BOOK THIS SPACE FOR AD
ARTICLE AD
While doing the Reconnaissance for BugBounty/Web application penetration testing, we often spend most of our time doing repetitive tasks for multiple targets. On top of that, keeping track of all the scan results is a huge pain.
If you do bug bounty or web application penetration testing, you might have found yourself stuck in the position where you want to revisit the bug bounty program and want to go through the older recon results; chances are that:
You may not have stored the scan resultsscan results are not organizedsearching through them is a significant painMoreover, if you observe, when you do recon, for most of the targets, you follow the same methodology to perform recon. All of these kinds of stuff can be automated into a framework.
Suppose if you are doing recon on redacted.com, you might have encountered a situation like this, “I want to search the subdomain which has page title “Dashboard” and has page status as 200 and quickly want to have a look at the screenshot.” Currently, there is no other framework that does this effectively.
This is when reNgine comes into play. reNgine is an automated reconnaissance framework meant for gathering information during penetration testing of web applications. reNgine has customizable scan engines, which can be used to scan the websites, endpoints, and gather information and store them in an organized fashion.
The beauty of reNgine is that it has configurable scan engines, you can configure the scan engines and use it against multiple targets.


reEngine automates the entire pipeline of recon based on the scan engine you have defined and organizes the results for quick search and identify your potential target with minimal efforts. This is how the scan results look like:

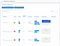
Using this dashboard, you can quickly search your subdomains against, HTTP status, ports, content length, page title, technology, directory or filename, or just everything! You can search for all subdomain that uses React as technology, and quickly see their screenshot, without the need to visit the page.
Search all subdomains that has http status 404
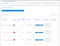
You saw how quickly it was to search the subdomains using almost anything and instantly identify them using screenshots.
Similarly, it does the same thing for endpoints as well. reNgine uses existing open-source tools to gather endpoints from various sources like common crawl, Wayback engine, and uses a web crawler to gather more endpoints. It then runs a quick HTTP probe to check for alive URLs and makes it easy for you to filter out.

reNgine makes it extremely helpful in the situation when you want to find an open redirection, in most of the open redirection, the common thing is =http. so if you are looking for open redirection, you can quickly search =http and check against their HTTP status as 30X, chances are that you have found an easy-open redirection.

reNgine can do a lot more than this
Search all the URLs using file extensions
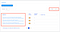
The other cool thing about reNgine is that you can configure to send yourself or your dev team a quick scan notification and results when the the scan is complete.

The future versions of reNgine will include many exciting features like custom scripting, a more detailed and thorough scan, faster scan, and improved dashboard.
Today, we announce the first version of reNgine. A powerful recon engine framework.
This is how reNgine works.

reNgine is definitely worth giving a try. Make sure to star the project on GitHub!
Github: https://github.com/yogeshojha/rengine
Developer: https://yogeshojha.com/
Twitter: https://twitter.com/ojhayogesh11
.png)
 4 years ago
230
4 years ago
230 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·