BOOK THIS SPACE FOR AD
ARTICLE AD
Hewlett Packard Enterprise (HPE) is investigating a potential new breach after a threat actor put allegedly stolen data up for sale on a hacking forum, claiming it contains HPE credentials and other sensitive information.
The company has told BleepingComputer that they have not found any evidence of a security breach and no ransom has been requested, but it's investigating the threat actor's claims.
"We are aware of the claims and are investigating their veracity," HPE's Sr. Director for Global Communications Adam R. Bauer told BleepingComputer on Thursday.
"At this time we have not found evidence of an intrusion, nor any impact to HPE products or services. There has not been an extortion attempt."
When asked to provide additional details regarding the company's ongoing investigation, Bauer said they had "nothing new to share."
IntelBroker, the threat actor selling the alleged HPE data, shared screenshots of some of the supposedly stolen HPE credentials but has yet to disclose the source of the information or the method used to obtain it.
"Today, I am selling the data I have taken from Hewlett Packard Enterprise," the threat actor says in a post on the hacking forum.
"More specifically, the data includes: CI/CD access , System logs , Config Files , Access Tokens , HPE StoreOnce Files (Serial numbers warrant etc) & Access passwords. (Email services are also included)."
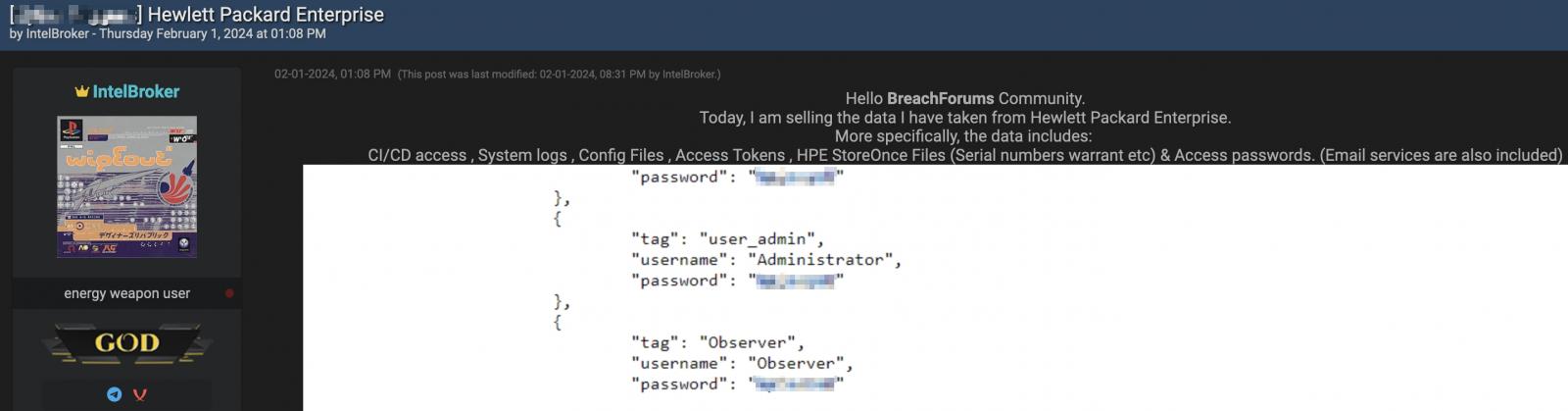 IntelBroker selling allegedly stolen HPE credentials (BleepingComputer)
IntelBroker selling allegedly stolen HPE credentials (BleepingComputer)IntelBroker is best known for the breach of DC Health Link, which led to a congressional hearing after it exposed the personal data of U.S. House of Representatives members and staff.
Other cybersecurity incidents linked to IntelBroker are the breach of the Weee! grocery service and an alleged breach of General Electric Aviation.
Russian hackers breach HPE corporate email accounts
This investigation comes after HPE disclosed two weeks ago that the company's Microsoft Office 365 email environment was breached in May 2023 by hackers the company believed to be part of the Russian APT29 hacking group linked to Russia's Foreign Intelligence Service (SVR).
The company said the Russian hackers stole SharePoint files and data from its cybersecurity team and other departments and maintained access to its cloud infrastructure until December when HPE was again alerted of a breach of its cloud-based email environment.
"On December 12, 2023, HPE was notified that a suspected nation-state actor had gained unauthorized access to the company's Office 365 email environment. HPE immediately activated cyber response protocols to begin an investigation, remediate the incident, and eradicate the activity," HPE told BleepingComputer.
"Through that investigation, which remains ongoing, we determined that this nation-state actor accessed and exfiltrated data beginning in May 2023 from a small percentage of HPE mailboxes belonging to individuals in our cybersecurity, go-to-market, business segments, and other functions."
Days before HPE's Russian hack disclosure, Microsoft revealed a similar breach where APT29 breached some of its corporate email accounts belonging to its leadership team and employees in the cybersecurity and legal departments.
Microsoft later shared that the threat actors gained access to the corporate email accounts after hacking into a misconfigured test tenant account by brute forcing its password in a "password spraying" attack.
HPE was also breached in 2018 when APT10 Chinese hackers also hacked into IBM's networks and used the access to hack into their customers' devices.
More recently, HPE disclosed in 2021 that data repositories of its Aruba Central network monitoring platform were compromised, enabling attackers to access data about monitored devices and their locations.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·