BOOK THIS SPACE FOR AD
ARTICLE AD
A smishing (SMS phishing) campaign is targeting iMessage users, attempting to socially engineer them into bypassing Apple’s built in phishing protection.
For months, iMessage users have been posting examples online of how phishers are trying to get around this protection. And, now, the campign is gaining traction, according to our friends at BleepingComputer.
It works like this: Under normal circumstances, iMessage will disable all links in messages from unknown senders to protect the user against clicking them by accident. However, if a user replies to a message or adds the sender to their contact list, the links are enabled, allowing the person to click on the link.
The text of the messages comes in all the variations that phishers love to use:
Undeliverable packages from USPS, EVRI, Royal Mail, DHL, Fedex, etc. Unpaid road toll. Owed shipping fees. Other outstanding payments that you are unaware of.But they all end in a similar way to this:
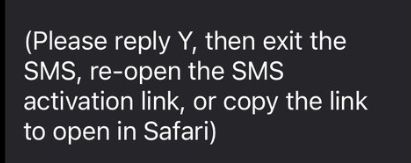
“(Please reply Y, then exit the SMS, re-open the SMS activation link, or copy the link to open in Safari)”
Replying with Y (or actually anything) will enable the links and turn off iMessage’s built-in phishing protection. Clicking the link will then lead the recipient to whatever malicious website the phisher had in mind. Even if the user just replies with “Y” and then decides not to follow the link—because it looks slightly off—the phishers will know that they have found a likely target for more attacks.
It’s also important to know that there are similar instructions for the Chrome browser:
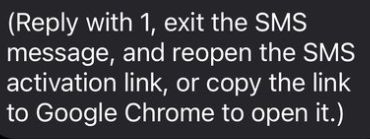
“Reply with 1, exit the SMS message, and reopen the SMS activation link, or copy the link to Google Chrome to open it.)”
How to avoid smishing scams
Never reply to suspicious messages, even if it’s only a “Y” or “1.” It will tell the phishers they have a live number and they will bombard you with more attempts. Never add a number you don’t know to your Contacts as that will disable the iMessage protection as well. Don’t assume any message is the real deal. If you’re being asked to do something, contact the company directly via a known method you trust. If it turns out to be a fake, you should be able to report it to them, there and then. If you live somewhere with a Do Not Call list or spam reporting service, make full use of it. Report bogus messages and numbers. Your mobile device may already have some form of “safe” message ID enabled without you knowing. It’s tricky to give specific advice here because of the sheer difference of options available on models of phone, but the Options / Safety / Security / Privacy menus are a good place to start. Check the link before you click it or copy it in your browser. Is it exactly what you would expect it to be? Scammers often use typosquatting techniques (for example evri[.]top instead of the legitimate evri[.]com, or they fabricate a link that uses the subdomain to make it look legitimate (for example usps.com-track.infoam[.]xyz). If it doesn’t look real then don’t click on it. If a message sounds too good (or bad) to be true, it probably is.We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·