQLi) = 450$😉
My remediation for you guys is “check again and gain again”.
Thanks for reading it!
.png)
 4 years ago
191
4 years ago
191 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·