BOOK THIS SPACE FOR AD
ARTICLE AD
An almost 6-year-old vulnerability in the Lighttpd web server used in Baseboard Management Controllers has been overlooked by many device vendors, including Intel and Lenovo.
The security issue could lead to the exfiltration of process memory addresses, which could help attackers bypass protection mechanisms like Address Space Layout Randomization (ASLR).
Lighttpd is an open-source web server known for being lightweight, fast, and efficient, making it ideal for high-traffic websites while consuming minimal system resources.
During recent scans of Baseboard Management Controllers (BMC), researchers at Binarly firmware security firm discovered a remotely exploitable heap out-of-bounds (OOB) read vulnerability through the Lighttpd web server processing "folded" HTTP request headers.
Although the vulnerability was addressed in August 2018, the maintainers of Lighthttpd patched it silently in version 1.4.51 without assigning a tracking ID (CVE).
This led the developers of AMI MegaRAC BMC to miss the fix and fail to integrate it into the product. The vulnerability thus trickled down the supply chain to system vendors and their customers.
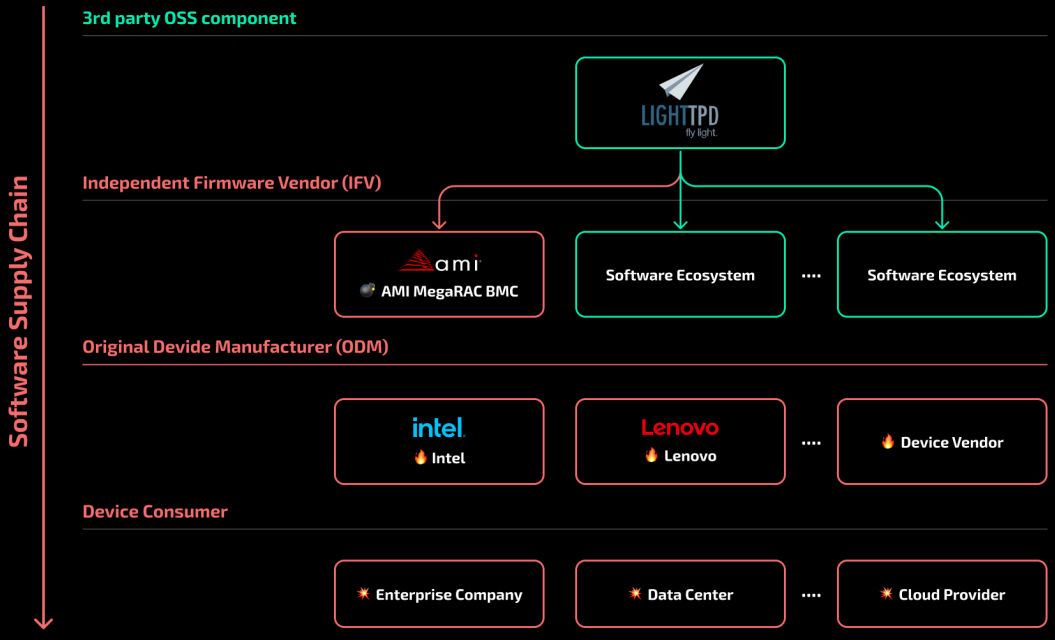 Lighttpd vulnerability falling through the supply chain
Lighttpd vulnerability falling through the supply chainSource: Binarly
Impact and status
BMCs are microcontrollers embedded on server-grade motherboards, including systems used in data centers and cloud environments, that enable remote management, rebooting, monitoring, and firmware updating on the device.
Binarly found that AMI failed to apply the Lighttpd fix from 2019 until 2023, leading to the roll-out of a large number of devices vulnerable to the remotely exploitable bug throughout these years.
"According to Binarly Transparency Platform data, we see multiple products from Intel, Lenovo, and Supermicro are impacted," Binarly told BleepingComputer.
"Based on our data, nearly 2000+ devices are impacted in the field. In reality, this number is even bigger."
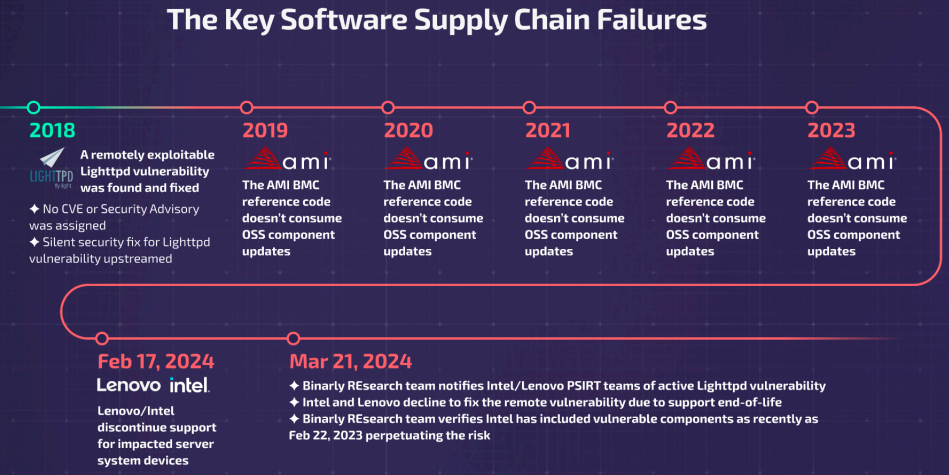 Timeline of an unfixed flaw
Timeline of an unfixed flawSource: Binarly
The threat analysts assigned three internal identifiers to the Lighttpd vulnerability based on its impact on different vendors and devices:
BRLY-2024-002: Specific vulnerability in Lighttpd version 1.4.45 used in Intel's M70KLP series firmware version 01.04.0030 (latest), impacting certain Intel server models. BRLY-2024-003: Specific vulnerability in Lighttpd version 1.4.35 within Lenovo BMC firmware version 2.88.58 (latest) used in Lenovo server models HX3710, HX3710-F, and HX2710-E. BRLY-2024-004: General vulnerability in Lighttpd web server versions before 1.4.51, allowing sensitive data reading from the server's process memory.Among the vendors with impacted devices are Intel and Lenovo, who Binarly notified of the problem in their devices. The firmware security company notes some Intel systems released as recently as February 22, 2023, include the vulnerable component.
However, both vendors said the impacted models had reached end-of-life (EOL) and no longer receive security updates, meaning that they will likely remain vulnerable until decommissioned.
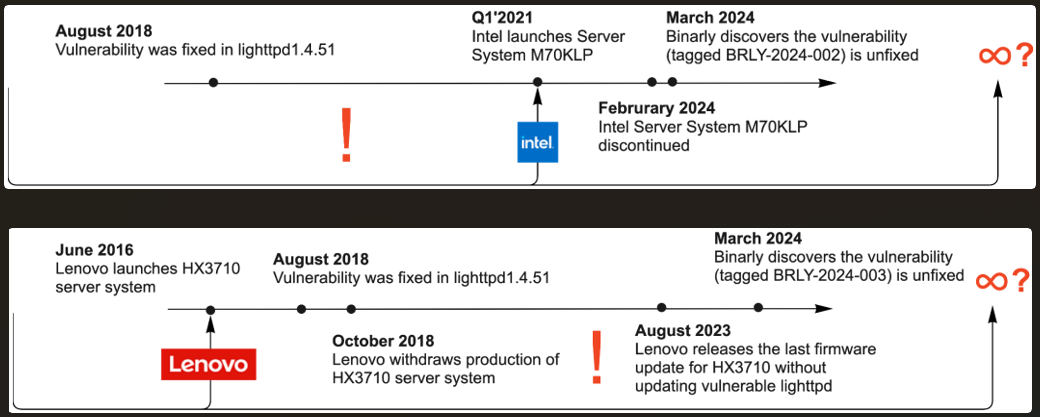 Vendor impact (Intel top, Lenovo bottom)
Vendor impact (Intel top, Lenovo bottom)Source: Binarly
According to Binarly, there is a "massive number" of vulnerable and publicly available BMC devices that have reached end-of-life and will remain vulnerable forever due to the lack of patches.
Binarly's report provides technical details about the vulnerability and how it works, which could allow an attacker to develop an exploit. The researchers note that this is another example of gaps in the firmware supply chain that introduce security risks that could extend over several years.
Lack of transparency and failing to raise awareness about the vulnerability from the Lighttpd maintainers also adds to the problem, leading to vendors failing to integrate the necessary fixes in due time.
.png)














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·