BOOK THIS SPACE FOR AD
ARTICLE AD
Data-wiping attacks are becoming more frequent on Israeli computers as researchers discovered variants of the BiBi malware family that destroys data on both Linux and Windows systems.
A Linux version of the BiBi wiper was seen in late October by researchers at cybersecurity companies ESET and SecurityJoes, who noted that it was launched by pro-Hamas hacktivists.
Over the weekend Israel's CERT published an alert with rules that could help organizations identify or prevent the threat actors' activity.
The agency recommends organizations to use the provided identifiers for all corporate security systems (e.g. security information and event management - SIEM, Endpoint Detection and Response (EDR), and antivirus).
The government also asks companies to inform the national cyber system if they find one or more identifiers on the corporate hosts.
Wiper malware disables recovery options
'BiBi-Linux' was discovered by the Security Joes' Incident Response team, who reported on October 30 that it was likely deployed by pro-Hamas hacktivists to cause irreversible data corruption and operational disruption.
ESET researchers announced the next day that they discovered the Windows variant of the malware being deployed by a Hamas-backed hacktivist group they track as BiBiGun.
The malware achieves its goal by simply overwriting files and there is no data exfiltration, encryption, or a ransom demand involved.
On Friday, BlackBerry's threat intelligence team published a technical analysis of the Windows variant for the BiBi-Linux malware. The researchers found the variant a day after SecurityJoes posted their findings on the new Linux wiper.
The malware is packed in a small 203KB 64-bit executable. When launched, it profiles the host's processor to determine the number of threads it can leverage for fast data-wiping attacks, supporting up to 12 threads on eight cores. A similar multi-thread and queuing logic was seen in the Linux variant.
According to the researchers, the threat actor used the simple right-to-left technique to bypass pattern detection rules that are common in legacy antivirus products.
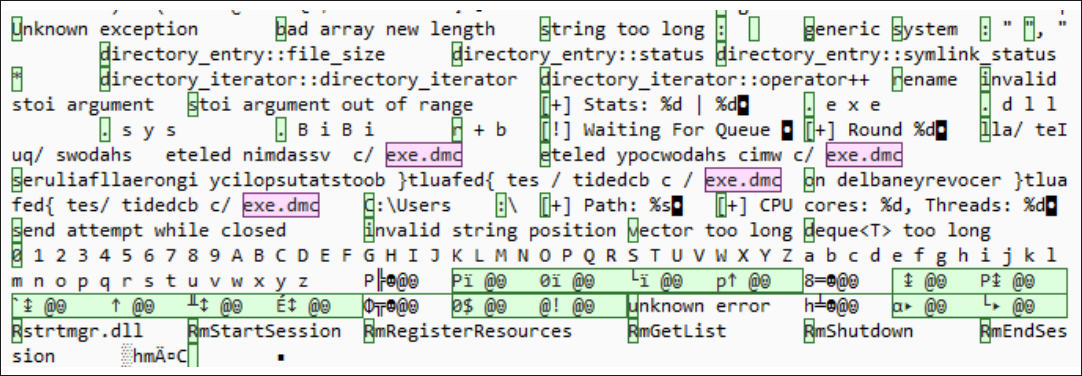 BiBi's commands stored in reverse writing order to evade detection (BlackBerry)
BiBi's commands stored in reverse writing order to evade detection (BlackBerry)BiBi for Windows targets all file types except for .EXE, .DLL, and .SYS files, likely because destroying them would render the computer unusable, and the hacktivists wouldn't be able to relay their message.
The targeted files have their content overwritten with random bytes to make them unrecoverable, and are renamed using a ten-character long sequence of random letters followed by an alphanumerical extension containing the "BiBi" string.
For example, a file originally named "document.txt" might be renamed to "asdzxcqwer.BiBi3" after the malware attack.
This process is unpredictable, obscuring the original filenames and further complicating data recovery efforts.
To prevent easy system restoration, the malware also deletes the shadow copies that hold system snapshots from an earlier state and are often used to recover data and settings.
Additionally, BiBi turns off the 'Error Recovery' mode on system boot and deactivates the 'Windows Recovery' feature.
BlackBerry says that the initial infection vector remains unknown at the time.
Security Joes posted a new, more comprehensive report late last week, looking deeper into the campaign and the Karma hacktivist group responsible for its orchestration.
The report presents some overlaps of Karma with previously known Iranian hacktivist groups such as 'Moses Staff,' previously known for launching ransom-less data encrypting attacks.
SecurityJoes and BlackBerry provide YARA rules [1, 2] for detecting the two currently known variants of the BiBi wiper along with hashes for the two executables. Another set of identifiers [TXT, CVS] for the BiBi threat activity is available from Israel's CERT authority.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·